Maker, meme-r, and unabashed geek, Joe has been writing about technology since starting his career in 2018 at KnowTechie. He's covered everything from Apple to apps and crowdfunding and loves getting to the bottom of complicated topics. In that time, he's also written for SlashGear and numerous corporate clients before finding his home at XDA in the spring of 2023.
He was the kid who took apart every toy to see how it worked, even if it didn't exactly go back together afterward. That's given him a solid background for explaining how complex systems work together, and he promises he's gotten better at the putting things back together stage since then.
Setting up network segmentation is best practice, whether using a series of VLANs or some other method. While we tend to speak of one method or another as singular forces, really the best practice is a layered method with multiple features acting in concert, whether that's firewalls, VLANs, or other means.
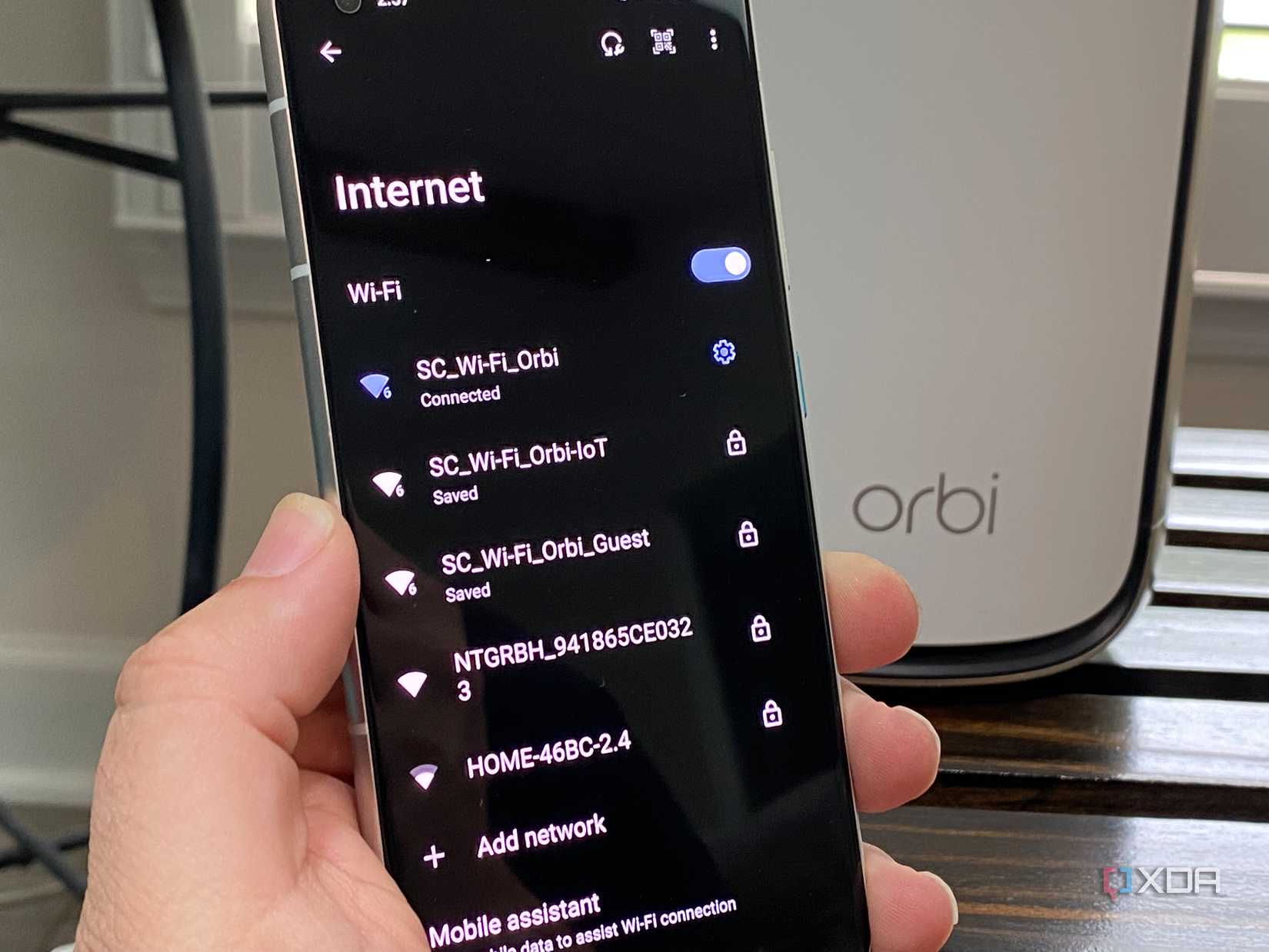
That means some networking equipment above the router that your ISP supplies is necessary, and a managed network switch is an integral part of the equation. Really, your network topology can be as simple or complex as you want, and security is a sliding scale based on your personal risk model, but a managed switch makes both easier. They come with advanced networking features, like port isolation, to help you combine your network in a scalable way that makes sense.
If you've never used port isolation before, it's a way of isolating the devices connected to those ports from being able to communicate with other isolated ports, while still reaching non-isolated ports, such as the ones leading to the internet or different servers. Unlike inter-VLAN communications, it all works on the same IP subnet and VLAN, so no complicated firewalls or transport rules need setting up.
Easy segregation of your IoT devices
They can't talk to what they can't see
We all know that our IoT devices have differing security levels, which means they really can't be trusted. They don't get frequent security updates, older ones have weak or no security at all, and they tend to broadcast across the whole network, jamming up the airwaves for every other device. Neither do they like being fully segregated on a VLAN, because you still have to be able to control them somehow.
But by using port isolation on your managed switch to a single AP that all the IoT devices can connect to, all of that broadcast chatter goes onto a single broadcaster, away from the devices like your phone and laptop, which like low latency communication. If you're using Home Assistant, you can put the server on a non-isolated port, and then the IoT devices can still talk to it for commands, while reaching the internet for updates.
 Credit: Source: Zyxel
Credit: Source: ZyxelSetting up a guest network without VLANs
Skip the arduous task of firewall rules with this one simple trick
Setting up a guest network makes your home network safer, but normally, you'd set up a VLAN for the purpose, and then have to add firewall rules, and decide if you want to allow networked printers or other devices through the security blocks. With port isolation, you can leave shared resources like your LAN-connected printer on an un-isolated port, and then every device connected to your network, whether on an isolated port or not, can reach them. This approach can be simpler as you only need to keep track of which ports are isolated or not, while not allowing guests to reach the NAS, server, or personal computers over the network.

9/10
Speed 1Gb
Interface 10x RJ-45 (2 uplink), 2x SFP
Enhanced security by limiting lateral movement
Reducing your attack surface is always a good plan
One of the biggest network security myths is that a single device is enough to secure your whole network. No matter how advanced that single device is, it won't be able to protect every segment of your network, every protocol, every app, every port, and so on. The only way is a fully layered approach, and by using port isolation, you stop lateral movement across your network.
Even if an attacker gets a foothold on one device, the isolated ports won't let that device communicate with other isolated ports. Yes, it will still be able to communicate out to the internet, but the spread is reduced, and that might be the difference between an IP camera being popped and that same attacker getting onto your NAS, or personal PC, where the impact of their intrusion will be significantly greater.
Simplified management and troubleshooting
Port isolation narrows down your scope of issues
Network security is complex, and every small win you get makes a difference. Port isolation is quick to enable, works instantly as it's done on the local switch, and doesn't require complicated coordination between switches, routers, and DHCP servers to work. That makes basic network security easier to set up, and gives a foundation to build upon.
Plus, it makes troubleshooting easier. You know which devices are connected to each isolated port, and which are connected to non-isolated ports. If there's a miscommunication issue between them, you know which ports to look at first, and can see if it's a wiring issue, or if something was accidentally put on another subnet. Remember, isolated ports still stay on the subnet of that switch, making IP-related issues easier to scan for and fix if they crop up.
Port isolation is yet another important feature that managed network switches enable
Again, port isolation (or protected ports or private VLAN edge, depending on vendor) gives us another arrow in our quiver to use for network security. It lets you effectively segregate individual ports and the devices on them from each other, without cutting off access to the internet, intranet, or other resources on non-isolated ports.
The only thing to remember is that it's limited to the single switch it's implemented on, so it doesn't extend across multiple switches without careful configuration, so as not to break the isolation. Then it's a great addition to the other security features you'll be using like a network-level firewall, network monitoring, and access control lists.
.png)











 English (US) ·
English (US) ·