Remotely accessing your home lab can be a challenging task, whether you need to access your NAS or a combination of physical and cloud servers. You could set up a VPN or maybe a reverse proxy, but those have varying levels of technical know-how to accomplish. You could use Cloudflare Tunnels, but they have restrictions on the type of data you can transmit, so you'll not be able to stream from your media server.
But what you could do is set up Tailscale, which has long been a favorite of mine, but I must confess I hadn't dug into the advanced features it has until now. I've used it before to connect my devices as a peer-to-peer VPN, without the usual bottlenecks of a traditional centralized VPN system.
But it can do so much more now, even if some of the features are in beta testing, and it's a more fully-featured product as a result. Some existing features have been made even simpler to use, and as a result, I might just start using Tailscale for my whole home lab.
Related
I use Tailscale to remotely access my self-hosted services - here's how
Tailscale provides an easy way to access your home server from external networks
5 Tailscale Funnel
Expose single services to the internet via your Tailnet
Wouldn't it be cool if you could expose your home lab services to the internet one by one, while doing so safely and using easy-to-use URLs? You could use Cloudflare Tunnels but the issue with those is that they're not encrypted between your service and Cloudflare, so technically they could snoop on what's going on. I highly doubt they are unless it's a check to make sure ToS aren't being violated, but still, the thought nags at me.
Well, a Tailscale Funnel is the same thing, except it's encrypted end-to-end with WireGuard, just like any other Tailscale connection. It's also one of the easiest things to set up, even if it's setting up HTTPS certification and DNS records for you. The command is now one line in the Tailscale CLI:
tailscale funnel [port]That's it. It'll provide you with a URL on your Tailscale to share, allowing other people to access the service without needing to take any additional action beyond clicking a link. Well, and sign in, if you have authentication set up on that self-hosted app. It's really powerful, and because it stays encrypted, it is more secure than other options. Don't forget to wait a while before trying to access it, as it takes ten to fifteen minutes for Tailscale's DNS servers to propagate.
If you need more powerful features, you can set it to stay open even when the CLI is closed, or set it to a path, or as a reverse proxy, or a file, directory, or even a plain text message for testing purposes. You can specify listening on a different port if needed, and multiple mount points or parallel OpenSSH if needed.
Related
How are Cloudflare tunnels different from a VPN?
Both let you access your services remotely but they do it in very different ways.
4 Tailscale Serve
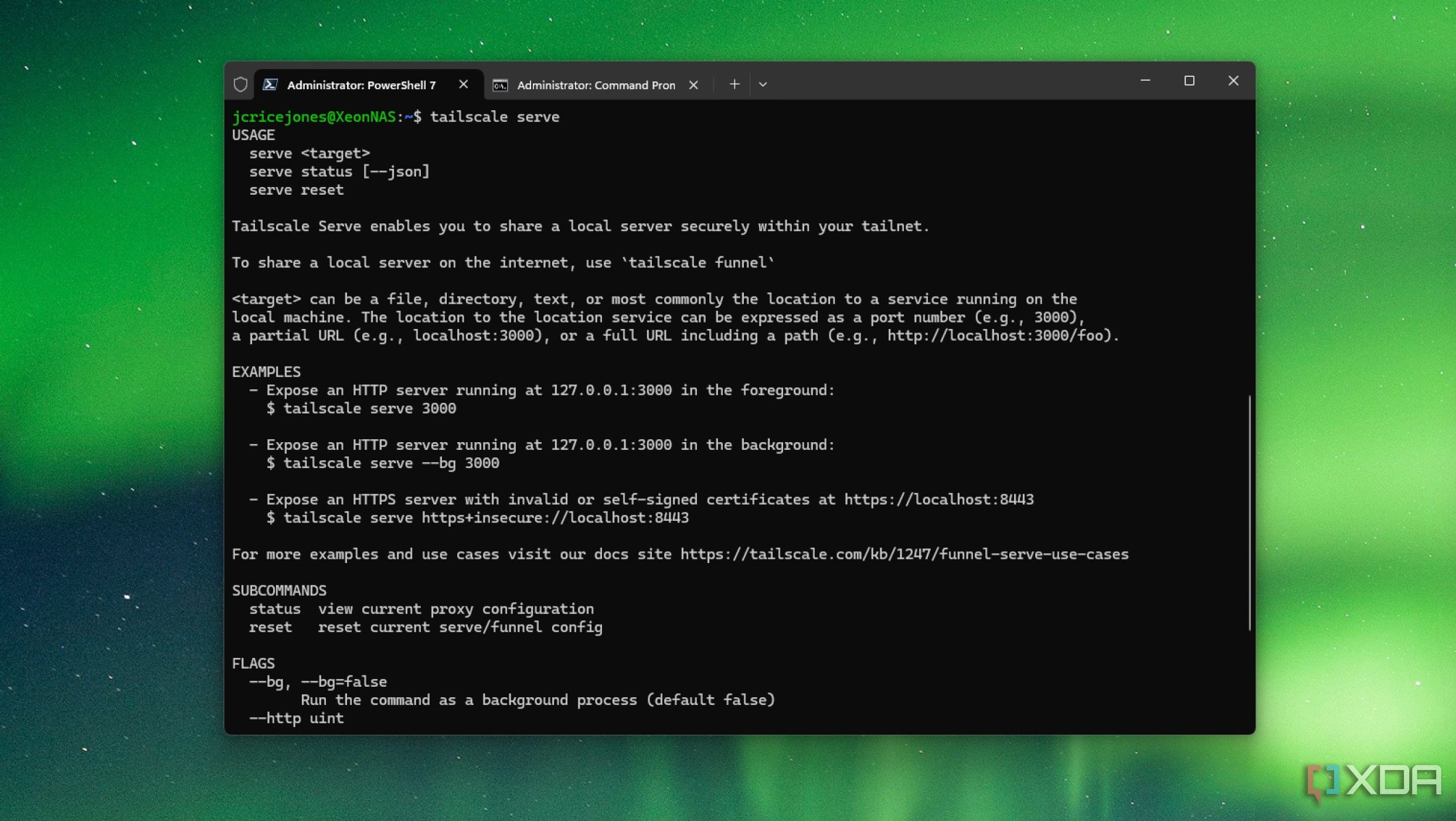
If Tailscale Funnel exposes services you control to the internet via easily used links, Tailscale Serve does the same thing, but only to the members of your tailnet. Again, no firewall tweaks are needed, and no advanced configuration is required; Tailscale handles all the hard work for you so that you can focus on testing. Whether it's a simple file server or something else, it's quickly shared to your tailnet.
Again, you only need one line in the Tailscale CLI:
tailscale serve [port]That makes the service on [port] number available on your tailnet, over HTTPS. Isn't that such an elegant solution? So you don't have to go mess around with DNS settings or domain names or mapping things manually. It just works, with one line. Static sites, development servers, anything really can be shared with this command, and you know your tailnet members, so it's already trusted users.

Related
I combined a Pi-hole with a reverse proxy for accessing my services locally, and it works perfectly
If you want to override your DNS records to have local access to your self-hosted services, this works perfectly.
3 Subnets
Expose whole LAN networks without installing Tailscale on every device
Tailscale doesn't have to be installed on every device in your tailnet. You can set up subnet routers to extend your tailnet to devices like printers that can't run the client, and then every user on your tailnet can use those services. When set up like this, it's closer to a traditional VPN where your encrypted tunnel goes to the subnet and then acts as if it is physically present, except you don't have to drop off your tailnet to do so, making it more secure, easier to deal with, and with less annoyances for the users.

Related
VLANs finally fixed my smart home headaches
I might have traded one headache for another, though...
2 Ephemeral Authentication Keys and nodes
Automatically register devices and have the keys self-destruct for cleanup
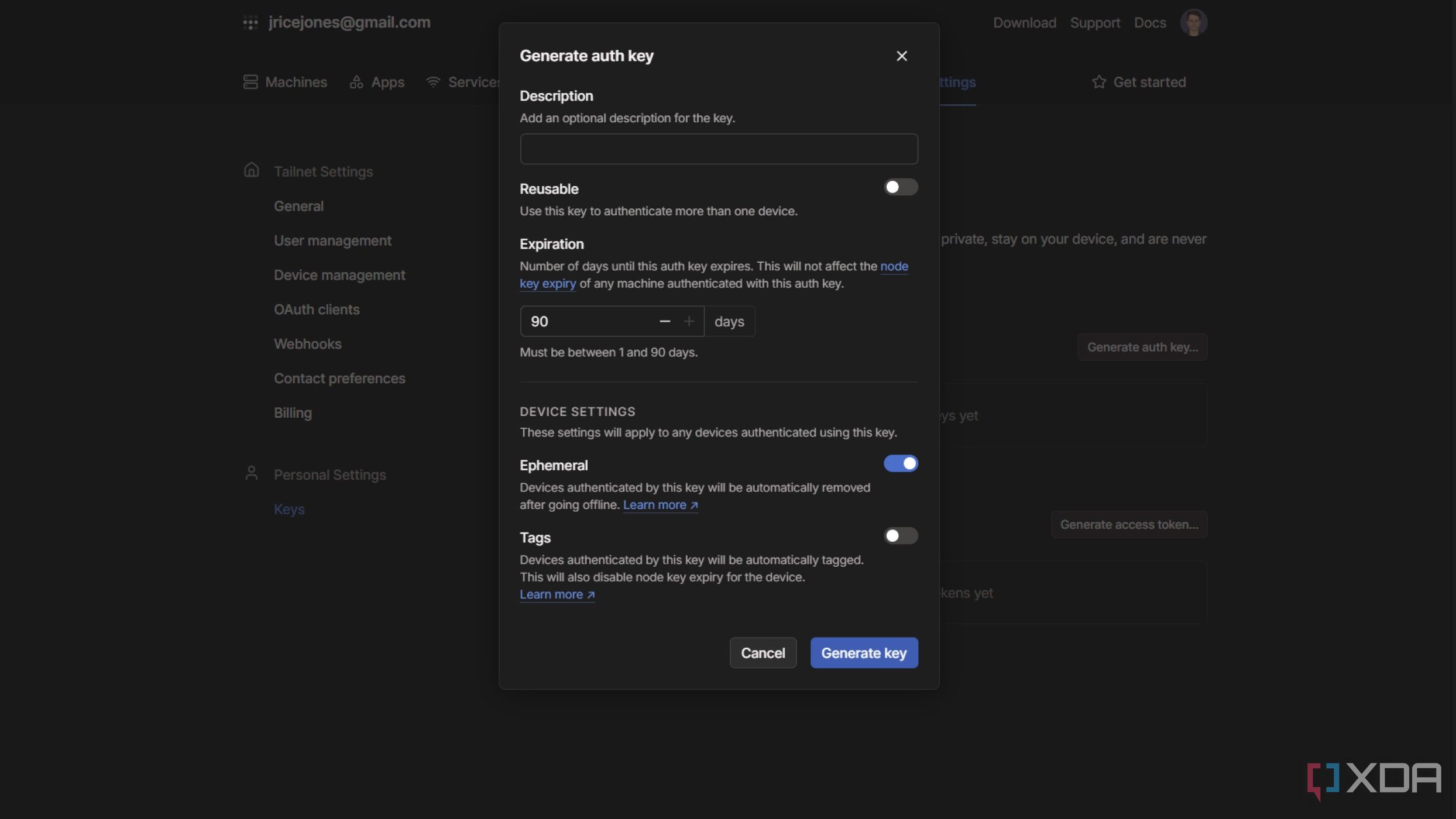
So, one thing that can be annoying about Tailscale is that the usual process for removing nodes is manual. That's okay when you have a few services or devices, but when you're using Tailscale to manage a Kubernetes cluster or three, it gets annoying — fast. After all, containers and k8s are there to be destroyed and re-upped, and once you've done that a few times, your management page is going to be rather crowded.
There's a solution, though. When creating the nodes, select the toggle next to Ephemeral and proceed as normal. That will make the key disappear like magic once the node is set up. Use a reusable key if you want multiple versions of the same container, like if you're doing HA clusters, and the other thing about ephemeral nodes is that they disappear off your management page if they're not used for ten minutes, which gives you plenty of time to bring your container down and up again without having to set new keys up, but not long enough that a disappearing container will stay in the list and confuse things.
1 Tailnet Lock
Make it so only devices you authorize can access your Tailnet
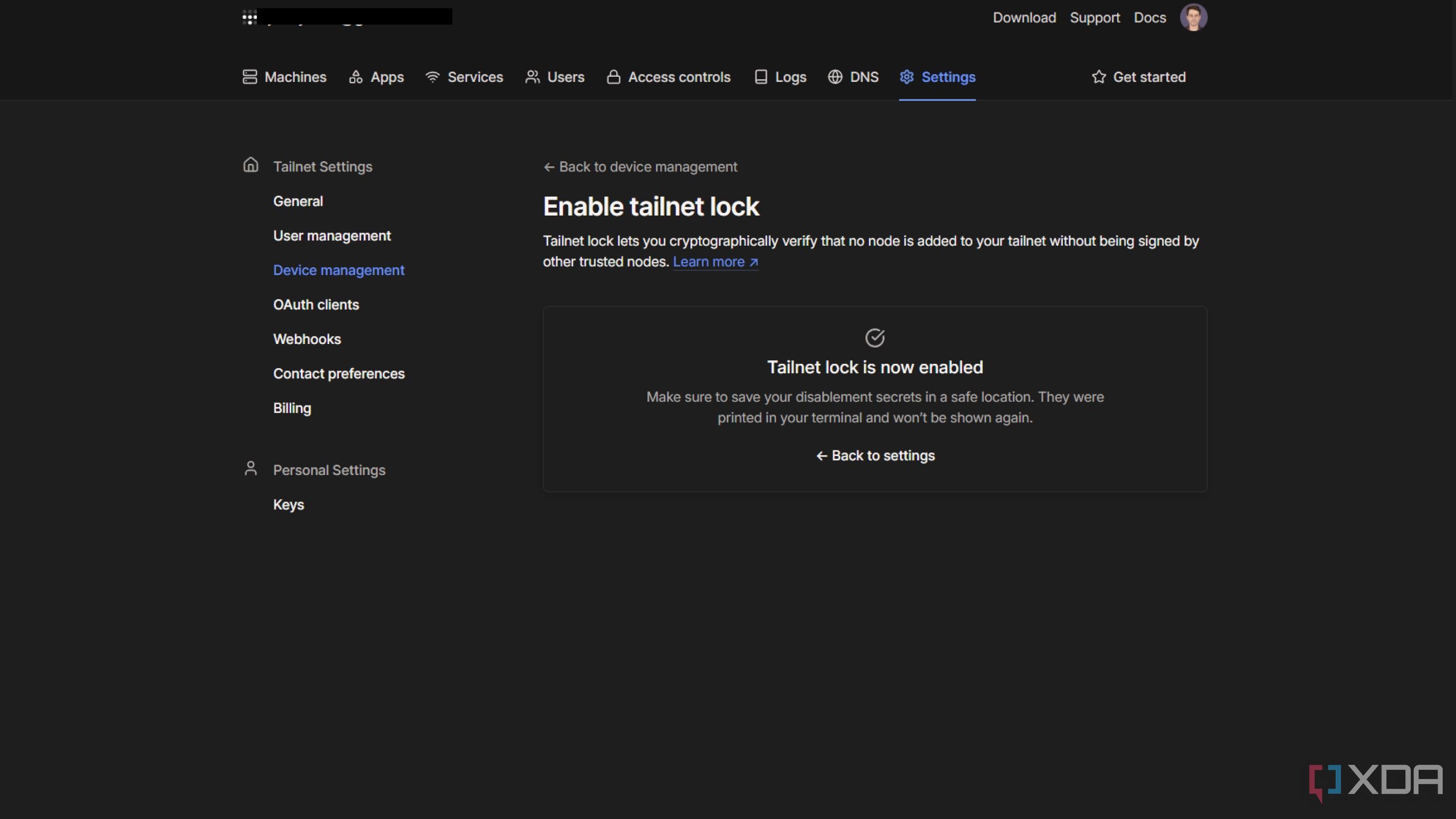
Normally, when you add new nodes to your tailnet, the Tailscale coordination server handles distributing the public keys to those peers. That's the server that Tailscale controls, not you. But you can set your tailnet to Lock, which then means peers on your tailnet handle the distribution of those keys.
It does add a little more complexity to the setup, as you need to add a Tailnet Lock key to the command when adding a new node. However, for some users, this will be welcome because it removes Tailscale as a potential threat actor. If the service did get breached, there's a chance it could add new peers to your tailnet, and see your data in plaintext. It can't do that with Tailnet Lock, and I've got it enabled just in case, more because I might forget to disconnect devices from my tailnet or stop using it.

Related
5 ways to detect and stop unauthorized devices on your home network
Nobody likes to think that unauthorized devices are using their network, but it's fairly simple to find them and kick them off.
Tailnet is far more than a mesh VPN
From robust access controls to secure service sharing, Tailscale is incredibly powerful. It's also easy to use, and it won't take long to get the hang of the concepts behind it, and how everything works. The documentation is spectacular, and I've had no issues with it in years. What service do you regularly use that you can say that about? There are tons of other things I didn't get to, like Taildrop for sending individual files across your tailnet, and with more features on the way, Tailscale is only going to get better.
.png)










 English (US) ·
English (US) ·