I recently stepped foot into the world of self-hosting apps and services. Once I did, it didn't take me long to go down the rabbit hole of discovering new apps to host on my home network. Replacing Google Photos with Immich and using Obsidian in a web browser were all fun games until I realized that I can only access these services as long as I'm connected to my local network. So what about when I'm not at home and I want to check my notes or view my data hosted locally? I realized that to do that, I would have to expose these services to the internet. While I didn't have a problem doing that, I underestimated the security measures I would have to take into account to protect my data.
Since I was new to self-hosting and wanted to get things rolling quickly, I ended up exposing my self-hosted services without adequate precautions. Thankfully, I realized the risks early and made the necessary changes in time. However, you may not be as lucky as I am, and you may end up compromising sensitive information and data with strangers on the web. To prevent such mishaps, I decided to put together a checklist of sorts to take into account before your self-hosted services can be accessed remotely.
Secure authentication is non-negotiable
Strong passwords and MFA are key
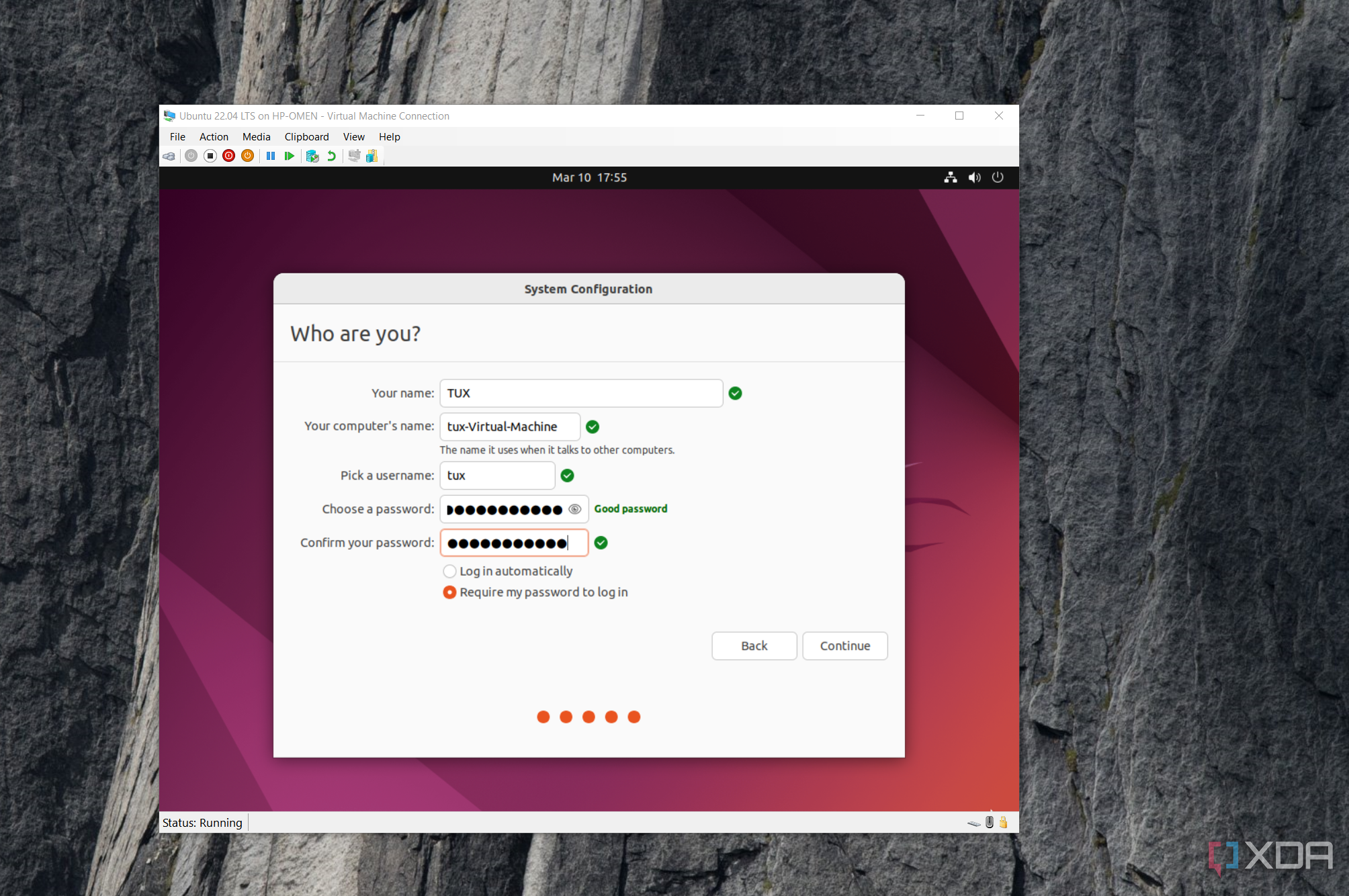
One of the most popular threats you face when you expose a service to the internet is unauthorized login attempts. So, just like your email or social media accounts, it's vital to set a strong password even for your self-hosted services. Use a combination of upper and lower case letters, numbers, and symbols. More importantly, don't use the default username and password linked to a service. Change it as soon as you set up an account.
Some other key pointers include using a unique password that you haven't used on another site and enabling multifactor authentication wherever available. Both of these can be tackled using a password manager and an app like Google Authenticator or Authy. For multiple services, it's wise to implement single sign-on with protocols like OAuth2 or LDAP.

Related
I self-host Bitwarden and here's why you may wish to do the same
Bitwarden is a must-have tool in your security arsenal, and here's why you should self-host it at home.
Use firewalls and network segmentation
Restrict traffic to necessary ports only
The best way to prevent an exploit is to control network access. Setting up a firewall can limit your hosted service's exposure, which can help prevent future breaches. Use tools like iptables or UFW to restrict traffic only to certain ports and block all others by default. In addition, use VLANs to separate services so that an attacker can't access all sensitive systems if one gets compromised.
Tools like OPNsense are perfect for this purpose since they provide enterprise-grade firewall capabilities. After setting up the required tools, it's advisable to regularly test your firewall rules with a service like Nmap to ensure only the intended ports are open.
HTTPS is mandatory
Obtain and renew certificates promptly

Man-in-the-middle attacks can expose complete data, including login credentials and inputs, if you're still on HTTP. This is because the data is unencrypted. Owing to this, HTTPS is no longer optional. Use automated solutions like Let's Encrypt to obtain and renew certificates. Additionally, tools like Certbot simplify setup for Nginx.
One thing to keep in mind, though, is that failing to renew your certificate may take your service offline, rendering it inaccessible remotely. So, set up an automation to renew the certificate every few weeks or months.
Update software regularly
All updates are good updates
Outdated software may not contain the necessary security patches to prevent newer forms of attacks. This is exactly why updating all your services to the latest version is key. Several vulnerabilities can affect the services you're hosting, the apps used to host them, and others on your computer. For instance, there's a chance Docker itself gets affected by malware. What then?
The only solution to avoid these mishaps is regularly updating all services and apps linked to your self-hosting routine. This includes updating your OS, web servers like Nginx, plugins, etc. Use tools like Watchtower to automatically update Docker containers to the latest version. Also, make a note of the version number of all your software, and look them up to see if there are any reported vulnerabilities that you can avoid.
Log and monitor all activities
Set up real-time alerts
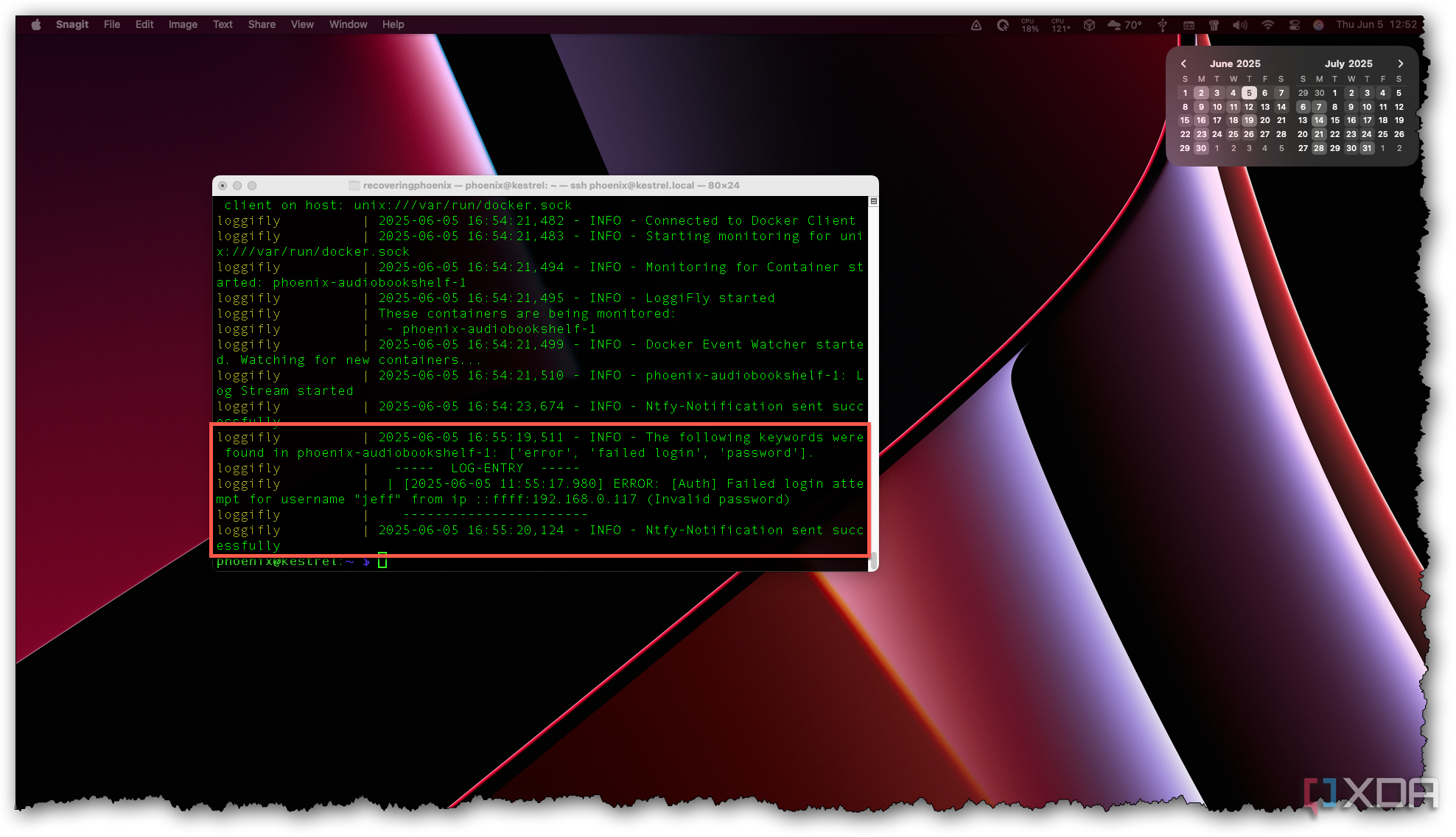
You need to have complete visibility into your system at all times to check what's going on and verify the state if things aren't going as planned. For logs, use a tool like Graylog to aggregate logs from all platforms — services, servers, and apps. You can use it to capture key events such as failed login attempts, configuration changes, etc.
You can also create a visual dashboard using Grafana to show real-time stats of CPU load, memory usage, etc. Sudden spikes without any usage or requests from your end can alert you to suspicious activity. Speaking of alerts, setting up alerts to be notified every time there are multiple failed login attempts or the disk is running low can be achieved using PagerDuty. It's also a good idea to go through the logs frequently, even if there aren't any alerts, just to double-check.
Protect your data
Taking care of these factors before exposing your self-hosted apps to the world can go a long way in ensuring there are no attacks or data breaches. Some self-hosted services like Immich and AdventureLog may contain private data like photos that you wouldn't want strangers on the internet to get their hands on. So, before you take any step as a beginner, it's best to sort out the security aspect and then go ahead with making the services live on the web.
.png)












 English (US) ·
English (US) ·