Whether you're jetting off to tech conferences or more calming climes for a holiday, XDA Travel Week is going to get you there smarter and safer. Our self-hosted services travel with us, thanks to VPNs, reverse proxies, and other networking tools that make it seem as though our laptops are always connected to our home networks. Some of us opt for Tailscale due to its simplicity, while others use a variety of other services built on the open-source WireGuard protocol.
What they all do is encrypt our network traffic as it passes between our devices, whether they are on a plane or at a hotel, and connect directly to our home network for unrestricted and secure access to our apps and files. I've tried Pangolin, which I liked, as well as Caddy, Traefik, Nginx, and NPM, and they all perform similar tasks with varying levels of complexity in terms of setup and security.
And then a new self-hosted remote access project turned up recently, Wiredoor. It's got a polished website and documentation, a short setup time, and can use domain names and local domain names just as quickly and easily. It ticks all the boxes for me so far: OAuth2, WireGuard, SSL certificates, and Nginx, which means I can ditch Cloudflare Tunnels, as I never liked the idea of data being sent unencrypted through them.
So, what is Wiredoor, and why do I prefer it to other options?
It's simple, secure, and self-hosted, and that's just the start
Having a server full of apps to make a personal cloud is awesome, but it's hard to use those apps from outside my home. VPNs are one option, but they can be annoying to set up, especially since my ISP's external IP address changes frequently, and I've found DDNS to be unreliable in quickly picking up the new IP address.
I also have the unfortunate situation of being behind Carrier Grade NAT (CGNAT), so even if I open ports to the internet, my ISP often decides that I'm not allowed to. It's a mild annoyance when experimenting with self-hosted email servers, as that involves a lot of extra work and inconvenience. It's even less pleasant when those ports are reserved for something I want to use from my home lab.
Sure, I'm not supposed to be self-hosting anything from my connection. Still, I'm also not about to pony up for a business-class connection to reduce the number of cloud services I'm putting data on. Therefore, the only viable solution is to utilize VPNs, tunnels, and a reverse proxy to access my hosted services, as if I were at home.
Wiredoor makes it simple
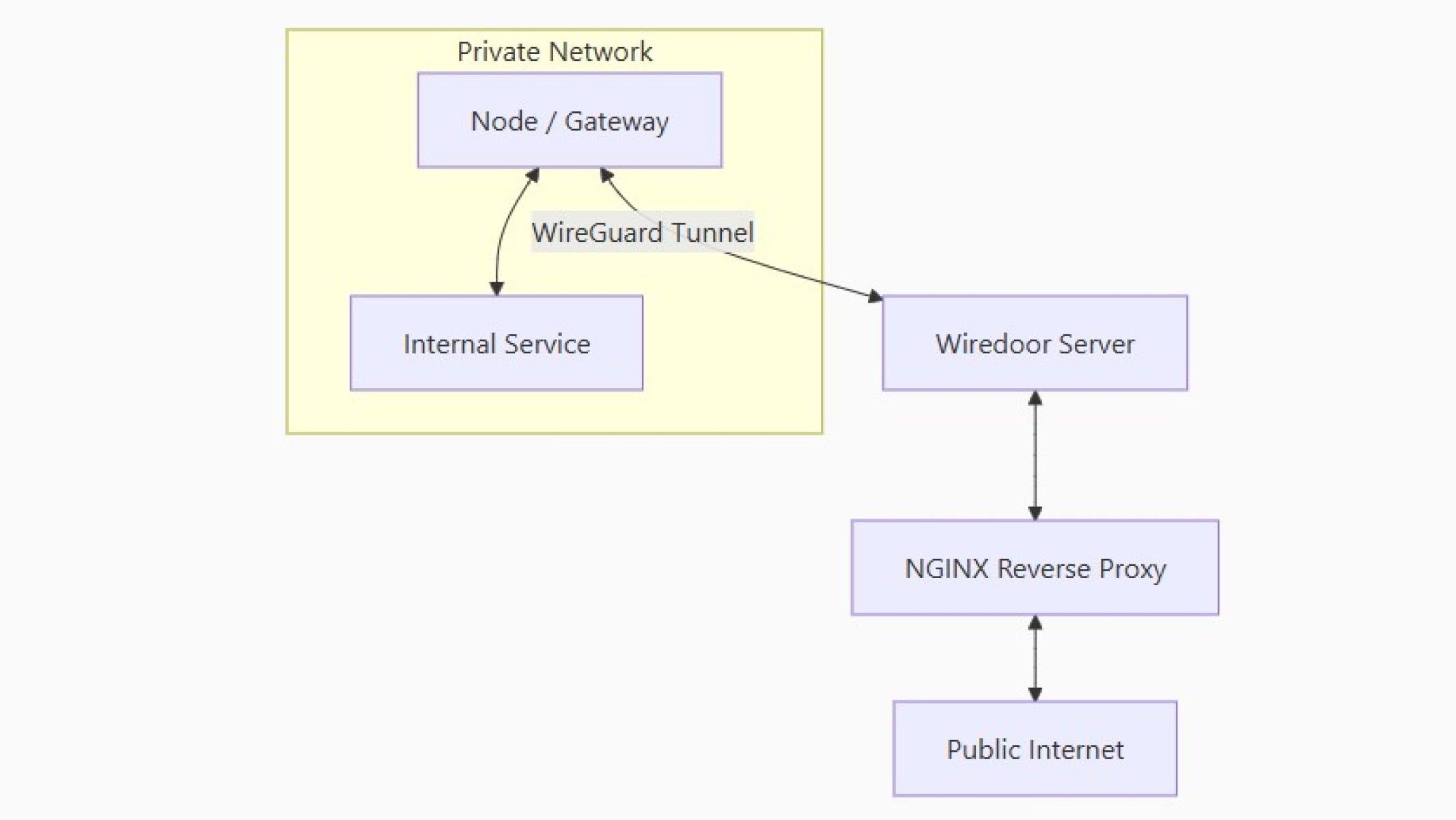 Source: Wiredoor
Source: WiredoorWiredoor is functionally similar to a Cloudflare Tunnel, in how it sets up the connection between your client and service. Except, it does this without breaking encryption anywhere on the chain, so your self-hosted solution stays safer, without anyone being able to snoop on your data. That means you can use it to access your Jellyfin library or any other streamed media that Cloudflare doesn't want you to use its services for. The process is simple to understand:
- Wiredoor sits on my VPS
- Nodes connect to Wiredoor over WireGuard tunnels
- Services on the private network the nodes are installed on are securely exposed
- SSL certificates are handled automatically
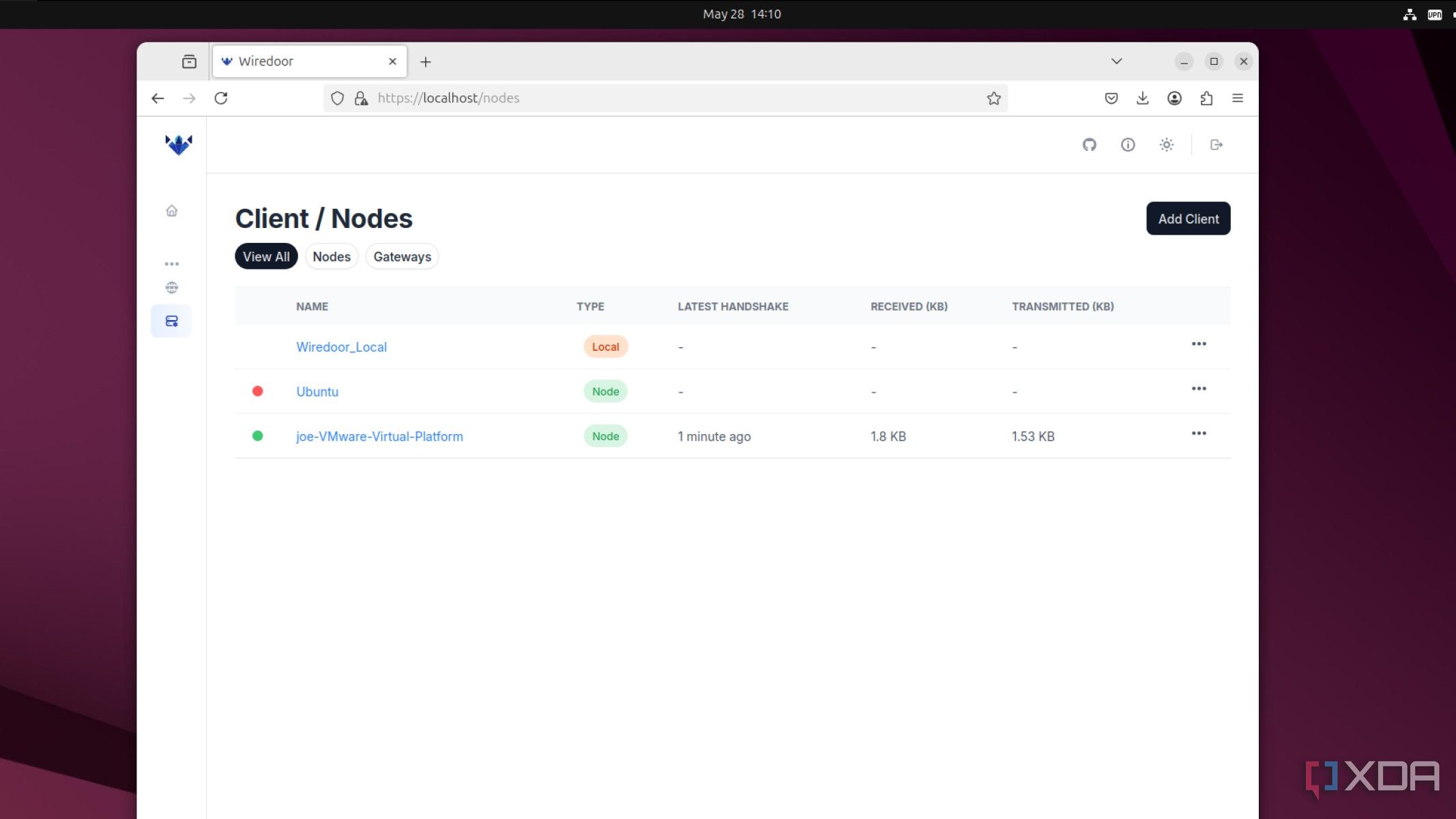
I connect to the domain on my virtual private server (VPS) or on my home lab server. Wiredoor knows which domain name corresponds to which service, initiates the connection, and passes data securely to me. I've been using it to get accustomed to it and see if it meets my needs, but the next step is to integrate OAuth2 so I can use my preferred SSO providers to log in to my services without having to set up SSO manually.
When I'm traveling, I use the VPS, as it sidesteps my restrictive network issues and gets me up and running with my collection of containerized apps in no time. It wasn't a perfect transition the first time I used it, as I managed to lock myself out of my home lab as I couldn't access the Wiredoor node via HTTPS, but because the setup is quick, it was only about ten minutes til I had things running again.

It's just as powerful in the home lab
Set up reverse proxies for individual services without needing external domain registration
Another awesome feature of Wiredoor is that it works with localhost or any internal DNS records you may have set up for testing purposes. That means you can point it to testing.local or any other home lab URL and have it work its magic. If you're using a node to expose services you don't even need to add the IP address, just the protocol and port to be used, and Wiredoor handles the rest.
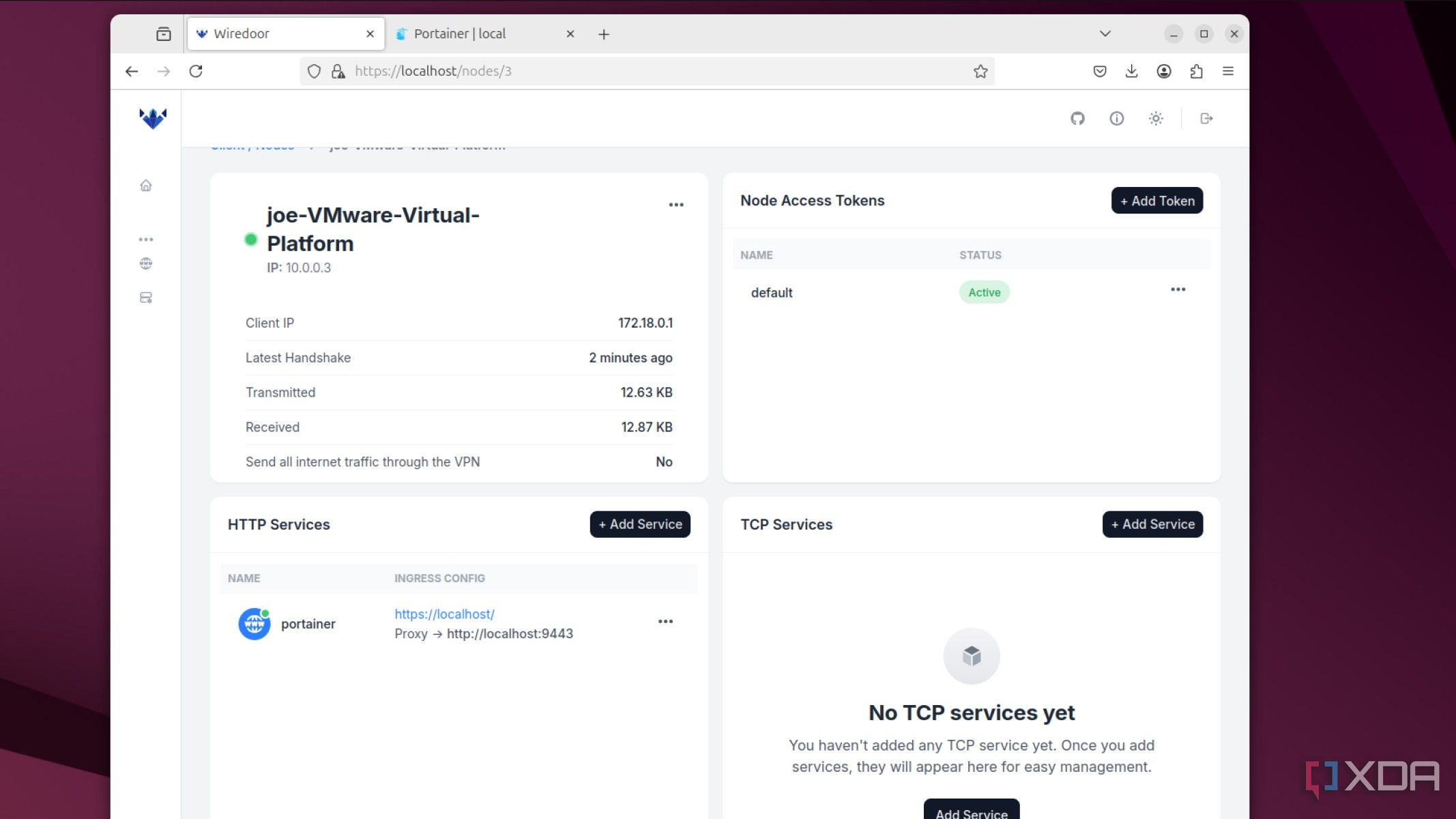
That makes it perfect for testing, as you can set up your desired services, use placeholder DNS records to ensure everything connects, then push it to prod with those settings, once you've changed the DNS to your running IP addresses. Even if you don't have a production environment, it's still for accessing your services with easily memorable URLs, without the need for port forwarding, manual setup of reverse proxies, or using Cloudflare, AWS, or Azure for secure tunnels.
Related
How are Cloudflare tunnels different from a VPN?
Both let you access your services remotely but they do it in very different ways.
I really like Wiredoor for its simplicity and speed of setup
When setting up a remote access system for self-hosted apps, it's important to me that they don't require externally opened ports. Wiredoor lets me do just that, from any private network I have access to, and from a variety of hosting solutions including Docker containers, servers, IoT devices, and Kubernetes clusters. It utilizes WireGuard for encrypted reverse VPN tunnels, eliminating the encryption break that occurs with Cloudflare Tunnels. Additionally, it already offers most of the functionality I need, despite being a relatively new project.
.png)











 English (US) ·
English (US) ·