OPNsense is a powerful router and firewall platform that I've been using for the past few months, and as time has gone on, I've migrated more and more of my services to it. My rationale is that many of my networking services hosted on other devices are all reliant on my home network working in the first place, so it's not a big deal to include them as a part of OPNsense as if my network goes down (taking those services with it), I don't have internet access anyway.
As a result, these are some of the services I've migrated to OPNsense that can be managed straight from the web UI. It's a nice way to consolidate many of my services into one place, and I'm really happy with it.

Related
9 things to avoid when building your dream OPNsense firewall
Building your own firewall can be incredibly rewarding, but here are some things to watch out for.
5 Reverse proxy
I use Caddy for this
I switched from Nginx Proxy Manager to Caddy a couple of months ago, and I've loved switching over. While NPM has a nice web GUI for modifying your configuration, Caddy is a simple "Caddyfile" that contains all of your reverse proxy options and can be easily modified and moved to other devices if needed. The OPNsense Caddy plugin works in a similar way, except every option is exposed by the UI.
In other words, not only do you get the simplicity of Caddy (as there's still a Caddyfile that you can see and copy out), but you get the best of both worlds thanks to the web GUI, too. I've moved all of my reverse proxies to Caddy in OPNsense, and all it took was changing the port of the web GUI that OPNsense runs on. With the reverse proxy, though, I can just access my router via an actual domain (router.home, defined in my local DNS) and it works just fine.
4 VPN
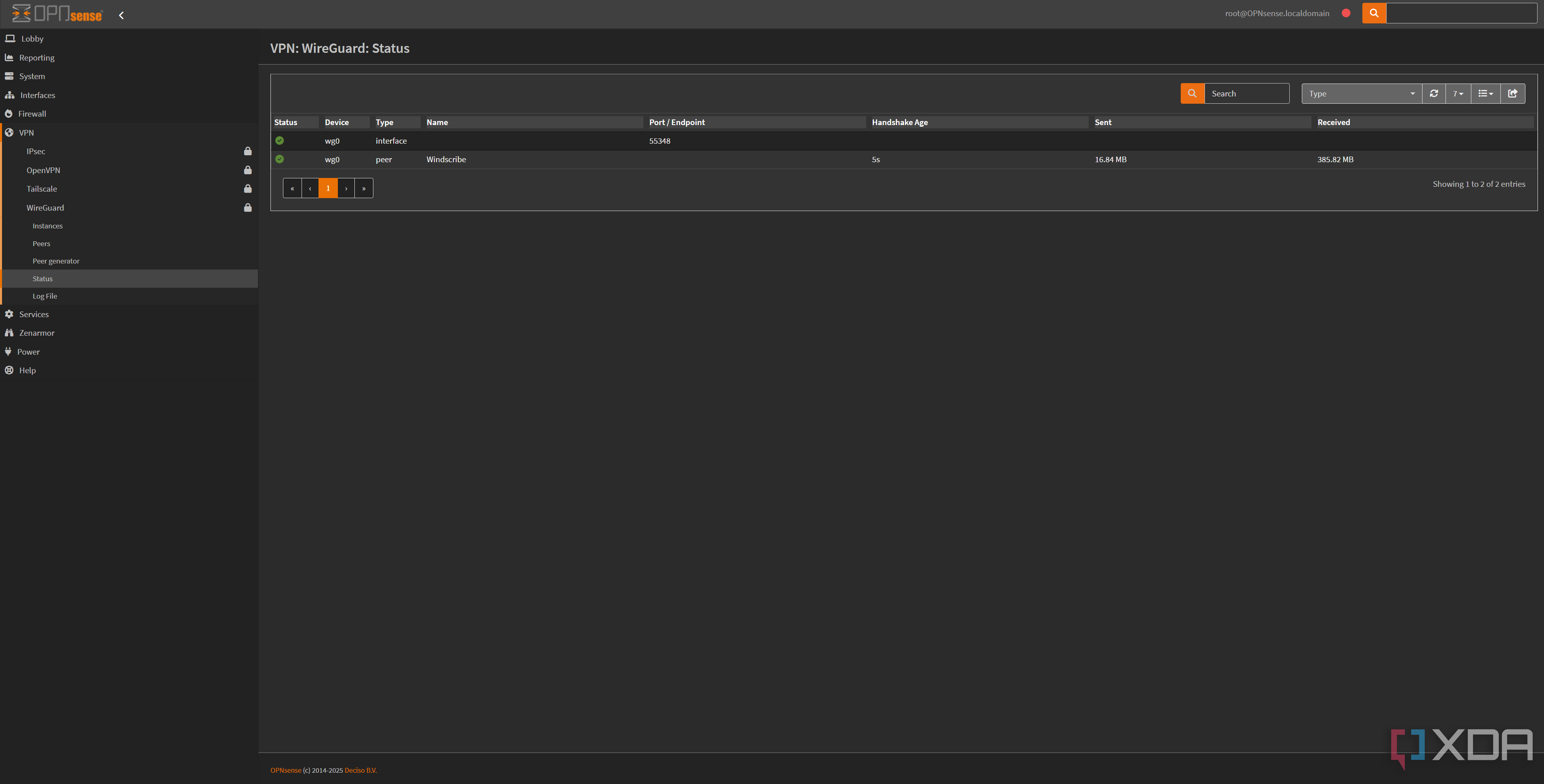
I recently created a WireGuard interface on OPNsense so that I could direct traffic from specified devices through the VPN, and while this may sound strange at first, it's actually quite useful. Typically, VPN companies limit how many concurrent devices you can have on the network, which means you'll be limited to having the client active on whatever number of devices there are at any given time. However, deploying it on OPNsense allows me to treat multiple devices as one device.
Right now, it's not convenient for devices where I would only want to sometimes use a VPN, but for those containers, VMs, or even full devices that I want to always be protected online, it's an excellent setup. It works extraordinarily well, and I can't recommend it enough. It's so much better than doing any kind of on-device container routing with Gluetun (or an equivalent application) on my NAS, for example. That's not a knock on Gluetun, that's just how good OPNsense is for that kind of configuration.
3 Tailscale
Turns my router into an exit node
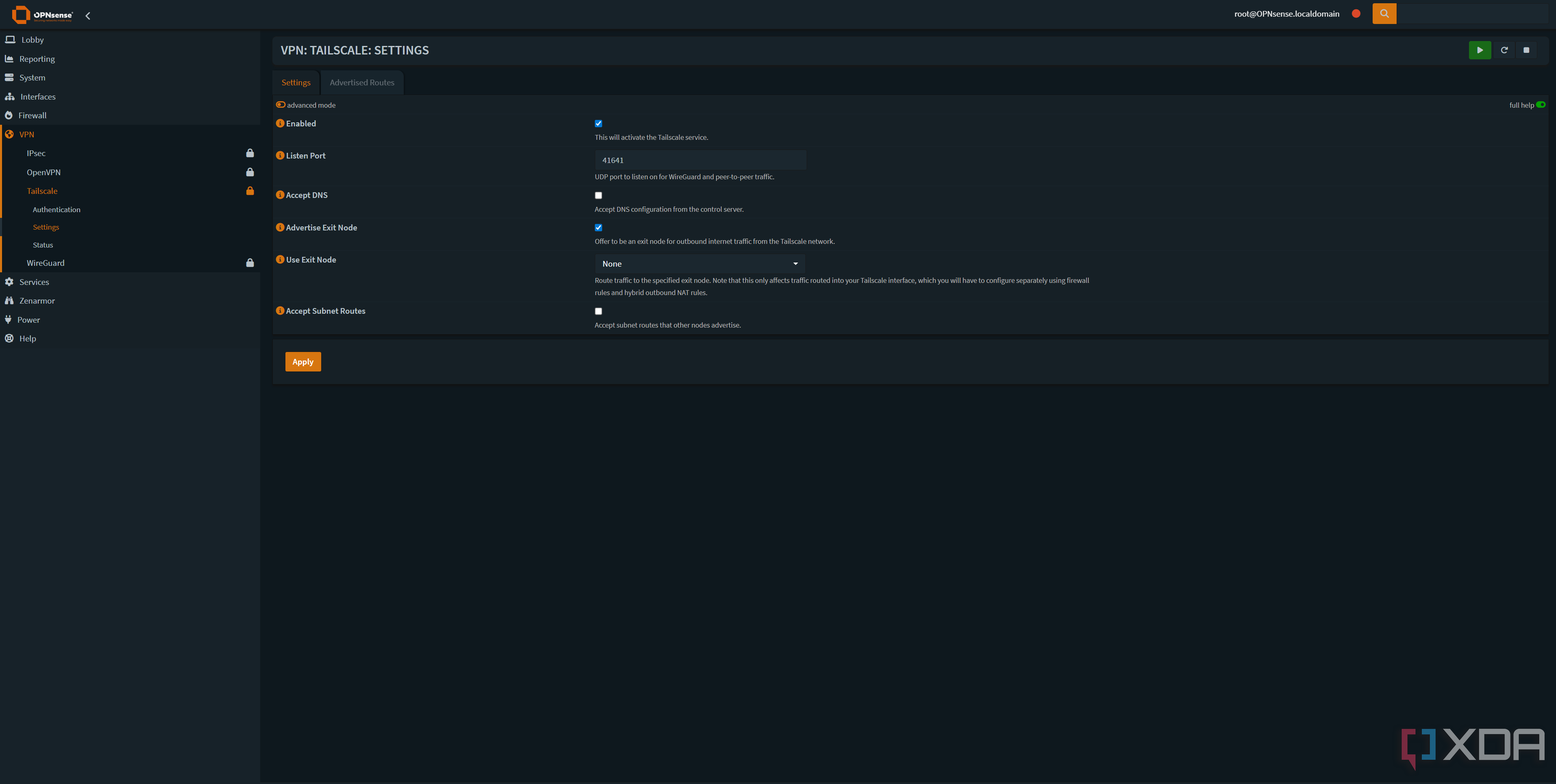
If you use Tailscale, you've probably experimented with the "exit node" option at some point. Basically, rather than routing traffic destined for Tailscale addresses, it routes all of your traffic to a specified device before going out to the wider internet. Think of it more like a traditional VPN, where you can be anywhere in the world, but browse the web as if you were at home.
While I previously used my NAS for this feature, it makes more sense to just use my OPNsense router. There are fewer hops, and again, it's one of those services that requires the internet to be working to be useful anyway. If my OPNsense instance is down, then I have bigger things to worry about than Tailscale. It's a natural fit.
2 Dynamic DNS
Keeping domains updated
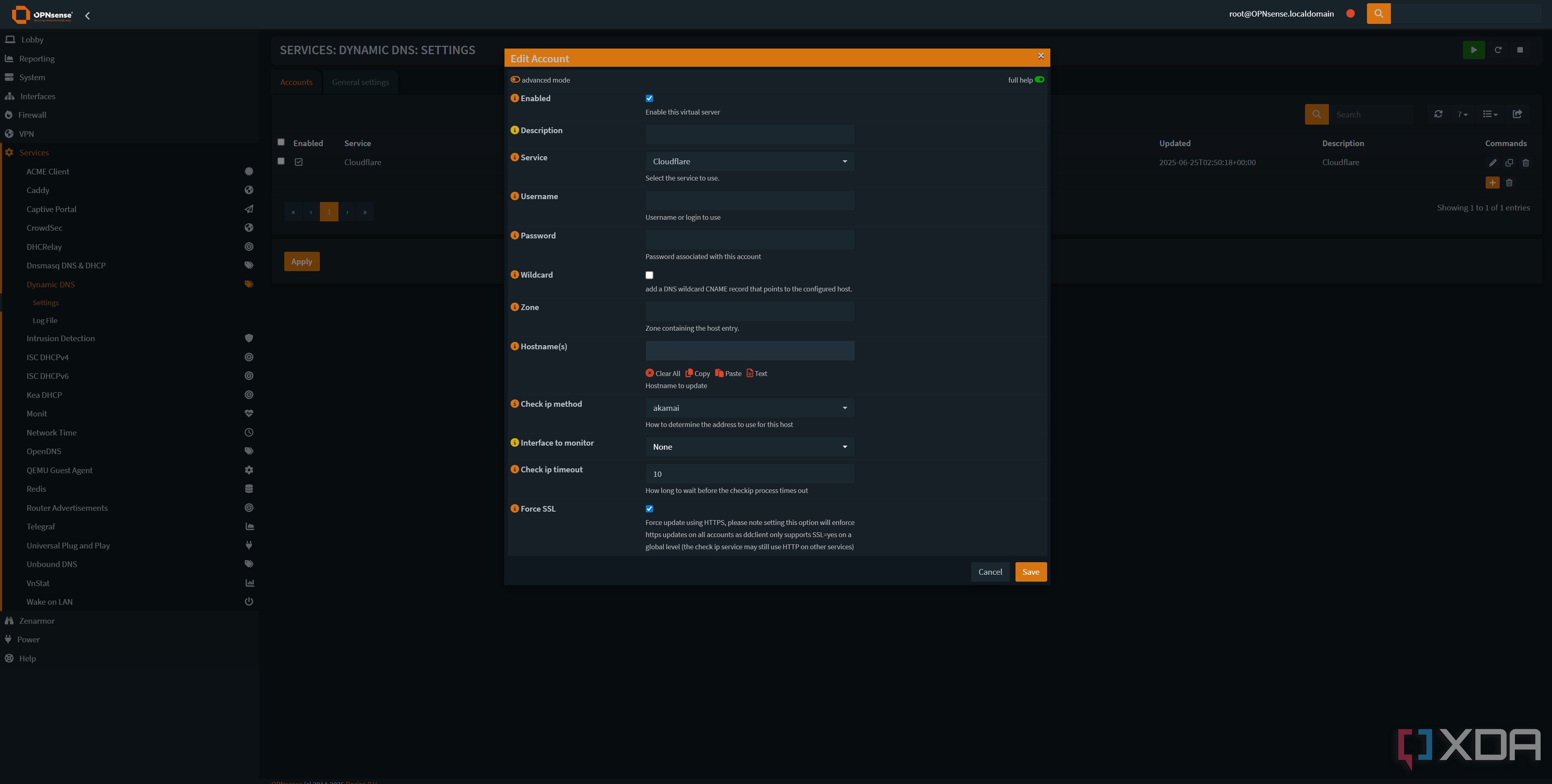
Previously, I had a separate container for updating my A records on my domain for pointing to my IP address, first using ddns-updater and then switching to cloudflare-ddns. However, I've since switched this configuration over to OPNsense, which has built-in support for dynamic DNS with multiple domains. It's another one of those configurations that just makes sense, because if I don't have internet, well, I probably don't have an IP address to reference for incoming traffic... not that incoming traffic could make a connection, anyway.
The beauty of it is that OPNsense supports a lot of platforms for dynamic DNS, along with support for custom GET, PUT, and POST requests if your service isn't listed. It works great with Cloudflare, and I've not had any issues with my A records updating when my IP address changes. They just work.
1 Wake on LAN
Though I also do it with Home Assistant
This one is a little bit different, but Wake-on-LAN is a pretty useful feature to have. I already use the Home Assistant Wake-on-LAN integration to boot up my server and my PC in the morning, but I don't have all of my devices set up, as I don't typically need it for them. However, I've used it a couple of times before deploying Home Assistant, and if my Home Assistant were either down or I didn't have the device configured already, it would be annoying in a pinch.
Thankfully, OPNsense has Wake-on-LAN built in, too. I can go to the DHCP list, copy out the MAC address of a device, and then send a magic packet to boot it up. It works wonderfully, and thanks to both OPNsense and Home Assistant, I've been able to sunset the container I had been originally using for that exact functionality.
OPNsense can do a lot
This isn't even everything that OPNsense can replace in your home network. If you use a Pi-hole, Unbound DNS supports blocklists, so you could even run Unbound on your OPNsense instance and use it as your DNS. I've yet to get around to doing this, but I want to try it in the future. Plus, you can even host a basic web portal on OPNsense, and a whole lot more. It's extremely versatile, and for anything that's critical to your network anyway, it's worth running it in OPNsense as if your OPNsense goes down, they'll fail either way.

Related
6 best self-hosted tools I have in my network stack
My networking setup is incomplete without these neat utilities
.png)











 English (US) ·
English (US) ·