Running your own private cloud at home is a great way to shave off subscription fees every month, but even if you're not running a stack of containerized services, you probably still need to be able to access your home network while away from it. While you could set up a traditional VPN, or even dynamic DNS to connect to your home network from a consistent IP address, these aren't the best way anymore.
Instead, services like Tailscale set up point-to-point VPN tunnels, so all your devices act as if they're on the same physical network, regardless of their location. Now, in the true spirit of home lab self-hosting, Tailscale has one problem, the servers that initialize those tunnels aren't yours, and while you could use the open-source Headscale to create your control plane, it's not as powerful or as easy to use as the standard approach.
I've been cycling through numerous remote access tools lately, and one has stood out—NetBird. While you could use the version hosted on their cloud, like Tailscale, they also offer a full self-hosting option, which I had to check out as it sounds great. It's not just fast and secure; it also offers deep access control, network and DNS integration, and a fantastic web UI that has yet to let me down.
So, what is NetBird, and why do I use it?
Not every self-hosted remote access tool has identity management at the core
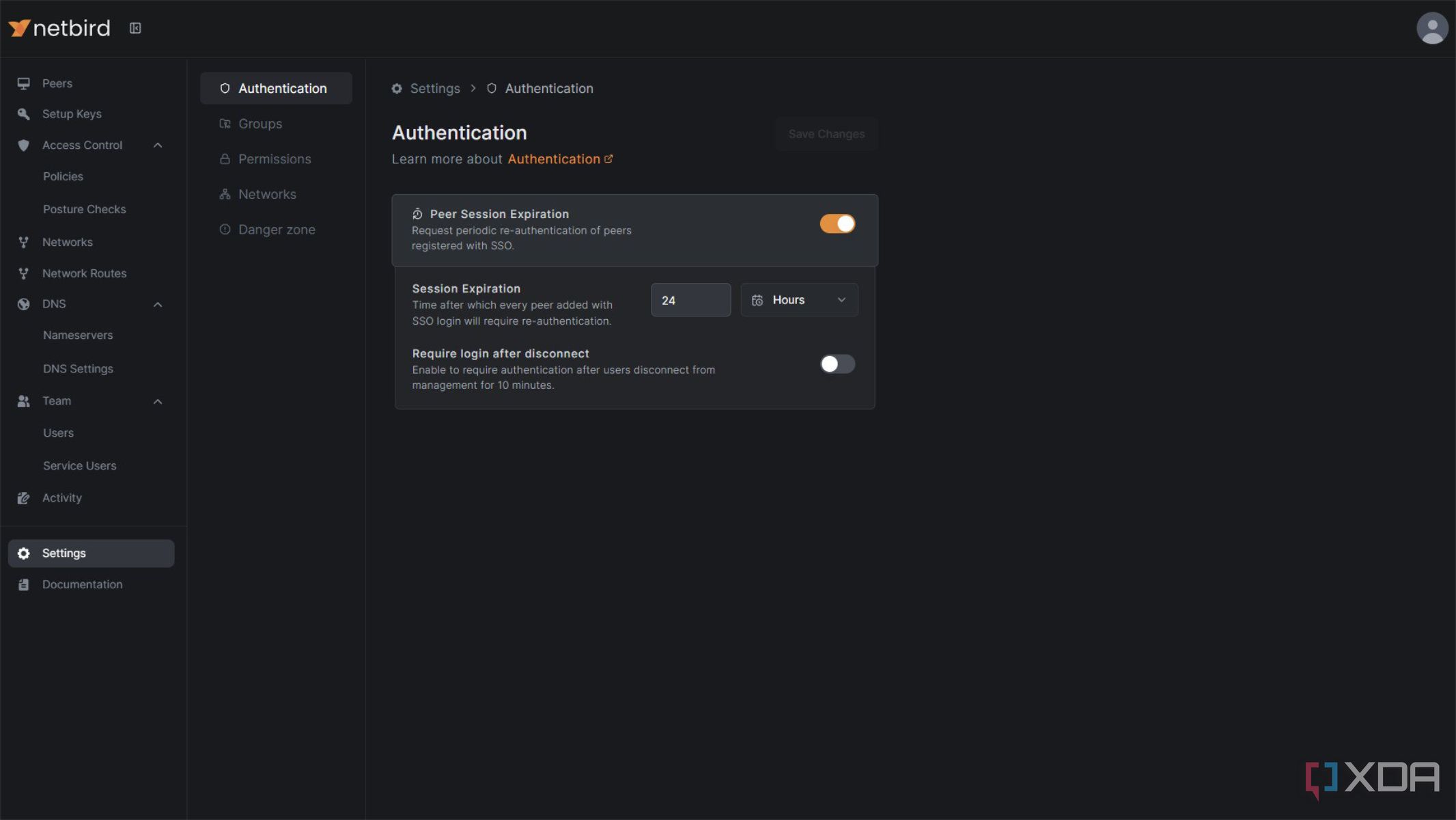
Like most well-known remote access tools, NetBird is built on WireGuard, making it fast and known for its security. However, unlike many other remote access tools, it has identity management built into its core. Therefore, when you self-host it, the first thing you set up is Zitadel, the default identity provider. But you can use any IDP that uses OpenID, including Keycloak and Authentik. The cloud-based version supports Google Workspace, Azure, Okta, and Auth0, but this feature is only available behind the Teams' subscription tier.
My experience with self-hosted access tools so far is that IDP integration is usually done after the fact, and you can often get away without using it at all. However, this is my home network, and I appreciate the idea that every user who connects to it has a login with multifactor authentication (MFA) and an audit trail of events, just in case. It's a nice touch in a sea of potentially stormy waters.
Once Zitadel is working, you head to the NetBird login page and request access. I couldn't figure out why it wasn't working at first, until I remembered I hadn't set up a SMTP email server to send the registration emails from. A few minutes later, I was in the NetBird UI, adding new users and deciding on which services I was going to expose.
Be careful here, though, as it seems the ability to approve peers is limited to the cloud-based version, so you could end up with new users that you don't want. That's possibly okay because new users don't have access to anything unless you've set up access control to allow ALL, which is bad security practice anyway. Using robust access controls to allow only specific user groups to use individual devices and services is always the best way.
Customize everything with a great UI
One thing I appreciate about NetBird is the well-made UI. On the user's side, all they need to do is download the NetBird app to their computer or mobile device, sign in with their login details, and any services, devices, and networks configured for their username will be available. You can even create setup keys that authenticate a device on its first use, allowing you to automate deployment with tools like Ansible, Terraform, and others.
But the other thing? The cloud-hosted version of NetBird has some features behind the subscription model is exactly the same as the self-hosted one. None of this "self-hosted users are several versions behind" or any of the other bait-and-switch tactics of some networking companies.
The other huge plus point for me? A comprehensive documentation section that not only tells you how to get started, but also the intricacies of every feature with examples, well-written how-tos, and explanations of which features are available on the free plan or not.
Related
How are Cloudflare tunnels different from a VPN?
Both let you access your services remotely but they do it in very different ways.
NetBird is pretty great, but it might not be the best fit for you
Remote access tools might use the same protocols, but the deployment is very different
NetBird is a powerful, self-hosted access tool with numerous advanced access control policies that do more than enable NAT traversal for encrypted tunnels, making SSH access to remote web servers easy to set up. You could set up one peer on your home network as a routing peer, potentially on your router, and access internal resources on your network securely. It's also simple to set up site-to-site tunnels, without the complicated firewall configurations you'd typically need.
You have other options
It has a lot going for it, but not everyone wants to self-host an identity management provider. You can still use the free cloud-based version for up to 5 users and 100 devices, although you'd lose access to Posture Checks (handy for segmentation) and a few other things. Plus, it's not like there are no alternatives:
|
Protocol |
WireGuard |
WireGuard |
WireGuard |
Custom (VL1/VL2) |
|
Hosting |
SaaS/self-hosted* |
Cloud/self-hosted |
Self-hosted only |
Decentralized/self-hosted* |
|
Authentication |
SSO, MFA |
SSO, MFA |
SSO, 2FA, PIN codes |
Shared network key |
|
Ease of Setup |
Very easy |
Moderate |
Technical |
Zero-config |
|
Use Case Focus |
Individuals/teams |
Business teams |
Homelab/self-host |
IoT/decentralized |
|
Pricing |
Freemium |
Freemium |
Free |
Freemium |
*Self-hosting requires enterprise plans or community editions.
What I would say is play around with a few, and see which one clicks with you and your needs. It might be the best service in the world on paper, but you're the one who has to manage it and deal with the everyday admin, and that's my least favorite part. Sometimes you just want a simple, quick fix that is no less secure, but hands off identity management and other complex tasks to the service you've signed up for.

Related
4 reasons you need to use WireGuard instead of OpenVPN for connecting to your home lab remotely
If you have a home lab and want to connect to it remotely, WireGuard is much better than OpenVPN.
Don't be afraid to change your remote access tool if your needs change

If all you need is a simple, short setup service that allows you to link your devices to your home network from anywhere, NetBird fits the bill. It was measurably quicker to setup than every other self-hosted tool I've used, and wasn't much harder than signing up on their website for the cloud-managed version. It's very powerful, and you can link it to individual services, allowing it to function as both a mesh VPN and a reverse proxy. But if it doesn't meet your needs, or you want more control, there are plenty of other solutions out there.
.png)











 English (US) ·
English (US) ·