Every time I set up my home network again, I go through a checklist to ensure that basic security is in place. Whether it's to use the latest Wi-Fi 7 routers or to use a custom router and firewall running OPNsense, these steps lay the groundwork for what's to come.
Part of network security is also not running any potential threats on your computer. Be cautious when downloading files from unfamiliar sources, and heed any warnings that SmartScreen or your browser may display.
They're far from a complete security solution, but without these in place, it's not worth putting extra effort into securing my home network. The most obvious security holes need to be patched first, and then it's time for further refinement. These steps work whether you're hardwiring everything or putting in a mesh network, or something in between, and even if your router doesn't have some of these settings, it's worth checking because if it does, you'll be better off changing them.
6 Change the default credentials
Because why wouldn't you?
There is one step I take before any other, as the first thing done once power is plugged into the new router. It's one that I'll do before I plug a cable into the WAN port to check if the internet is working, and it's essential. Listen up—change your default router passwords before you even connect them to the internet.
Listen up—change your default router passwords before you even connect them to the internet.
That's it, such a simple task, but one that doesn't get done as often as it should. If you bought your router, this is what you should do. I know, sometimes you don't get the choice or the installing technician connects things up before you get the chance, but ask them how to log in to change the password, and do it before they leave just in case something goes wrong and you need them to show you how to reset your router and try again.

Related
7 devices that use terrible passwords by default
Do you change the default password as soon as you plug things in?
5 Enable WPA2 or WPA3
I won't use insecure encryption on my Wi-Fi
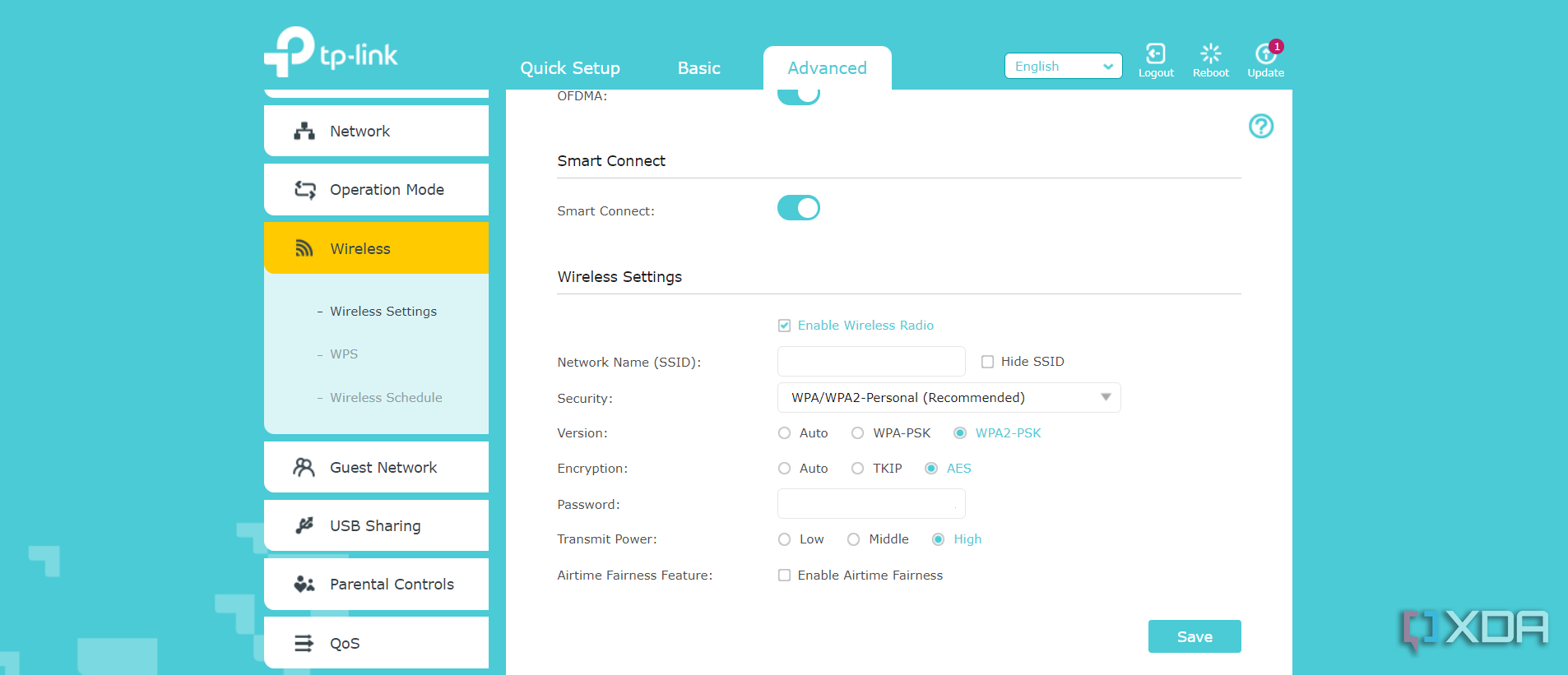
While I'm in the router admin pages changing the default admin password, I'll also change the Wi-Fi password. At one time, that was enough to safeguard your wireless network from intrusions, but not anymore. Even though your router supports WEP or WPA/TKIP, don't use those for your wireless encryption method. Easily available tools can crack those passwords in seconds, and you often wouldn't know someone is on your network.
I always use WPA3 if possible, as it's the latest and most secure option; however, you can also use WPA2 as an alternative. Just ensure it's AES and not TKIP, as that's the safer option. I'll also enable the guest network as it's safer to let your visitors use it, instead of giving them your main network password. That way, you can change it after they leave, and the devices with your data on are still on a different network altogether.

Related
Best Wi-Fi routers in 2025
Upgrade your home Wi-Fi so your speeds are fast and consistent in every room of your house
4 Update the firmware (and set a reminder to check for future updates)
Patch those security holes with official fixes
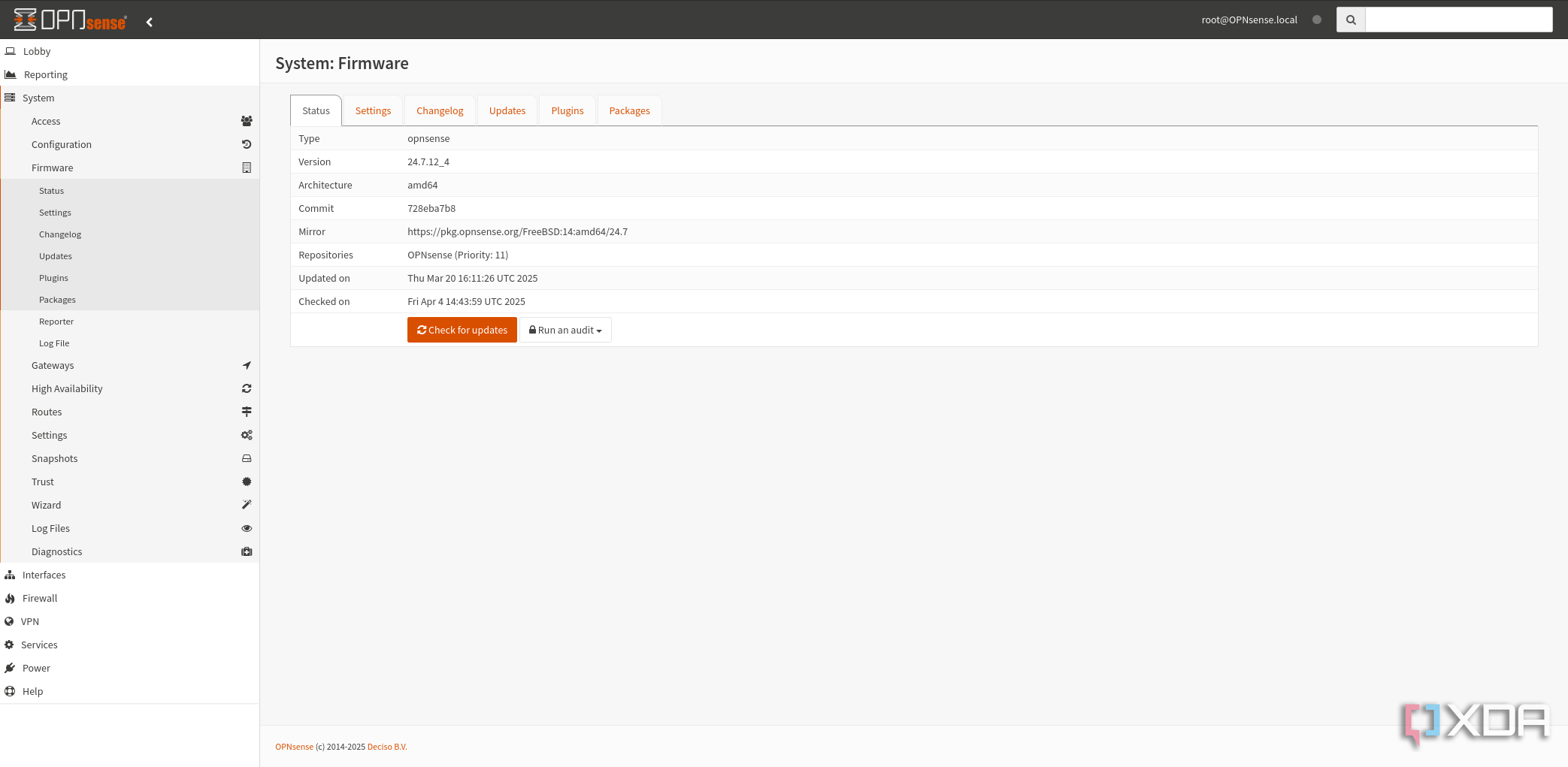
If you're in the "I don't update my firmware unless something is wrong" camp, the tent you're sleeping in is leaking. You might not notice it right now because it's not raining, but it's there, and it's time to change your habits. The best time to update your router firmware is as soon as you get it. The second-best time is when you remember to check for an update, because every update will make your home network that little bit safer.
If you're in the "I don't update my firmware unless something is wrong" camp, the tent you're sleeping in is leaking.
Router firmware updates address critical security issues, annoying performance issues, and numerous other problems. Sure, you can wait a few days, read the patch notes, and check to see if anyone has issues before updating, but please do the update. It's best for everyone. Routers are often hijacked into botnets, and the security issues those firmware updates address are prime targets for zombification.
3 Segmented IoT devices on their own VLAN
And added a Guest network for actual guests
My home network is only as secure as the least secure device on it, just like anyone else's. And you know what is known to be insecure? IoT devices, pretty much across the board, and some are near impossible to put good enough security on. That's why I'll put them on a segregated VLAN, so they can only communicate with each other and the apps that control them, and not with my computers or storage server.
Even if those devices are secure when I add them, there's no guarantee that they'll stay that way, whether a security issue will be discovered (and not patched), or they get compromised by malware. By keeping them away from my other home network, I keep my data safer and also prevent the noisy broadcast signals from the IoT devices from interfering with the networks that benefit from lower latency and more bandwidth.

Related
Please stop exposing your IoT devices on the internet; your smart light might betray you
If you're not careful, your IoT devices could allow an attacker access to your home network.
2 Turn off vulnerable features
Sorry UPnP, NAT-PMP and WPS, you're no longer needed

A collection of Playstation 5, Xbox Series X, a Nintendo Switch dock, and PlayStation 3 bundled together.
Depending on your router, several features may be enabled that are designed for easy use, but this also means they're easy for attackers to exploit. Wi-Fi Protected Setup (WPS) lets you join a wireless network by pressing a button and entering the pin code, but that makes your home network less secure as the pin code is shorter than your Wi-Fi password and easier to crack. Turn that off, as I do, and then look for UPnP and NAT-PMP. You can safely turn these off, as most devices and programs have better, more secure ways to transmit data outside of your home network.

Related
4 reasons you should consider disabling UPnP in your router
You probably don't need it anymore, and it's a security nightmare.
1 Got myself a firewall
And set up encrypted remote access
For years, I relied on the built-in firewall in the ISP-provided router to secure my network. But no longer, as whether I've got a consumer firewall or a customized one made from spare parts, I won't be without one. It's not enough to rely on the ISP, or on the basic security offered on consumer routers. It's also not enough to install a hardware firewall on your network and leave it unconfigured, as the process of refining access and rules requires time. Time well spent, though, if it keeps my home network secure.
And whether I've got a self-hosted remote access solution or using Tailscale, having a secure, encrypted way to access my home network when not physically there is an essential part of my overall security strategy. If my mobile data is being encrypted and then sent to my network before going to the intended receiver, I'm protected from man-in-the-middle attacks or other ways to get my data.
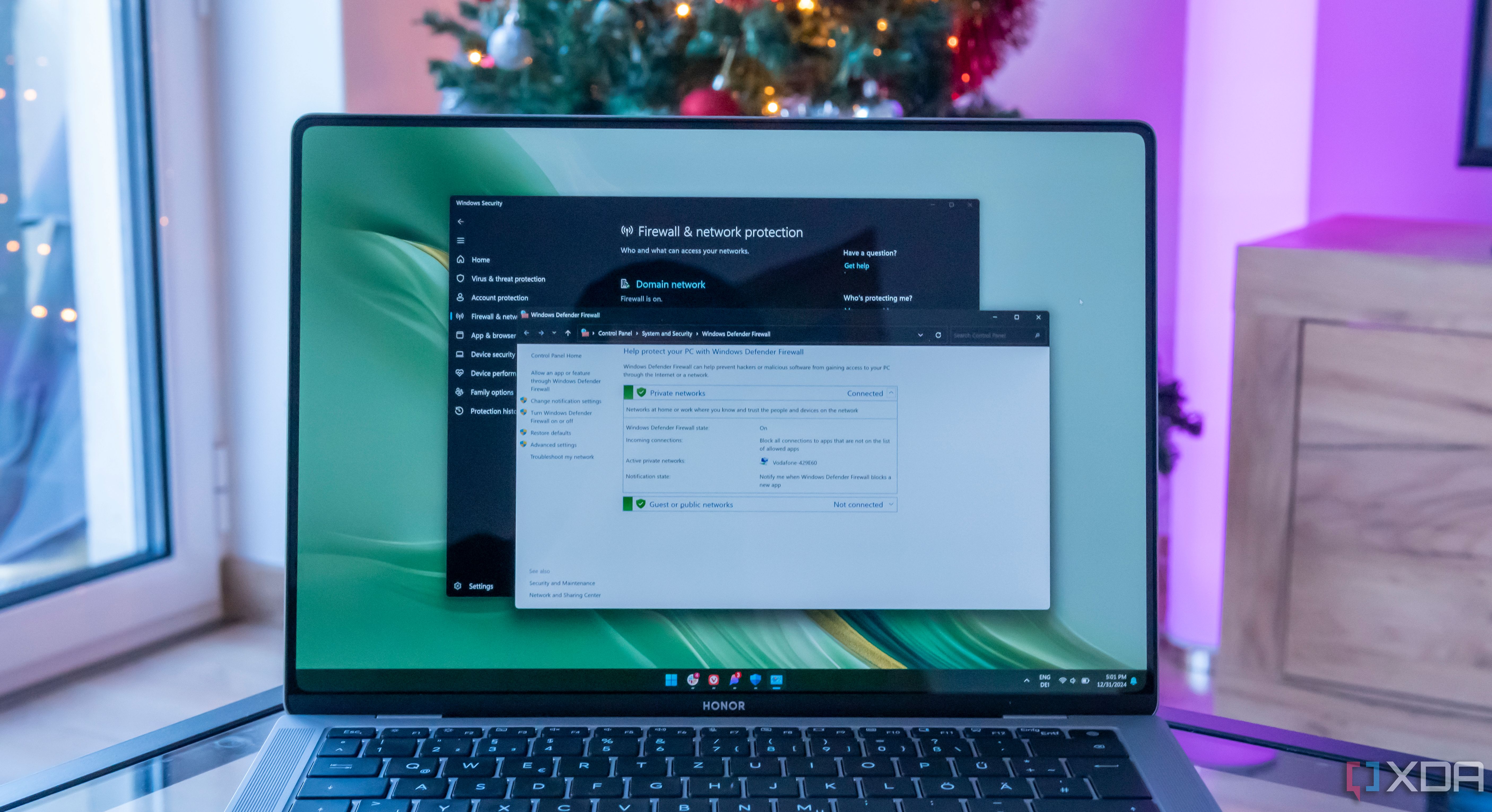
Related
How to set up and use the firewall on Windows 11
The Windows Firewall works well out of the box, but here's how you can set it up
While useful, these steps are just the beginning
Keeping your home network secure is an ever-evolving process, and while there are basic steps that work in every situation, not every network will be secure after completing these. You'll want to dig into more advanced steps, including what to do if an attacker is already on your home network. Remember, your internet gateway works in both directions, and you want to ensure security on both of them.
.png)












 English (US) ·
English (US) ·