Like many, I suffered with an ISP-provided router for many years—more than I wish to admit to, really. After tracking its performance for a while, I decided it was time to kick that useless box to the curb.
In its place? A custom router running OPNsense, where I can change what I want, add what I want, and more importantly, remove what I don't want. It's perfect for the level of dabbling, tinkering and generally poking at tech that I'm used to, and I can't wait to see what else I can add to it in future iterations.
8 Robust security options
Nobody should be on my network but me
The default firewall and other security features of consumer-level routers are sadly useless. That's perhaps even more so for ISP routers, as you can't often see what's being done on your behalf, and your ISP sure isn't going to tell you otherwise. But with OPNsense as a baseline, I can add industry-standard security packages to tighten things up, and monitor traffic in and out of my network to spot any anomalies. It doesn't make me safer on its own, but it gives me the tools I need to be safer, and that's what counts.

Related
5 essential firewall rules every home lab should have
Before you start playing with services and tools, here's what you should set up first.
7 Run my own internal DNS server
Unbound means I don't need a domain for reverse proxy use
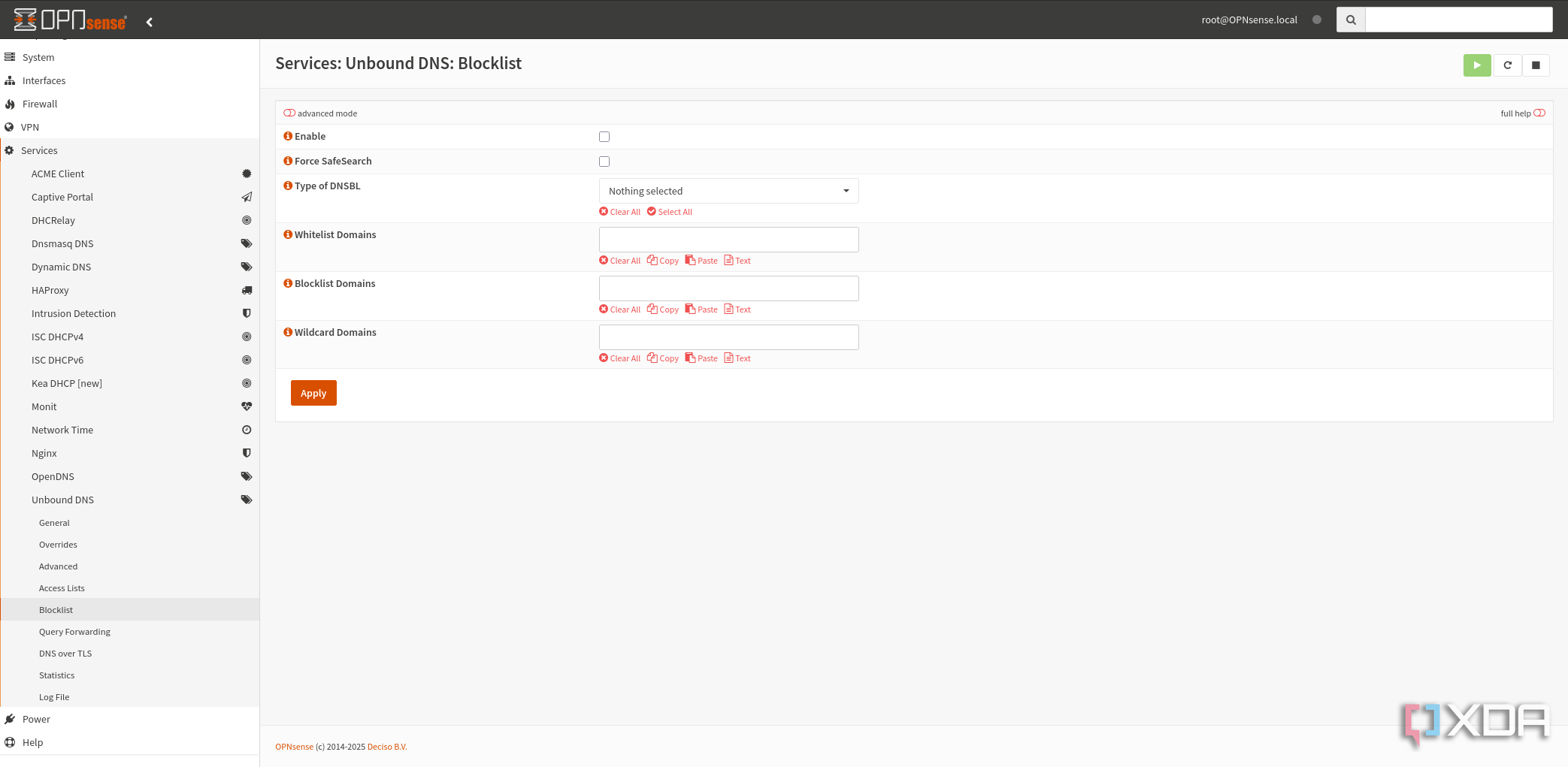
While adding Unbound to self-host my DNS server comes with a host of privacy and security benefits, there's only one thing I want it for at home. No, not DNS caching, although that's handy, but the ability to make domains for use inside my network. That makes handling reverse proxies simple, because I don't need to own the .TLD I'm using, and it stays alive for users on my network even if the internet goes out, which is a fairly common occurrence in my neighborhood.
6 Keep my home lab separate
My home network doesn't need those shenanigans

I've been building up my home lab lately, and the most crucial part is ensuring it doesn't affect the other users in my household. That meant I needed a way to keep it off the main network, and setting up a VLAN and some firewall rules accomplished that in no time. That's not something I could have done on any of the consumer or ISP routers I've used over the years, and the versatility of OPNsense is winning me over big time.

Related
5 essential firewall rules every home lab should have
Before you start playing with services and tools, here's what you should set up first.
5 Use VLANs for other annoyances
Yes I mean my IoT devices
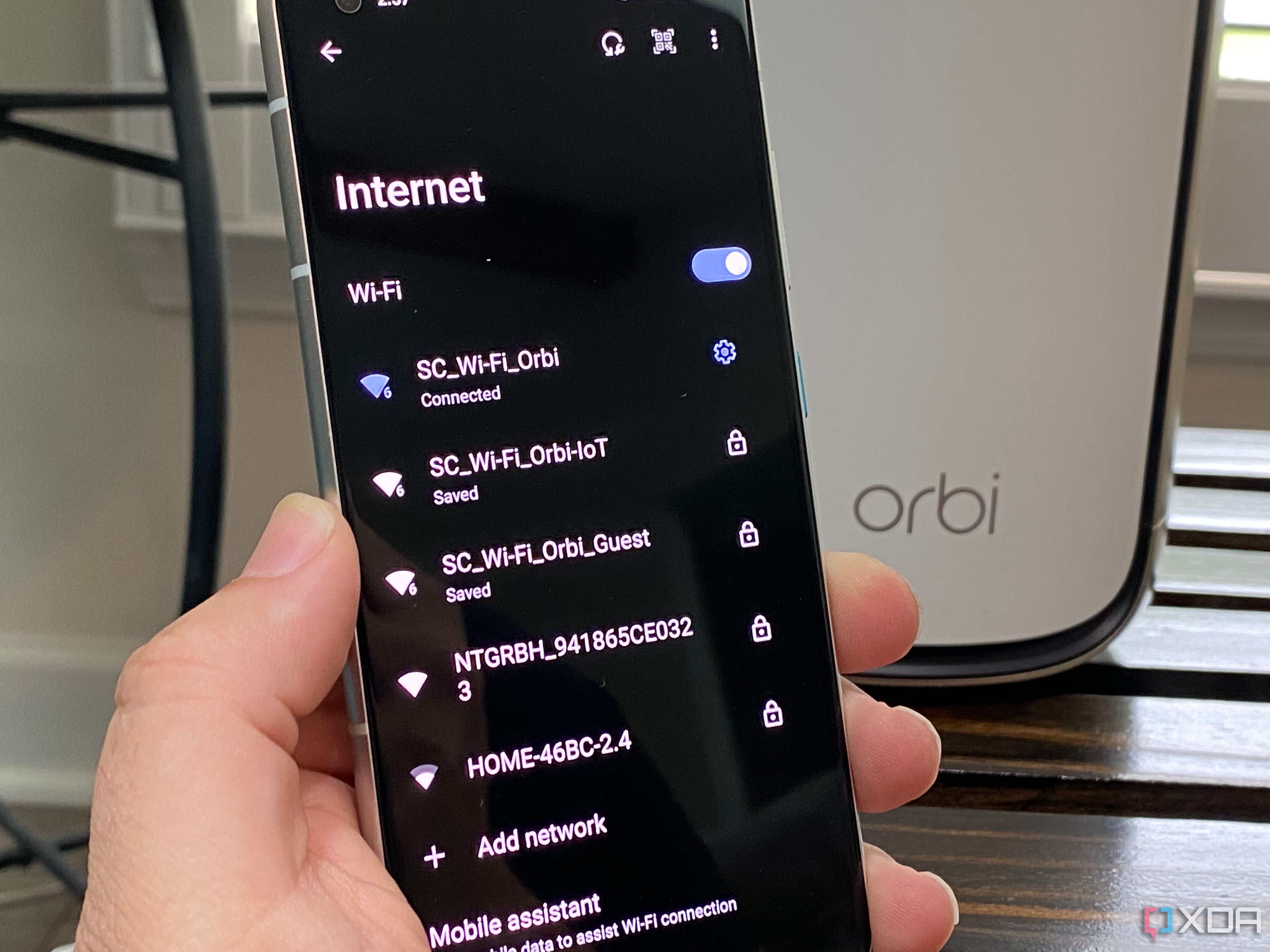
You know the fun thing about VLANs? Okay, there's nothing fun about VLANs, or most networking features, but they sure are handy for making your internet flow to the right devices at the right time. Putting your smart home controls on a mini PC hub that's then on another VLAN with every IoT device saves your other networks from excessive broadcast chatter, and just might save it from malicious actors too. Let's not forget that the biggest botnets were made from IoT devices and old routers, and by using OPNsense and a VLAN for smart home devices, you remove both of those from the equation.

Related
VLANs finally fixed my smart home headaches
I might have traded one headache for another, though...
4 Plenty of plugins
I can add more features with a click
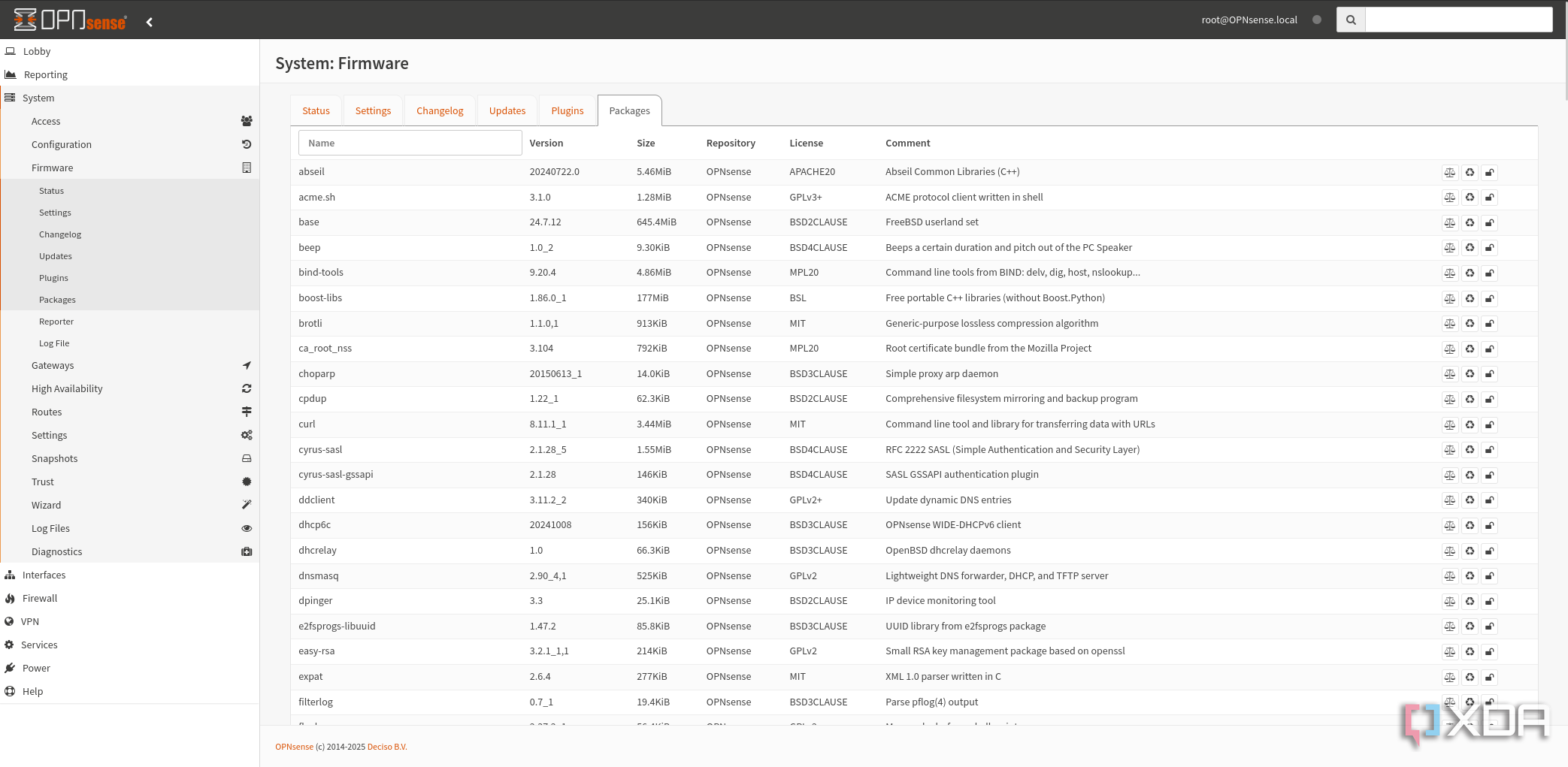
The extensible nature of OPNsense means I can improve it at any time by adding plugins from the store. I highly recommend you do so because you can quickly add security packages, proxies, and other useful packages. While my ISP router was configured to protect my network from *gestures at the internet*, it was lacking in the advanced features that I wanted, like DNS caching, IDS/IPS, and more control over the rulesets the firewall uses. It's not much of a stretch to say you need to add plugins, because you do, OPNsense or pretty much any custom firewall software is pretty barebones when you first install it. You're given a skeleton to build the security appliance you want, not a prebuilt one that might be restricted from features you'd like.
Related
8 things I always do after installing OPNsense
Here's a checklist of things to do with your fresh OPNsense firewall.
3 Regular updates
Seriously, routers need better support
I can count on the fingers of one hand how many times I remember my ISP updating the networking equipment they provided me, and several of those times left me with no internet as the update botched things. With OPNsense, I get regular updates even on the free license with a pop-up reminder when I log into the dashboard. If I pay for a license, I get more regular updates and it helps support the project, which is a big thing because we need viable open-source security options for home lab and enterprise use.

Related
Should you use OPNsense or pfSense in your home lab?
Which open-source firewall software should you be picking?
2 Improved reliability and performance
Consumer routers are not built well
Consumer routers are built to parametric lists, aren't cooled well (if at all!), and generally don't last that long. They're not designed to last long, whether from a hardware or software perspective. But OPNsense runs on a very wide variety of hardware, from old PC parts to custom-built boxes, and can be reconfigured or rebuilt at any time. Plus, you can virtualize it if you want, and abstract away driver issues while putting it onto a high-availability cluster so that your firewall and router never go offline, even if part of the hardware it runs on fails. That's on my to-do list, and then I don't have to worry about anything except backup power.

Related
4 hardware requirements I would never skimp on when building my own OPNsense or pfSense router
If you're looking to build your own router and firewall, these are the most important components you need to worry about.
1 I'm in control
This is really the most important part
I have a few maxims that my home lab runs on, and they're just as important for my home network. But the main unspoken rule is that I should be in charge of my network, not an outside party. That means no ISP access, no service provider, no ISP DNS records, and so on. I know that means I'm the person who gets the blame if anything goes wrong, and that's also okay. I'll gladly pay for some things, so I don't have to handle them, or because the cybersecurity teams maintaining plugins are far better at it than I ever would. But at the end of the day, the more I learn about security, the more I want to practice better security to learn even more.
I'm never going back to a consumer router ever again
While there's an argument to be made about the ease of use of consumer routers, they're not more complex than OPNsense, and often have worse technical documentation when something goes wrong. I've set up OPNsense for my home lab to get familiar with it, but it'll be taking over as the house's main router soon enough, probably in a Proxmox HA cluster to ensure uptime of the network and associated services. I love it, and while I might play with other manufacturers' hardware, I'm never looking back.
.png)












 English (US) ·
English (US) ·