Kali Linux has earned a solid reputation in cybersecurity circles for good reason. It comes packed with tools that make vulnerability assessment, penetration testing, and security auditing not only possible but also efficient. Whether I’m checking my home network for weaknesses or analyzing traffic patterns, Kali gives me the power to stay informed and proactive. Here are six features I rely on regularly to keep everything running securely.

Related
These 5 home networking tools are essential for any Windows user
Troubleshoot, optimize, and secure your home network like a pro
6 Nmap for robust network scanning
Scan, map, and analyze with detailed precision
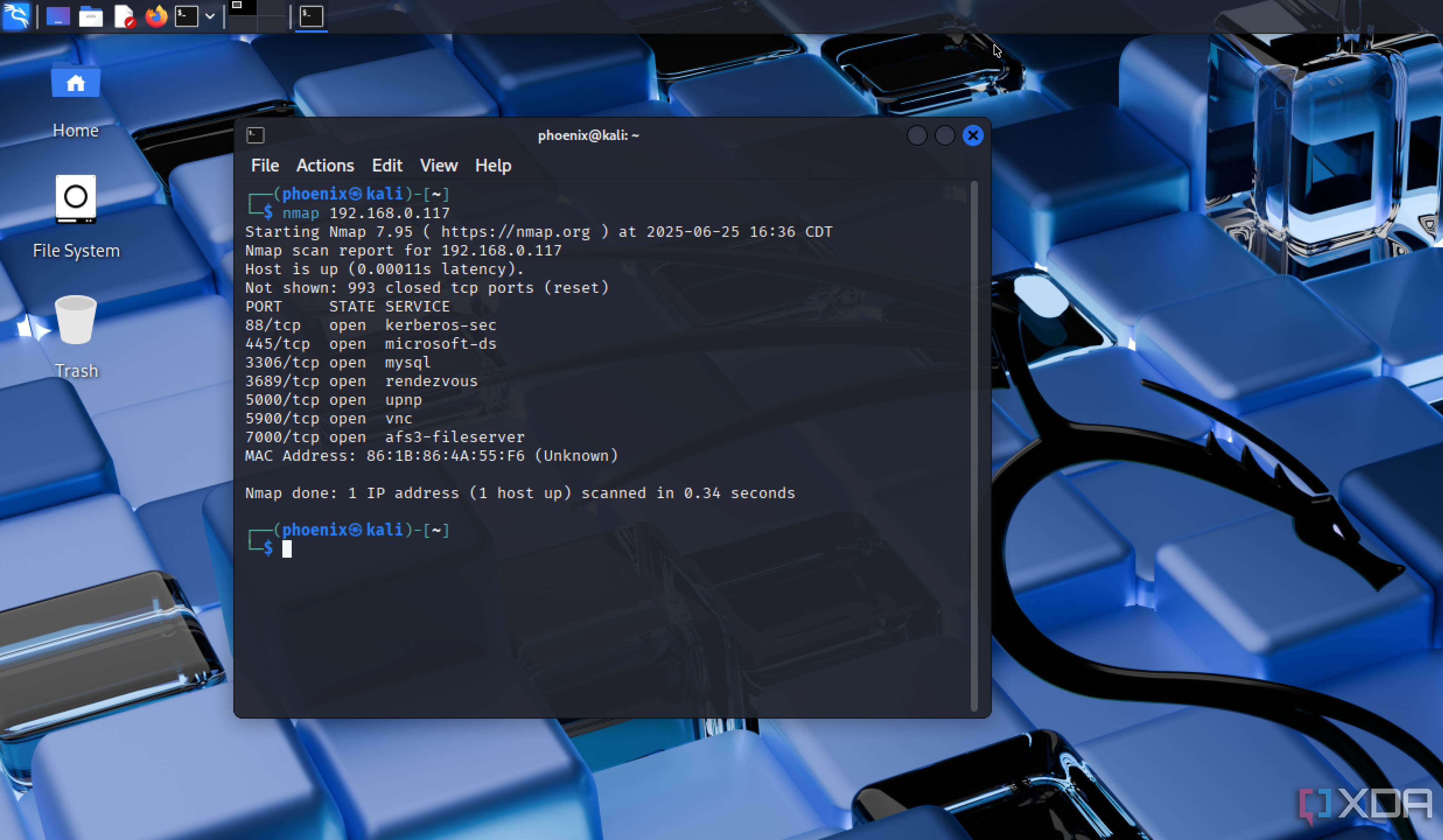
Nmap is often one of the first tools I reach for when assessing my network. It quickly reveals open ports, available services, and operating systems across all devices connected to the network. This helps me understand exactly what’s running and where potential entry points might exist. I can filter out trusted devices and focus on anomalies that may indicate misconfigured services or unauthorized hosts.
The level of customization available in Nmap is another reason I keep it in my regular workflow. Whether I want a quick scan or a deep dive, it adjusts to the task at hand. Paired with NSE scripts, I can even probe for specific vulnerabilities or misconfigurations. It provides me with actionable information that I can use to strengthen my network’s defenses.
Nmap’s reports are easy to read and share, making them ideal for documentation or for explaining findings to others. I often run regular scans on known segments to catch changes early. Keeping a close eye on the expected versus unexpected results is a simple but effective tactic.
Related
I mapped every machine in my home lab with this free tool
Capable of documenting even the most complex server setups and network stacks, NetBox is a must-have for any home labber
5 Wireshark for packet-level visibility
Monitor traffic and spot potential threats early
Wireshark offers a detailed view into what’s really happening across my network. It captures packets in real-time and provides me with the tools to dissect them on the fly. I use it to inspect protocols, flag suspicious payloads, and identify abnormal traffic patterns that may indicate a compromised device or service. Being able to drill down to the byte level is incredibly helpful for troubleshooting and threat detection.
One feature I particularly appreciate is Wireshark’s support for custom filters. I can isolate just the traffic I care about, like DNS queries or failed login attempts. This helps me stay focused without having to wade through pages of unrelated data. When something odd is going on, it rarely hides for long.
Wireshark isn’t just about reaction, though. I use it proactively to test firewall rules and validate segmentation strategies. It’s a great way to confirm that my network behaves as I expect it to. When I spot issues, I can address them before they become actual problems.
Simulate real-world attacks to find weak points
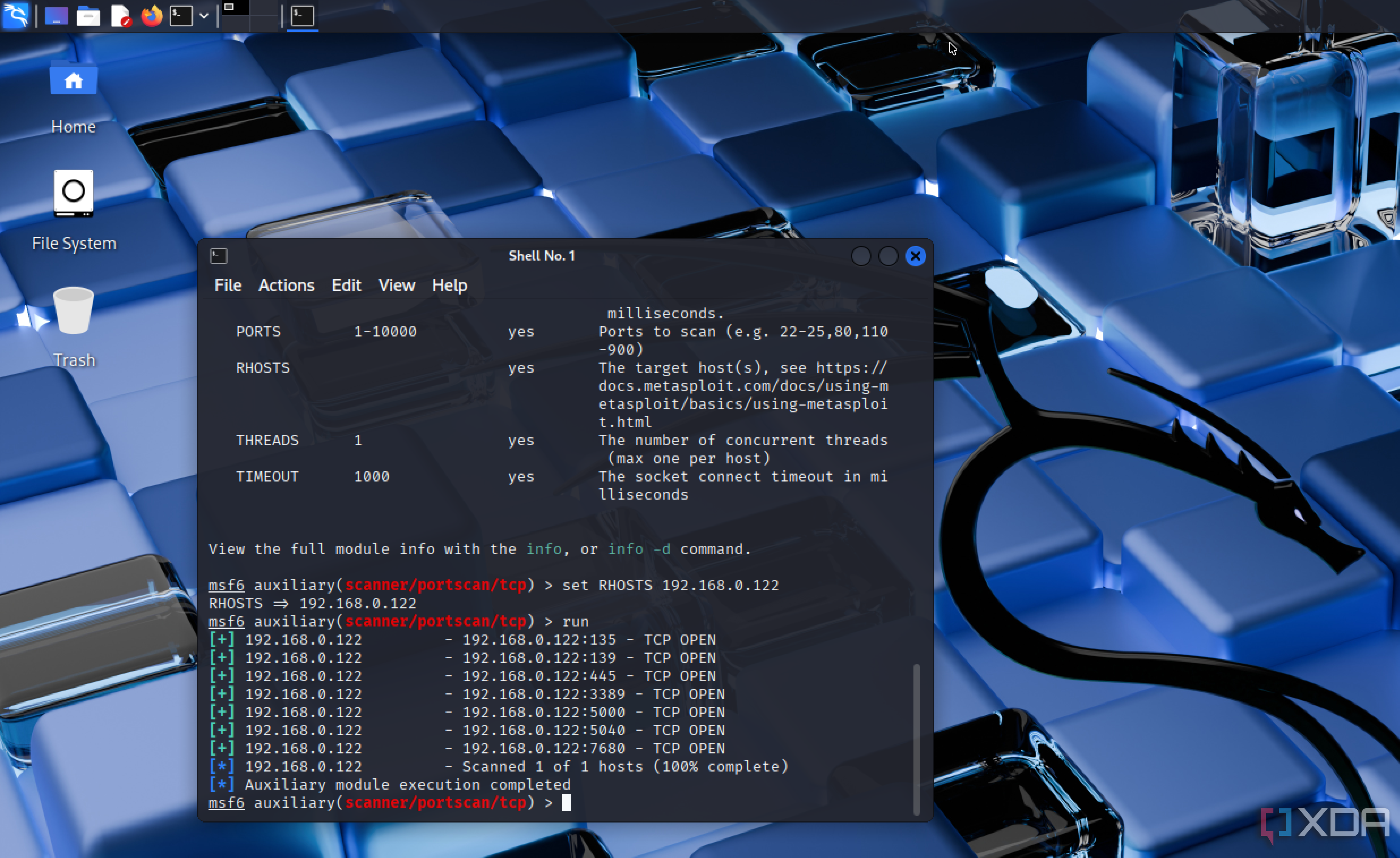
Metasploit is one of the more advanced tools in my Kali setup, but it's absolutely worth the effort to learn. I use it to simulate attacks in a controlled environment, allowing me to test how my systems respond under pressure. That gives me a much clearer idea of what defenses need reinforcing. It also helps me validate whether patches and configurations are working as intended.
It’s particularly useful when combined with known exploits and payloads. I can test specific vulnerabilities against different operating systems or service versions on my network. Metasploit provides clear feedback, so I know which targets were successfully compromised and why. That insight is hard to get from passive monitoring tools.
Another strength of Metasploit is its seamless integration with other tools. I can feed it targets from Nmap scans or use it to verify findings from vulnerability reports. This kind of integration streamlines my process and saves time. It brings offensive security into my defensive strategy.
Related
9 reasons you should use ntop on your Raspberry Pi
To level up your network administration game, you should consider running ntop on your Raspberry Pi
3 Aircrack-ng for wireless auditing
Analyze and secure your Wi-Fi environment

Wireless security can often be overlooked, but Aircrack-ng keeps me on top of it. This suite of tools lets me capture packets, analyze encryption protocols, and even test password strength on my own network. It helps me make sure my wireless access points aren’t a weak link in the chain. I use it regularly to check for signal bleed and rogue access points.
I’ve also used it to validate changes in Wi-Fi configuration, especially after firmware updates. Aircrack-ng makes it easy to confirm whether old vulnerabilities have been patched or if new ones have been introduced. It helps me avoid surprises when upgrading equipment. Since wireless networks are so common, I find this tool critical to my overall security approach.
When I’m working in a more mobile setup, like with a portable Raspberry Pi setup, Aircrack-ng really shines. I can run audits in the field and test signal strength or security posture without needing a full workstation. That flexibility helps me maintain strong wireless security no matter where I am.

Related
4 reasons I installed RaspAP on my Raspberry Pi
It may not be the most powerful option, but it's definitely one of the friendliest.
2 Burp Suite for web application testing
Dig into web apps to uncover flaws
Burp Suite is my go-to tool for checking the security of any web applications I run. Whether it’s a self-hosted service or something I’ve deployed for testing, Burp helps me catch problems early. It intercepts and modifies HTTP traffic, making it easy to simulate attacks like XSS or SQL injection. I use it to explore the full request and response cycle in detail.
One of its biggest strengths is the ability to automate vulnerability scans while still allowing manual inspection. I like using the built-in spider to map out an application and identify all of its endpoints. That gives me a solid foundation to dig deeper into each route and input field. It also flags inconsistencies and poor security practices.
When I do find issues, Burp Suite provides me with the information I need to fix them quickly. I can replay requests with different parameters or see exactly how an app reacts under pressure. It’s not just about finding vulnerabilities but learning how they behave. That makes it easier to build more resilient applications from the start.
Related
5 of the best tools for monitoring your home lab
Keep a weather eye on your home server with these incredible services
1 Netcat for quick and versatile testing
Lightweight but powerful for network debugging

Netcat may seem simple, but it’s a tool I use frequently. It functions like a Swiss Army knife for network communication, letting me send and receive data between systems. I use it to test open ports, verify firewall rules, or create ad-hoc data transfers. It’s especially handy when I need to troubleshoot without setting up a full testing suite.
One thing I like about Netcat is that it works well in scripting and automation. I’ve built lightweight diagnostic scripts that check system responsiveness or measure latency between devices. These can run on a schedule or be triggered on demand, providing me with instant feedback. The minimal setup makes it fast and reliable.
Despite its simplicity, Netcat is extremely flexible. I’ve used it to simulate services for testing intrusion detection systems or to tunnel traffic in test environments. Its no-frills interface lets me focus on what’s happening under the hood. It gives me control over how I interact with the network in ways that are otherwise hard to replicate.
Related
I monitor my home network by self-hosting ntopng - here’s how
From analyzing your traffic to snooping on malicious devices connected to your network, ntopng can do it all!
Kali Linux keeps me ahead of potential vulnerabilities
These tools represent just a slice of what Kali Linux has to offer, but they cover critical areas of my network security routine. By combining real-time monitoring, offensive testing, and detailed diagnostics, I can stay one step ahead of common threats. Each tool brings something different to the table, and together they form a complete picture.
Kali’s strength isn’t just in its toolset but in how easily it fits into different environments. Whether I’m working on a laptop, a VM, or even a Raspberry Pi, the same tools behave consistently. That portability means I can assess and secure my network from almost anywhere.
Security is never a one-and-done task. It’s something I check in on regularly, and Kali makes that process more efficient and informative. With these six features, I can maintain confidence in how my systems are performing and identify areas where I need to improve.
.png)












 English (US) ·
English (US) ·