We tend to think of our personal computers as safe zones, especially when we have installed robust security solutions like antivirus and firewalls. But the truth is, hackers aren't always kicking down the digital door with brute force. More often, they're slipping in quietly through overlooked weaknesses, software loopholes, or social engineering tricks that feel totally normal until it's too late. The popularity and wide usage of Windows OS, along with its backward compatibility and broader attack surface, make it a common target for attackers.
Over the years, I've seen many cases of online security breaches affecting both personal and organizational Windows devices, and in almost every case, the breach could have been avoided with just a bit more awareness and better user habits (using the same passwords everywhere, are you?).
Let me walk you through the most common ways Windows PCs get compromised and, more importantly, what you can do right now to avoid becoming the next victim. This isn't just about installing antivirus software and hoping for the best; it's about understanding how attackers think and staying one step ahead.
Related
14 signs your Windows laptop has been hacked (and what to do)
Is your Windows laptop acting possessed? Check common signs that indicate a hacking attempt on your device
7 Phishing emails
Clicking the wrong email can open the door to major problems
Phishing remains one of the easiest and most effective ways for hackers to compromise a system. And yes, it's similar to actual "fishing": throwing a lucrative bait to catch the unaware fish. A carefully crafted email (bait) that looks like it's from your bank, streaming service, or even a legitimate software support might trick you (fish) into clicking a malicious link or entering your login info on a fake page.
These emails are often well-written and can spoof real email addresses, making them dangerously convincing. For example, "admin@amazan.co" or "alerts@bankofarnerica.com." Intruders also utilize subdomains to make the email address look genuine. For example, "admin@amazon.xyz.com." Here, xyz.com is actually the main domain, not amazon.com.
What you can do:
- Always verify the sender's email address, especially if the message urges immediate action.
- Hover over links before clicking to preview the actual destination URL.
- Never open unexpected attachments, even if they look like invoices or scanned PDFs.
- Use email services with strong spam filters and phishing protection.
- Enable multi-factor authentication for accounts tied to email.
- Most services, like banks, would never ask for your personal information via email or phone calls. So when you receive such emails or calls, question whether that makes any sense.
- Educate yourself and your coworkers or family on the latest phishing scams.

Related
I got my Steam account phished - here’s what I did to get it back
Phishing can happen to anyone, even those who know what to look for.
6 Malicious websites and pop-ups
Sometimes danger is just one click away from a search result
You don't have to visit the dark web to end up on a malicious site. Hackers use fake download pages, sketchy pop-up ads, SEO manipulation, and even cloned versions of real websites to trick you into downloading malware or entering sensitive information. One wrong click can lead to ransomware, spyware, or worse.
Similarly, you can also become a victim of fake software updates through malicious pop-ups. If you are getting "Update Flash Player" or "Update Chrome" pop-ups when visiting a website, it's an old trick used by cyber attackers to lure you into clicking malicious links. No legitimate software company will ask you to update its software on a third-party, unknown website. In fact, Flash Player is no longer supported by any browser, as Adobe discontinued it in 2021.
What you can do:
- Use a browser with built-in malware protection.
- Avoid visiting unknown or shady websites to download software and games.
- Install a reputable ad-blocker to prevent pop-ups and redirects.
- Be cautious of overly aggressive download buttons or fake "update your app" prompts.
- Check the URL carefully, especially when inputting credentials. Ensure the website you are visiting has an SSL certificate (HTTPS) and it matches the website.
- Only install updates from official sources (Windows Update, vendor websites).
5 Pirated software and cracks
If the software is free but should cost money, you're probably the product

Source: Christiaan Colen (Wikimedia Commons)
Cracked software and games can come bundled with malware, spyware, or trojans. Even if the software works as intended, there's no way to tell what kind of backdoors you've unknowingly installed on your machine. The usual targets are the technologically inexperienced ones who attempt to pirate software from dodgy websites.
Some of these programs may request administrative-level permissions. While these permissions can be legit, it's important to remember that you are granting high-level access to a program that you have downloaded unofficially, which means it may not be fully trustworthy.
Additionally, many cracks and keygens can disable your security programs or ask you to disable them. While they aren't technically malware, their ability to make system-level registry changes causes security solutions to flag them as such. In these situations, you need to figure out whether using the crack is worth the risk to your system's privacy.
What you can do:
- Avoid pirated software if you have a choice; trust me, it's not worth the risk.
- If you are a college student or on a tight budget, use free or open-source alternatives to popular paid software.
- If you must test unknown files, use a sandbox or virtual machine.
- If you have downloaded files from unknown sources for any reason, scan them using services like VirusTotal before opening.
- Keep legitimate installers backed up in case you need to reinstall.
4 Using weak passwords and reusing passwords
One bad password can unlock your entire digital life
Using weak passwords like "qwerty123" or reusing the same login password across multiple accounts is practically an open invitation for attackers. Once one service is breached, attackers can try that same combo on email, banking, cloud storage, and social media accounts.
On top of that, credential-stuffing bots can automate this process, making it super-fast, so that you don't get much time to protect your accounts. Because of such an easily avoidable mistake, you can practically lose all or most of your online accounts.
What you can do:
- Regularly check your passwords on HaveIBeenPwned to determine if your email, password, and other personal information have been compromised in a data breach.
- Use strong, unique passwords for every single account.
- If you tend to forget passwords (like me), use an authentic and popular password manager to safeguard and even generate your passwords.
- Don't rely on browser-based password managers if you're sharing the device. They aren't secure password managers.
- Enable multi-factor authentication for extra protection.
- Change passwords immediately if you find out a service you use has been breached.
3 Outdated software and Windows versions
Old software is full of holes that hackers already know about
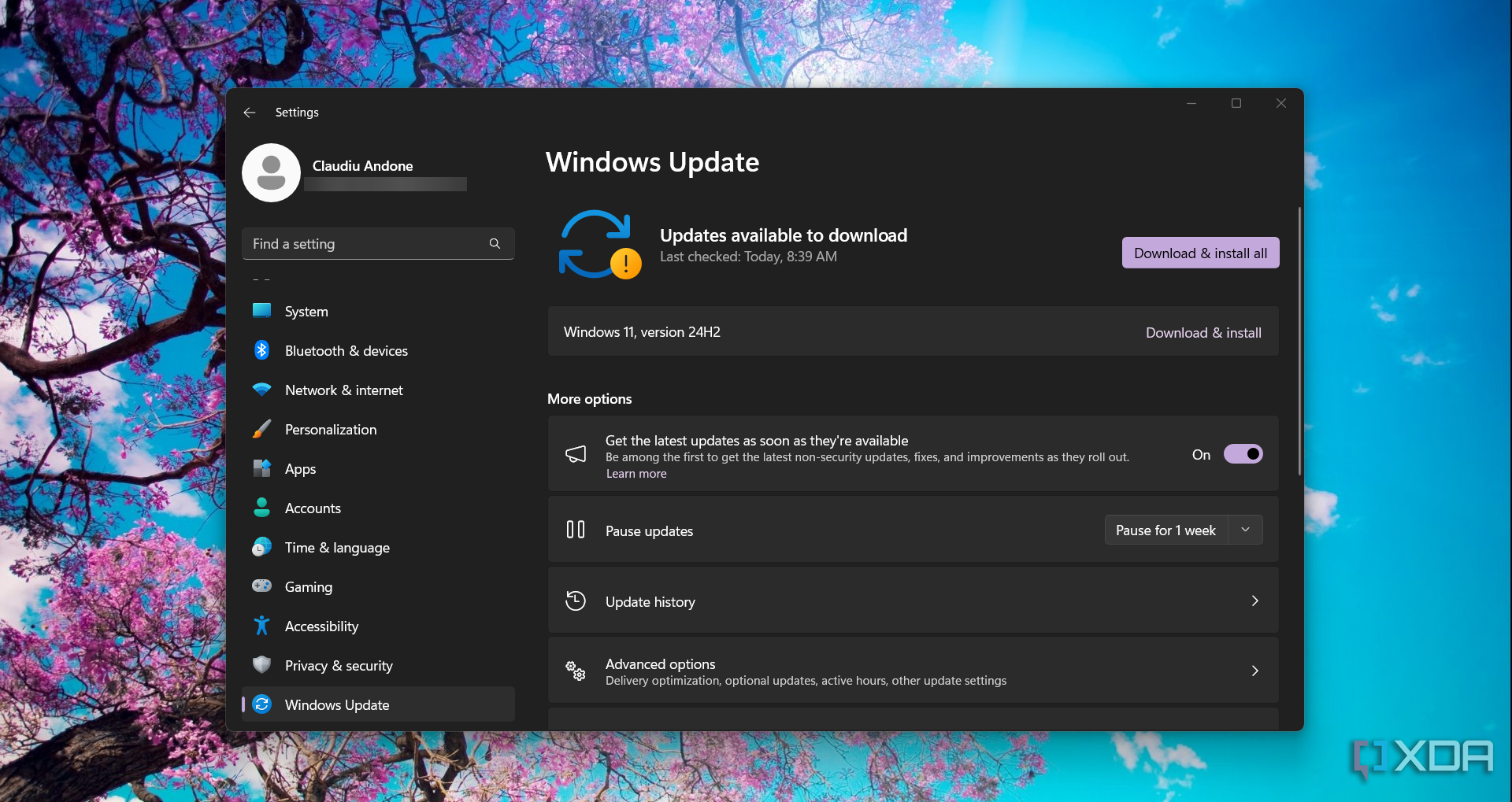
Running outdated versions of Windows or skipping updates for your software leaves you exposed to known vulnerabilities. There's a reason Windows updates too much. Microsoft releases important security patches through updates to secure your OS. Similarly, popular apps like Chrome also release security updates from time to time to resolve vulnerabilities. Cybercriminals often target systems that haven't patched recent exploits.
An example of this is the spread of the WannaCry Ransomware attack. It exploited a vulnerability in Windows' Server Message Block (SMB) protocol, specifically through an exploit called EternalBlue. Microsoft released a patch for this vulnerability in March 2017; however, the attack occurred in May 2017 and affected more than 200,000 devices across 150 countries simply because they had not updated their systems to install the patch.
What you can do:
- Always install critical Windows updates as soon as they are available.
- Enable automatic updates for major applications you use daily and essential drivers.
- If it's too lethargic for you to check for software updates manually, use legitimate software and driver updater apps.
- Uninstall software you no longer use. It reduces your attack surface.
- Upgrade from unsupported Windows versions like 7 or 8.1 to at least Windows 10 (best to upgrade to Windows 11, if your hardware supports it).
Related
4 reasons Windows XP is so insecure nowadays
Everyone knows Windows XP is insecure, but these are the exact reasons why.
2 Malicious USB devices
Not all flash drives are friendly

Plugging in an unknown USB device is risky, especially ones you find lying around or receive unexpectedly. Hackers can preload USB sticks with malware, use them to steal files, or even execute pre-programmed scripts automatically using USB emulation. Some attacks go even deeper, using what's known as BadUSB payloads.
BadUSB attacks involve reprogrammed USB devices that act like keyboards or network adapters. Upon being plugged in, these devices execute malicious commands, such as installing malware or changing security settings without user interaction.
An example is the FIN7 hacking group, which mailed USB drives disguised as promotional items to compromise victims' systems. Another threat is the USB Killer, which delivers high-voltage pulses to damage computer components.
What you can do:
- Never plug in untrusted or unknown USB devices.
- Disable autorun and autoplay features in Windows settings.
- Use a USB data blocker (a.k.a. "USB condom") when charging devices in public.
- Set up your system to prompt before recognizing new removable devices.

Related
The Flipper Zero's BadUSB can do anything on your computer just by being plugged in
BadUSB can do a lot of good, but it can also be used for a lot of evil. Here are some of the uses for it.
1 Browser extensions gone rogue
Your handy extension might be selling your data or worse
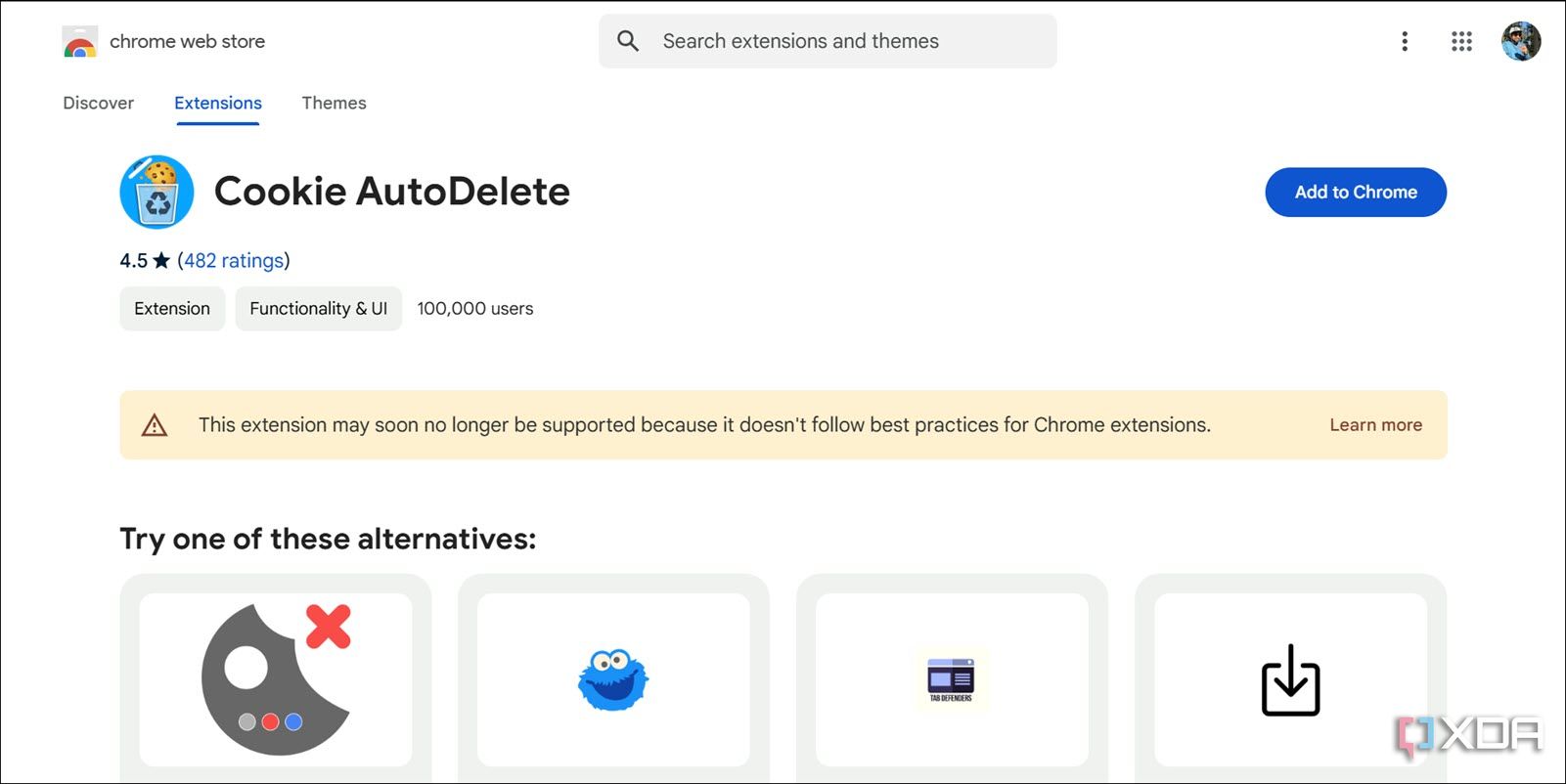
Some browser extensions start out useful but get sold to shady companies who turn them into adware or spyware. Others may request unnecessary permissions to track browsing habits, inject ads, or steal login info. The fake software update alerts we previously discussed can also appear due to a browser extension going rogue.
What you can do:
- Only install extensions from trusted developers and marketplaces.
- Check reviews and extension permissions before installing.
- Regularly audit your extensions and remove anything you don't use.
- Avoid extensions that require access to all websites unless absolutely necessary.

Related
5 popular extensions that won't work on Chrome soon, and their alternatives
These popular Chrome extensions will stop working due to Manifest V3 changes. Learn why and discover alternatives to keep your browsing seamless.
Your best defense starts now
Nowadays, staying secure is not just about installing antivirus software and relying entirely on it. It's about creating smart digital habits, knowing the common threats, and keeping up with the ever-changing tactics used by cybercriminals. If you implement even a few of the tips in this article, you'll dramatically reduce your risk.
Clearly, you don't have to be a cybersecurity expert to protect your Windows PC, but you do need to stay sharp. Most hacks don't happen because people are careless; they actually happen because people don't realize they're walking into a trap until it's too late. Remember, being cautious about your PC's privacy and security isn't paranoia; it's common sense.
.png)













 English (US) ·
English (US) ·