A security researcher has uncovered flaws in PureVPN's Linux client that could expose users' real IP addresses and weaken firewall protections.
According to PureVPN, the flaws are limited to its Linux GUI v2.10.0 and Linux CLI v.2.0.1. Other platforms, including Windows, macOS, Android, and iOS, are not impacted.
PureVPN, which has been included in some of best VPN guides, has promised patches to fix the issue by mid-October.
How was the leak discovered?
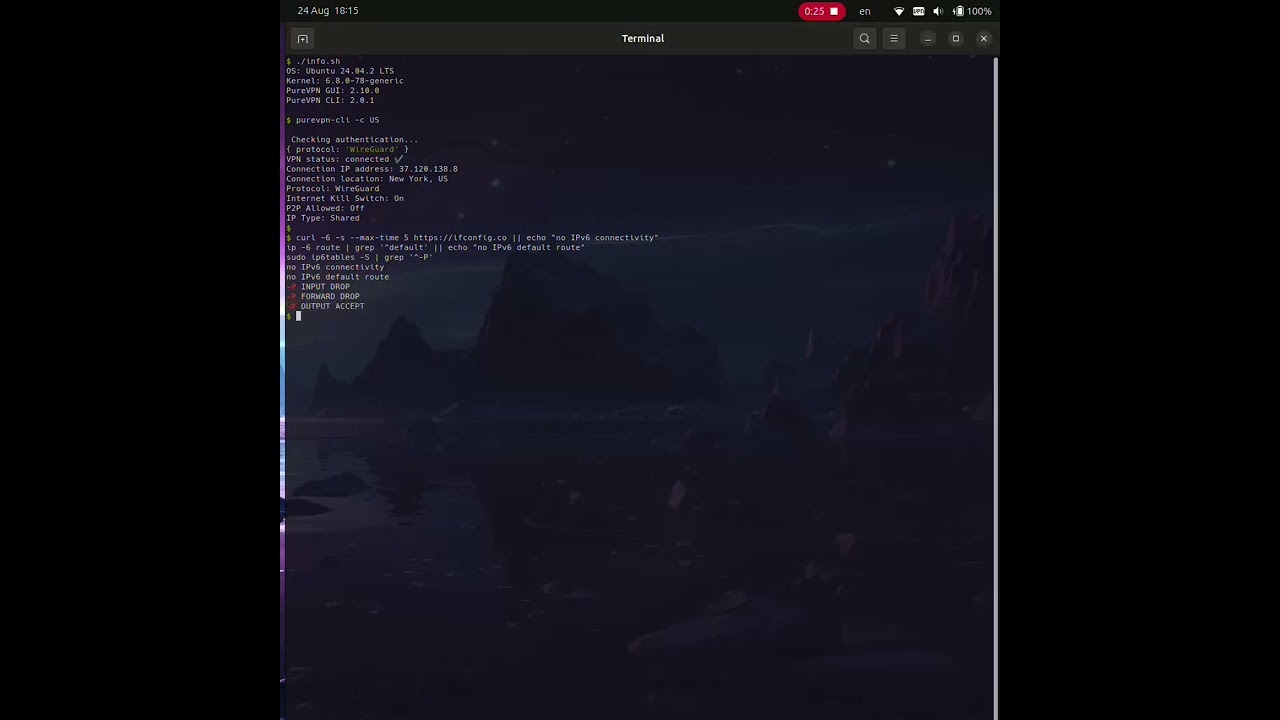
Researcher Anagogistis reported on September 17 via their blog that PureVPN's Linux app leaked IPv6 traffic in certain conditions and reset firewall rules without restoring them afterward – the issue was first discovered in late August.
According to Anagogistis, tests on Ubuntu 24.04.3 with kernel 6.8 showed that the client failed to block IPv6 connections, meaning a user's actual IP could slip through even while connected to the VPN.
In addition, the app overwrote existing firewall rules when launching, but didn't put them back once disconnected. That left affected systems less protected than before connecting to the VPN.
Anagogistis published two videos on YouTube demonstrating the vulnerabilities in action.
PureVPN CLI IPv6 leak - YouTube
Why IPv6 leaks are an issue
A VPN's core purpose is to mask your IP address and keep traffic encrypted. If IPv6 traffic bypasses the tunnel, websites and online services may still see your real location. For privacy-conscious users, that defeats the point of using a VPN in the first place.
IPv6 is the newer internet addressing system designed to replace IPv4, and many networks now support both. While IPv4-only setups are common, IPv6 leaks are harder for everyday users to notice because connections often fall back silently. That makes this type of flaw particularly dangerous, as someone may believe they're fully protected when they're not.
The firewall issue compounds the risk. By weakening system defenses, a VPN meant to add protection could unintentionally leave devices exposed after use. For Linux users who rely on strict firewall rules to manage traffic (whether for torrenting, remote work, or server security), that's a serious setback.
How has PureVPN responded to the IPv6 leaks?
PureVPN publicly acknowledged the problems in a security advisory on September 19. The company thanked the researcher for responsible disclosure and laid out its timeline for fixes.
A patch is scheduled for release by mid-October 2025, with updated Linux clients that:
- Properly block IPv6 traffic or add an IPv6 kill switch.
- Ensure firewall rules are restored after disconnecting.
- Improve testing to prevent similar issues in the future.

In the meantime, PureVPN recommends workarounds such as disabling IPv6 manually, reapplying firewall rules after disconnecting, or forcing IPv4-only connections.
VPN leaks are not new. Over the years, researchers have uncovered DNS leaks, IPv6 leaks, and other flaws across several providers. Independent testing often checks for these issues, which is why services that advertise features like "leak protection" and a reliable kill switch are considered more trustworthy.
Linux users face unique challenges because VPN apps are often designed with Windows and macOS in mind. Firewall integration in particular can vary widely, and not all providers test thoroughly across Linux distributions. This case underlines the importance of both transparency from VPNs and continued scrutiny from the security community.
What to do if you are impacted by the leaks
If you're using PureVPN on Linux, check your client version. If you're on the affected builds, consider the following steps until a fix is released:
- Disable IPv6 at the system level to prevent traffic from bypassing the tunnel.
- Manually restore your firewall rules after disconnecting from the VPN.
- Use IPv4-only connections where possible.
- Test your setup with an online IP leak tool to confirm your VPN is working as expected.
- Consider temporarily switching to another PureVPN app or a different provider if you depend heavily on Linux security.
- Watch for PureVPN's client update in October and install it as soon as it's available.
PureVPN says its fixes will address both the IPv6 leak and firewall behavior, and the company has pledged to strengthen its disclosure process to handle future reports more efficiently.
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.
.png)











 English (US) ·
English (US) ·