A seasoned mechanical design engineer turned tech reporter and reviewer, Chandraveer brings more than four years of consumer tech journalism experience to the table, with bylines at Android Police and iPhoneHacks. He's written about everything from UI and UX changes across various apps to emerging software and AI trends. At XDA, he showcases his versatility in the tech reporting space with articles rooted in personal experiences and frustrations.
Chandraveer's passion for consumer tech spills over into hobbies such as mechanical keyboards, photography, and 3D printing. With an academic background in design and manufacturing, his insatiable curiosity spans beyond the digital domain. Chandraveer's downtime is an eclectic mix of reading fiction, practicing calligraphy, conceptualizing new products, and enjoying an expansive FLAC audio library.
I've noticed a stark contrast between how cafes and hotels share Wi-Fi access with guests as opposed to how my friends do it. Most enterprises usually have a dedicated network for visitors that provides limited-time internet access with a bandwidth cap after proper authentication through an SMS or email-delivered OTP. Meanwhile, my friends just toss me a QR code for their home Wi-Fi, and I am confident there's good reason to extend the corporate caution to your home as well.
A separate Wi-Fi network for your guests isn't meant to show off your tech prowess, but an essential safety feature that protects your smart home and personal devices from the poor browsing hygiene of your visitors. You don't need a new broadband line and your router should be smart enough to create one quickly so you can isolate guest devices from your primary network. But as with most things in the tech world, there’s a right way and a wrong way to do it. A poorly configured guest network can be just as bad as not having one at all, complete with the false sense of security. Here are four common pitfalls you can sidestep.
Guest networks still need protection
Open network is open season for criminals
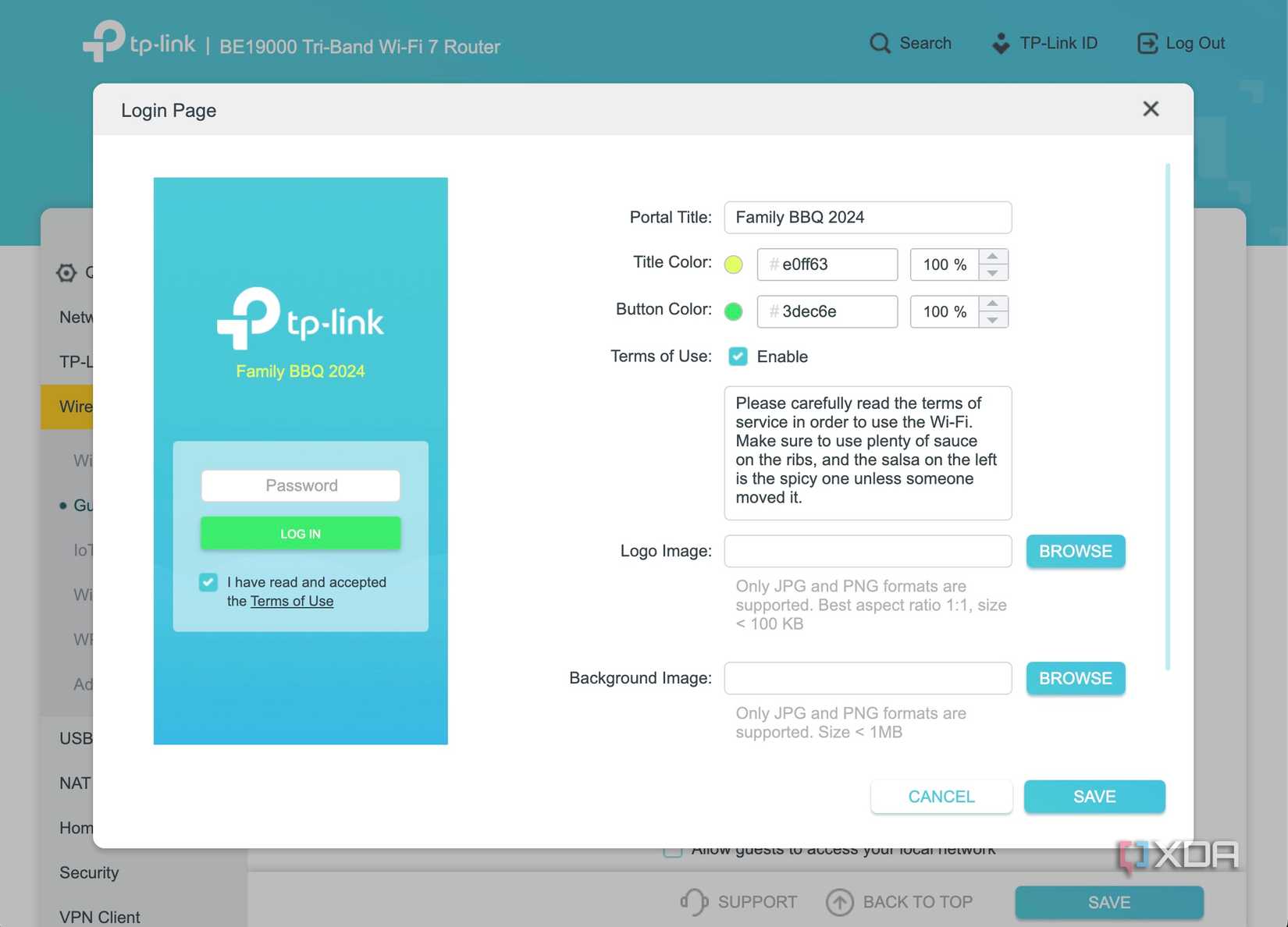
The most egregious sin you can commit when setting up a guest network is leaving it completely unprotected. I’m talking about an open network with no password or authentication for signing in. It might seem like a convenient option for your guests, but it’s the digital equivalent of leaving your front door ajar. Anyone close to your house may misuse your network for nefarious purposes, and the proposition is many times more perilous in apartment complexes.
Most router brands encourage you to set up a password for the guest network during initial setup. A simple password is deterrent enough for most bad actors so long as it isn't the default. Default combinations fall quickly when brute-forced, so you're looking for something easy to remember and secure. Alternatively, you can set up a secure password and only hand out QR codes to visitors wishing to connect. This way, only your Wi-Fi SSID that's already on the airwaves is revealed and connecting is as convenient as an open network too. Some routers include an option for a configurable portal page where guests must enter information to connect. This can help small businesses look more professional.
If your guest network is improperly isolated from your primary, a hacker could use the open guest network as a stepping stone to access your personal files, smart home devices, and other sensitive data. An unprotected guest network is also a prime target for man-in-the-middle attacks, where a malicious actor intercepts the communication between a user and the internet. Sure, an HTTPS transmission encrypts important info before it leaves your computer or smartphone, but an open file server or open router port would be a goldmine for bad actors.
Attacks may piggyback on your connection to slow down your internet speeds to launching cyberattacks from your IP address, which will land you in hot water with law enforcement. Setting up a password isn't a bulletproof solution, but is deterrent enough to be considered basic Wi-Fi hygiene.
Not defining a bandwidth cap
Choke everyone's connection and foot the bill too
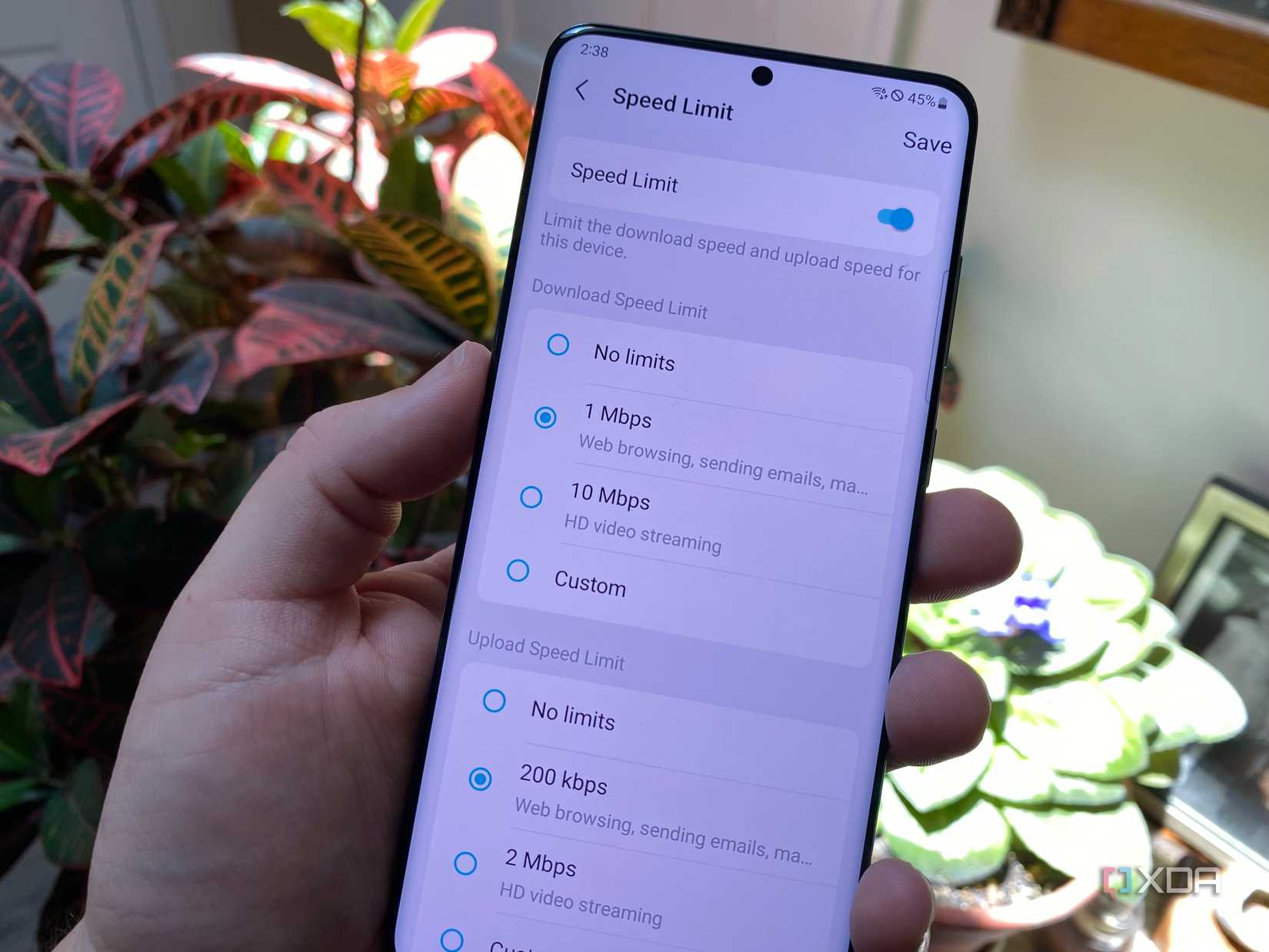
Speaking of speed, another common oversight is to neglect settings for the allocated bandwidth. As I mentioned earlier, a guest network is an isolated fork of your primary broadband connection, created by the router. Without a limit on how much bandwidth each guest device can consume, a few data-hungry visitors can quickly monopolize your entire internet connection, leaving you with a laggy, frustrating experience on personal devices. I've found teenagers downloading movies and massive game files, and neighbors secretly using my network. While the bandwidth implications and financial dent on a limited ISP plan are temporary, the legal risk from pirating content on an unprotected IP address is far greater.
Most modern routers allow you to set bandwidth limits for your guest network, and with a reasonable cap, your guests will be none the wiser while your personal devices operate unaffected. You could also relegate all guests to the slower 2.4GHz band while your personal gadgets remain prioritized on the faster 5GHz band. It’s a simple way to maintain a fair and balanced internet experience for everyone. You can also use this feature to prioritize traffic on your primary network, ensuring that your own devices always have the bandwidth they need for important tasks.
Limit the number of connected devices
Nip connection throttling in the bud
Having more guests over than a modern router can serve is nearly impossible with liberal limits on the number of simultaneous clients. However, each connected device consumes a portion of your router’s resources, and they add up quickly. Setting up a low ceiling for this is highly advisable because guest networks isolate peer connections by default. Good routers additionally have toggles for allowing guest clients to connect with each-other on your Wi-Fi, which could be useful when you're casting a video to a TV, for instance.
Some experts recommend permanently connecting untrustworthy devices, including smart home gear, to your guest network in order to protect your primary Wi-Fi network. This might seem excessive or unfeasible if your devices need to share the same SSID for controls, but running such a setup in a modern smart home quickly takes its toll on an older router. By setting a limit on the number of connected devices, you can prevent your guest network from becoming a free-for-all that drags down your entire internet connection. It’s another layer of security that can help you keep your network under control.
Smart devices might still have full network access
Asking for trouble
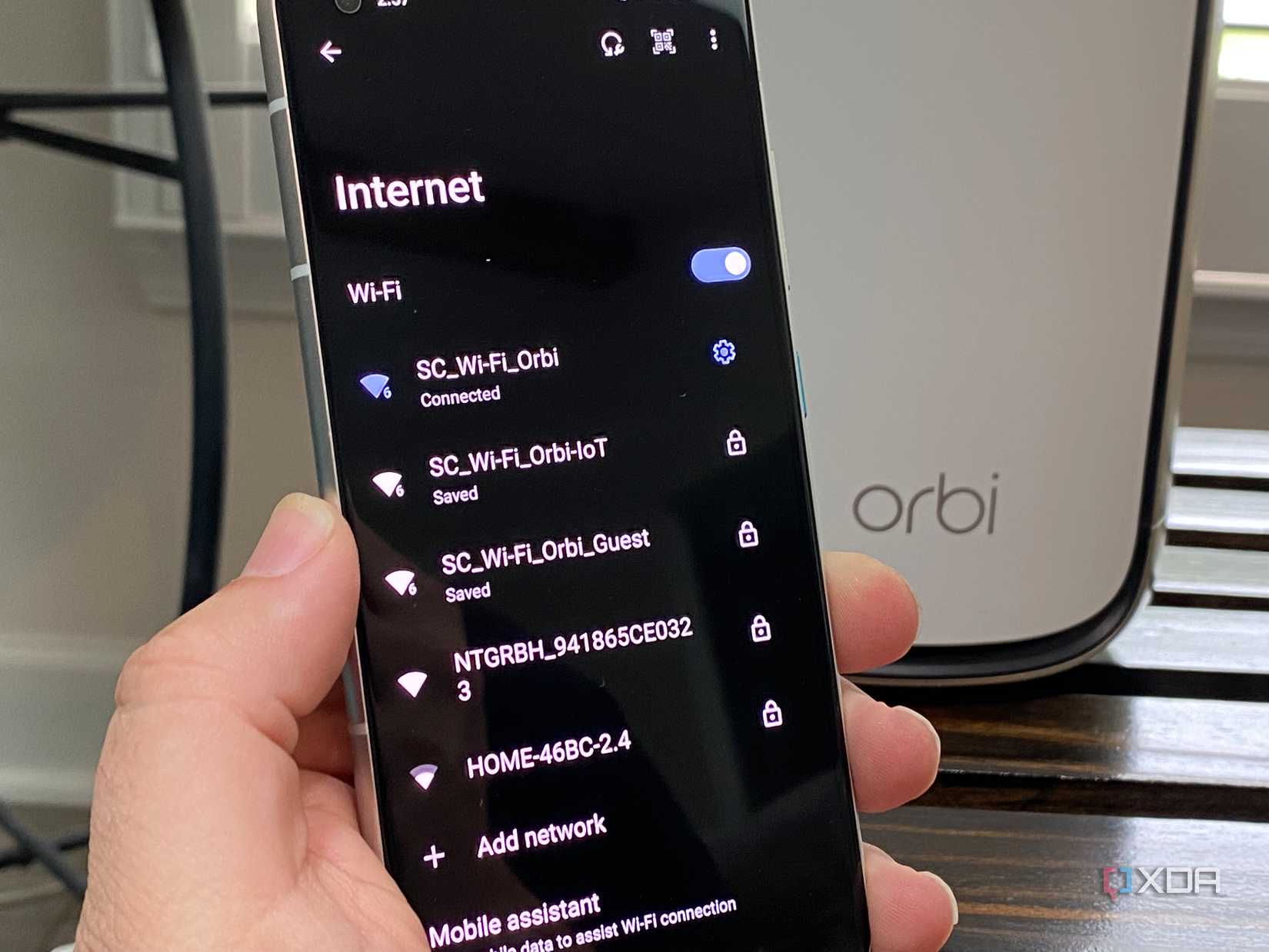
Continuing the prior advice, if you'd rather have shady IoT devices that never get updates on the guest network, while your banking or personal data continues on the home Wi-Fi, another risk lurks. You see, it is easy to conflate an IoT network or guest Wi-Fi from a modern router with conventional VLAN that isolates devices connected to it from the main network. Since guest Wi-Fi is a mere use-case for a VLAN, just setting up a guest Wi-Fi is no guarantee the connection is isolated from your home network. For instance, some Netgear Orbi routers don't isolate Guest Network clients from the main and some TP-Link routers don't fully isolate their IoT SSIDs.
This may be okay if you want your smart home devices like a smart TV or speaker shared with your guest , but sensitive devices are better off tethered to a separate router, or a dedicated VLAN that promises isolation in case smart devices fall prey to attacks.
It’s a terrifying thought, and it’s a risk that’s simply not worth taking. You should turn off discoverability for these devices once they latch on to the secondary Wi-Fi, and it should give you two-fold protection from visitors controlling said devices as well as bad actors barging into your personal home network after commandeering a vulnerable IoT gadget. All your smart home gear can still communicate with the internet and your primary command center that uses the main Wi-Fi. With these precautions, your smart home should remain a private sanctuary where everything still works as intended, and guests don't mess it up.
Mistrust and safety are different things
Setting up guest Wi-Fi isn't as inhospitable as it is about ensuring the security of your main Wi-Fi network. It's an additional step that keeps your network and devices isolated from the callous browsing habits of others, and the tendency of rogue IoT devices connecting to obscure servers you don't trust fully. If it helps your image, you can entirely hide the SSIDs for your home network or IoT VLAN once everything is connected to it. Thinking of the guest Wi-Fi as a home network and the main one as a secret Wi-Fi takes the offensive down a notch when visitors connect.
Alternatively, if router firmware makes the guest network easy to toggle, you can switch it on only when needed. Guest networks need not be permanent, but when you use them, please sidestep these common pitfalls.
.png)












 English (US) ·
English (US) ·