
Sign in to your XDA account
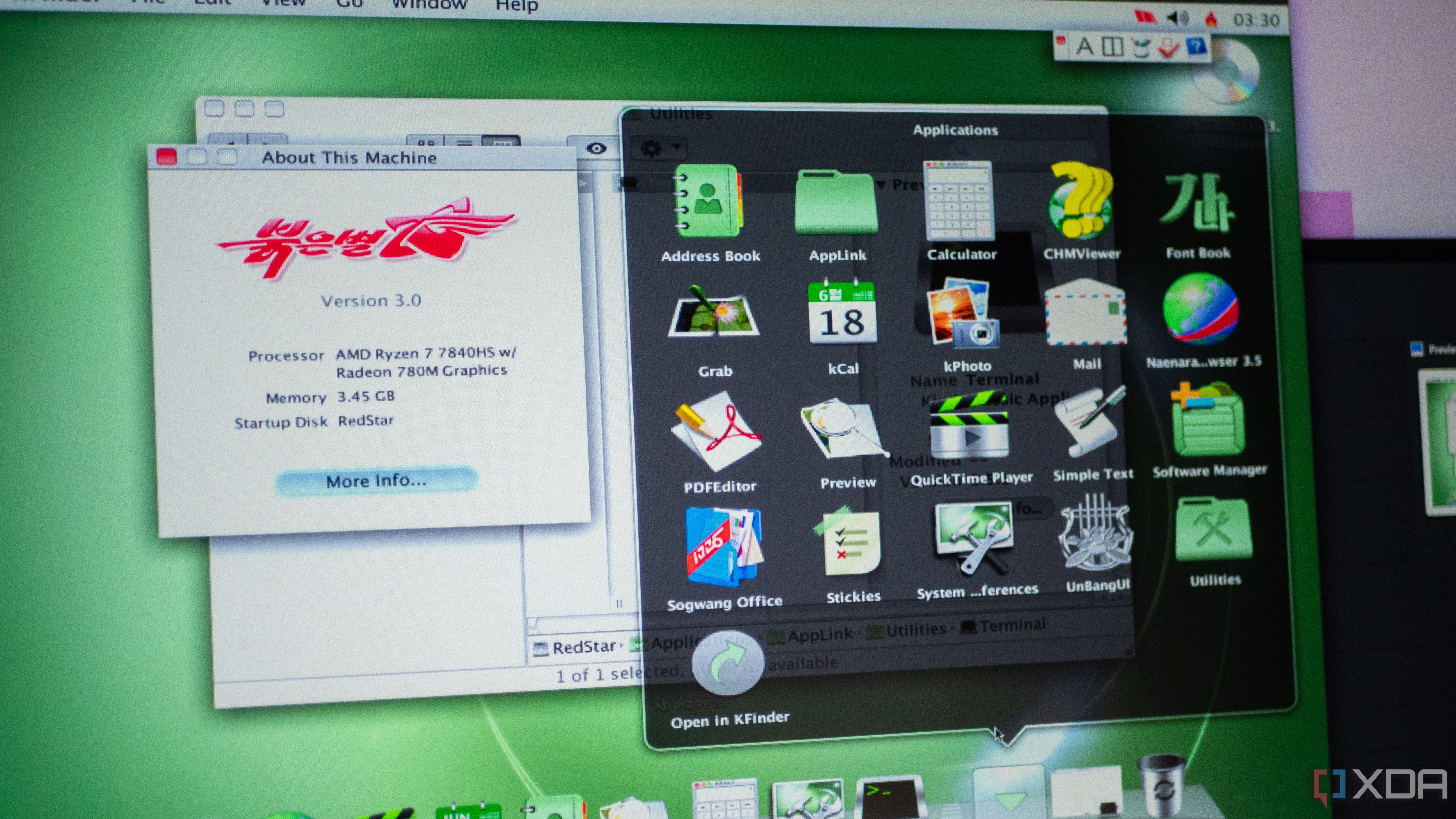
North Korea is an interesting country to look at from a technology perspective. Under the regime, its citizens are entirely cut off from the outside world, and entry to the country is severely restricted; all that we know is essentially pieced together from a combination of satellite imagery, defectors from the nation, and reports that can often be contradictory. That's why Red Star OS 3, a Fedora-based Linux distribution developed by North Korea, is especially fascinating. It's a rare glimpse into an otherwise largely unknown world, and I set it up in a virtual machine.
Of course, Red Star OS 3, the version we're showing off here, leaked just shy of a decade ago. In fact, its successor Red Star OS 4 is apparently based on Ubuntu, though that particular version has found its way into the hands of few journalists and can't be downloaded publicly. Given that a decade has passed, and there's no shortage of information about Red Star OS 3 these days scattered across the internet, I felt it was worth exploring to highlight some of the most peculiar aspects of the operating system, and what it shows about the reclusive country that we otherwise know little about. It turns out there's more to find yet, as I discovered some functionality that I hadn't seen reported elsewhere.
For those looking to embark on a journey with Red Star OS, it's important to know a few things. First, as you would probably expect, the operating system is heavily locked down out of the box, tracking what files users access and blocking access to the wider web. Secondly, if you plan on running it yourself, it would appear safe to run the operating system on your home connection with limited internet access, given what we know about it now, but it would still be advisable not to provide the operating system access to your home internet connection at all.
For the purposes of testing, in VirtualBox, I've not given Red Star OS a network adapter. To be honest, though, there isn't a whole lot to worry about when running it. While VM escape can theoretically be possible through a virtual driver created by the VM, it's incredibly unlikely that a ten-year-old operating system that's been studied relentlessly is still capable of exploiting a modern environment. Plus, its primary connections are all aimed at the North Korean intranet, so it doesn't appear capable of phoning home either.
What is Red Star OS?
An interesting history
Red Star OS, as we've already established, is a Linux distribution developed in North Korea. It began development in 1998, and the first version of it appeared in 2008 with a very Windows XP look and feel. Red Star OS 2 was released in 2009 and also resembled Windows XP. However, Red Star OS 3, the version we're looking at here, drastically switches up the user interface to resemble macOS instead.
It's a typical Red Hat/Fedora-based Linux distribution for the most part, though it contains preinstalled software and a Korean language package localized with North Korean terminology and spelling. It's possible to switch the language of the OS to English with root access, and there are installers that have been modified to switch the installer to English as well.
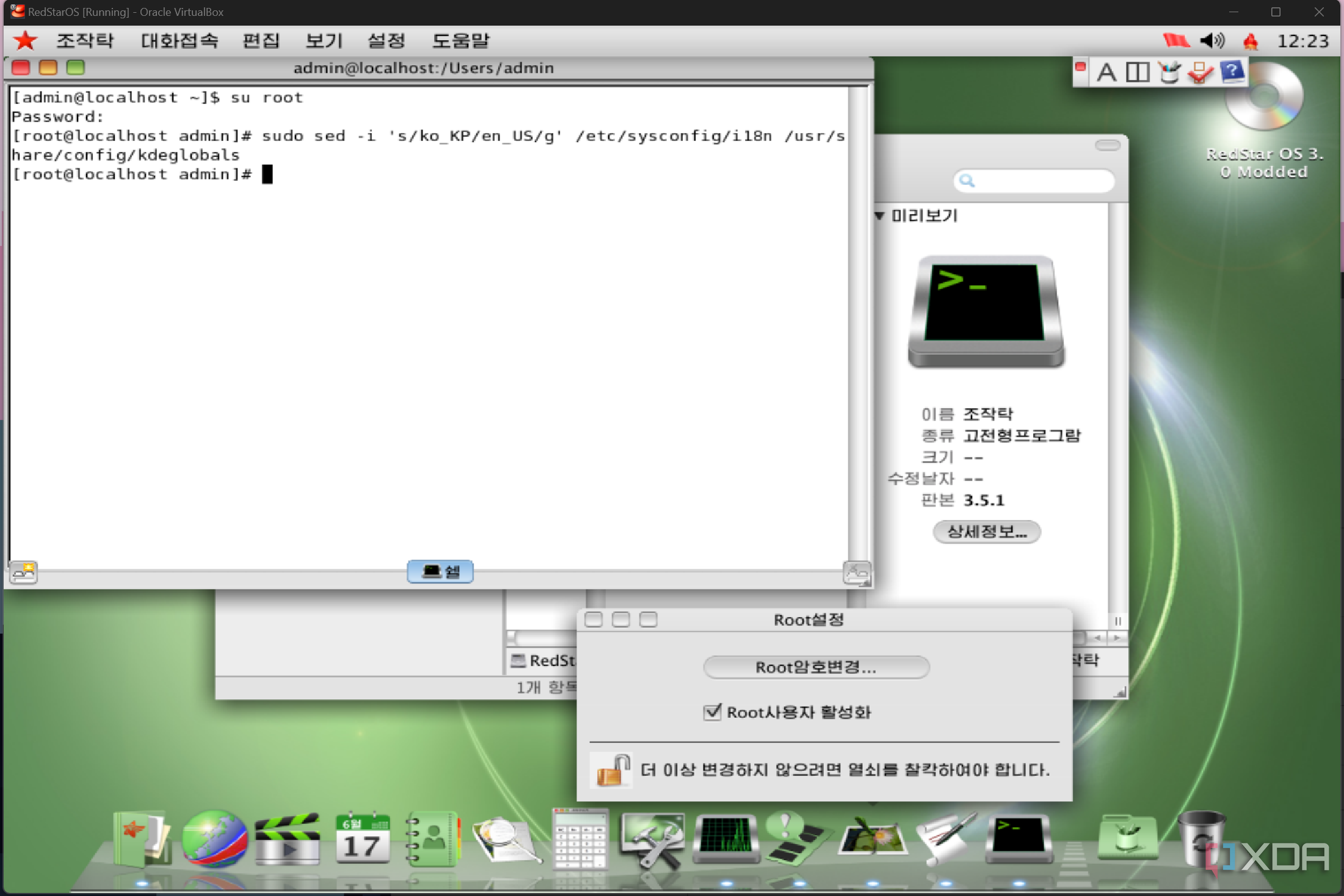
The user-facing preinstalled software includes a browser based on Firefox called Naenara (meaning "My Country"), a text editor, an OpenOffice clone called Sogwang Office, a media player (referred to as QuickTime when using the OS in English), a file sharing application, and some basic games. There's also a music application, called UnBangUl, a name that matches a major North Korean accordion brand. Wine is also preinstalled to allow for Windows applications to run.
However, look below the surface, and there's significantly more software ticking away under the hood. Files are automatically watermarked, system files are protected and the system will reboot if an unauthorized change is detected, and a hidden "antivirus" software can delete specified files. Snort also comes preinstalled, though it's not enabled by default, and iptables rules do the following:
- Allow certain inbound services like HTTP, HTTPS, SMB, and drop the rest
- Defines an allowance of reply traffic to those services
- DNS requests can be made, but replies won't be accepted as the iptables make no reference to sport 53 or dport 53.
- mDNS/Bonjour are explicitly accepted via port 5353
For the most part, Red Star OS is an unremarkable operating system on the surface. Once you've gained root access to the system and can install your own applications unrestricted, along with uninstalling the preinstalled spyware designed to monitor users, it's just a reskinned Fedora, and that's about it. Getting modern versions of package managers running on it can be a tall ask, and especially now, it's far too out of date to really be usable.
Yet, there are some aspects of the system that raise questions throughout. Some of the biggest are with Naenara, the Firefox-based browser that comes preinstalled.
What Naenara can tell us about North Korea's internet
Or, rather, intranet
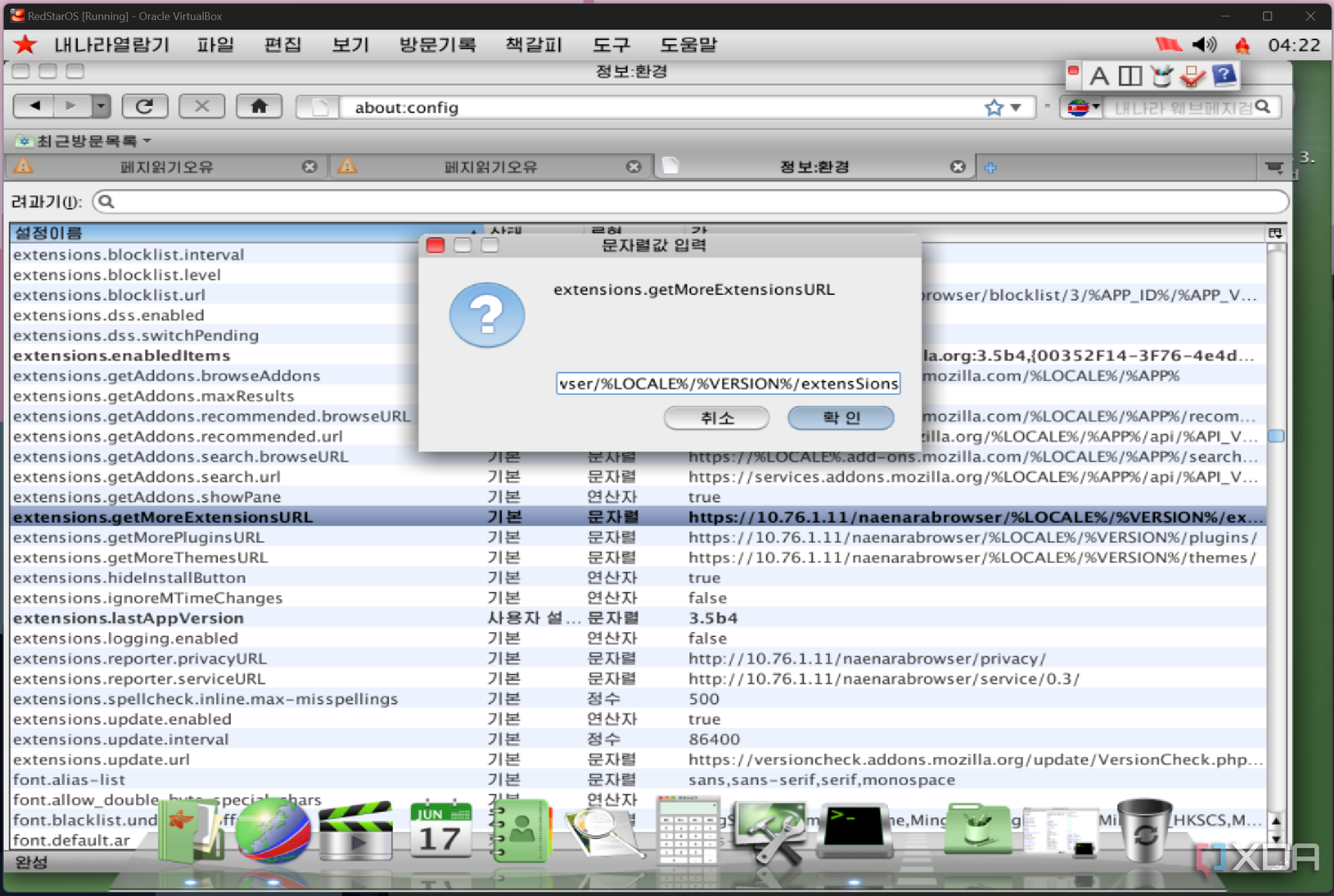
When first launching Naenara, the default home page is the IP address "10.76.1.11." This is an internal IP address reserved by IETF and IANA as specified in RFC1918, and you'll often see "10.x.x.x" addresses used within corporations or home networks. While it's widely known that North Korea has an intranet known as Kwangmyong, this gives us a bit of insight into how devices might communicate. For further context, Will Scott, a former lecturer at the Pyongyang University of Science and Technology, stated that the country appears to have its own DNS system with its own top-level domains (TLDs). These include TLDs that don't exist on the wider web, like .web and .rec.
Scott also stated that most end-user computers he saw were running Windows XP and a few used Windows 7, and that Red Star was not something that he had seen in many places. His theory was that Red Star is used more as an industrial operating system rather than one designed for end-users, and that most computers he had seen in his time in North Korea appeared to be imported from China.
As for Naenara's internal IP address being a default IP address, it makes a lot of sense. North Korea has been officially allocated just 1,024 IP addresses from APNIC, and its range is 175.45.176.0/22. There are two additional blocks assigned to it under the control of China Unicom (210.52.109.0/24) and the Russian satellite company SatGate (77.94.35.0/24), though this still adds up to be a very small number of addresses for a country of 26.42 million (as of 2023). This isn't much of a problem for North Korea, though, as global internet access is heavily restricted in the region to high-level government officials, some Korean Computer Center employees, and some academics for the purposes of research. This internet access is also strictly monitored.
As for the certificates used by the browser, the root certificates have a country issuer code of KP, the ISO 3166-1 Alpha-2 code for North Korea. This makes sense; Scott stated that network requests required the use of an HTTP Squid proxy at a campus level, and every request was associated with his username. With North Korean certificates, the issuer who would have the private key could man-in-the-middle all "encrypted" requests. Interestingly, Scott noted that while his internet usage was unfiltered, graduate students and professors at the university had access to the wider internet just like he did, though theirs was filtered, and a lab proctor would watch over users in a special room of the campus designated for that outside browsing.
Taking a look at about:config in Naenara, it seems that many Google and Mozilla URLs were simply replaced with an internal IP address, as there are still Mozilla and Chrome-related flags addresses that follow the exact URL path of a typical request, though with the internal IP placed instead. Interestingly, it appears that there are official extensions that can be installed, and the default search engine replaces Google's domain with the internal one noted previously. Unless basic built-in functionality that can be accessed is broken on the North Korean intranet, the logical conclusion is that internal services are likely modeled after existing services from outside the country.
Finally, automatic update checking can't be switched off. However, you can set it to "always ask" before an update is installed. Out of the box, it will automatically install updates, though.
Applications in general are quite strange on Red Star OS 3
There's even an encryption utility, though it's only accessible by root users
In navigating the OS and seeing what I could find, I discovered an application called "Bokem." This is an encryption utility that implements a 128-bit block cipher based on AES called Pilsung. As it turns out, the cipher itself appears to be fairly secure, though its implementation within Bokem likely isn't. Having said that, you do need root access to use it, so it might be the case that nobody is expected to use it at all. Launching this in a VM required prefixing the launch command with "DISPLAY=:0".
What's more interesting is the actual layout of applications. It's not just the OS that has a macOS look; applications themselves are stored in a manner similar to applications stored on macOS. In Red Star, they're located under /Applications, and each application is in its own ".app" folder. For example, "QuickTime" is in the QuickTime.app folder, which contains a Contents folder, a Resources folder, and a "RedStar" folder, which contains the actual executable.
There's not much really to see from the applications side of things that we haven't already gone over. However, I took some time to dig into one of the utilities designed to spy on users, and there were some interesting things still left to find that I haven't seen reported elsewhere.
Dissecting scnprc
The "anti-virus" running on Red Star OS
There are two core components to Red Star's total system lockdown. The first is scnprc, which scans files, and the second is opprc, which actually does the watermarking of those files. However, scnprc does some pretty interesting stuff too, and I took it into Ghidra to analyze some of its functionality. I looked at the following functions in the binary:
- WriteHiddenEncodeFile
- WritePatternToUSB
- WriteImageInformation
- ImageProcessing
- get_disk_serial
- ScanCD
- checkfile
It is unclear which of these functions are actually used, but these functions exist in the binary and can theoretically be executed at any time.
The most interesting discoveries I made were in WritePatternToUSB and ScanCD. I have not seen either of these discussed in relation to Red Star OS before, though their activities would have been broadly assumed. We'll first look at WritePatternToUSB.
WritePatternToUSB
WritePatternToUSB is a massive function that took a while to decipher, but essentially, it does the following:
- Sanity-checks the file system by checking if the drive can be opened, reading the first 64 bytes, and confirming with a helper function whether it looks like a FAT32 file system
-
Reads FAT32 fields from the file system. This includes:
- FATSz32/DrvNum: offset 0x24 (36) for the FAT type. This will be DrvNum for FAT16 or FATSz32 for FAT32.
- BPB_RsvdSecCnt: Offset 0x0E (14) for reserved sector count
- BPB_BytsPerSec: Offset 0x0B (11) for bytes per sector
- BPB_FSInfo: Offset 0x30 (48) for start sector of FSINFO
- Reads FSINFO sector
- Computes a byte offset to delimit the FAT area
- Checks for a pattern with the information gained from the file system
- The pattern is either updated, or a new one is created
I was unable to determine what exact pattern was being written, though I could see that it takes in a "tmp.tmp" file with the data required. I suspect this is either supplied by opprc, or was never fully implemented. The function would seek to fatStart+clusterIndex*4, write a 4-byte value at that array position, and work its way through an in-memory cluster map.
ScanCD
ScanCD is another interesting function, but thankfully, a lot simpler to understand. It appears that it gets called when a CD is inserted into the system, and does the following:
- It scans every directory on the CD inserted
-
Every file found is passed to a checkfile function
- checkfile calls another helper process to analyze the file
- The response from the process fills a local variable
- Checks for different file types based on the description received
-
Under very specific conditions, a value of -1000 can be returned
- In this case, the CD is ejected
- The offending file path is logged
- A GUI warning is displayed
- The system is rebooted after 1000 seconds
checkfile recognizes the following files:
- Image: JPEG image data, TIFF image data, PNG image data, GIF image data, bitmap data
- Audio (lossy): MPEG ADTS, Wave audio, Microsoft ASF, MP3, "very short"
- Video/container: RIFF (little-endian) data, MPEG sequence, RealMedia, QuickTime movie, Macromedia Flash (Video)
- Plain text/source: UTF, Unicode, ASCII, generic text
- PDF documents
- CHM help files
- DjVu images
-
CNKI CAJ ebooks
- This is a publisher in China that publishes academic papers
- Office 2007 and OOXML
- Hangul Word Processor
- Superstar/Founder PDG ebooks
These don't trigger the warning and a shutdown alone. I was unable to confirm what exactly triggers it, and I suspect this is also dictated by an outside service, as there are multiple process calls.
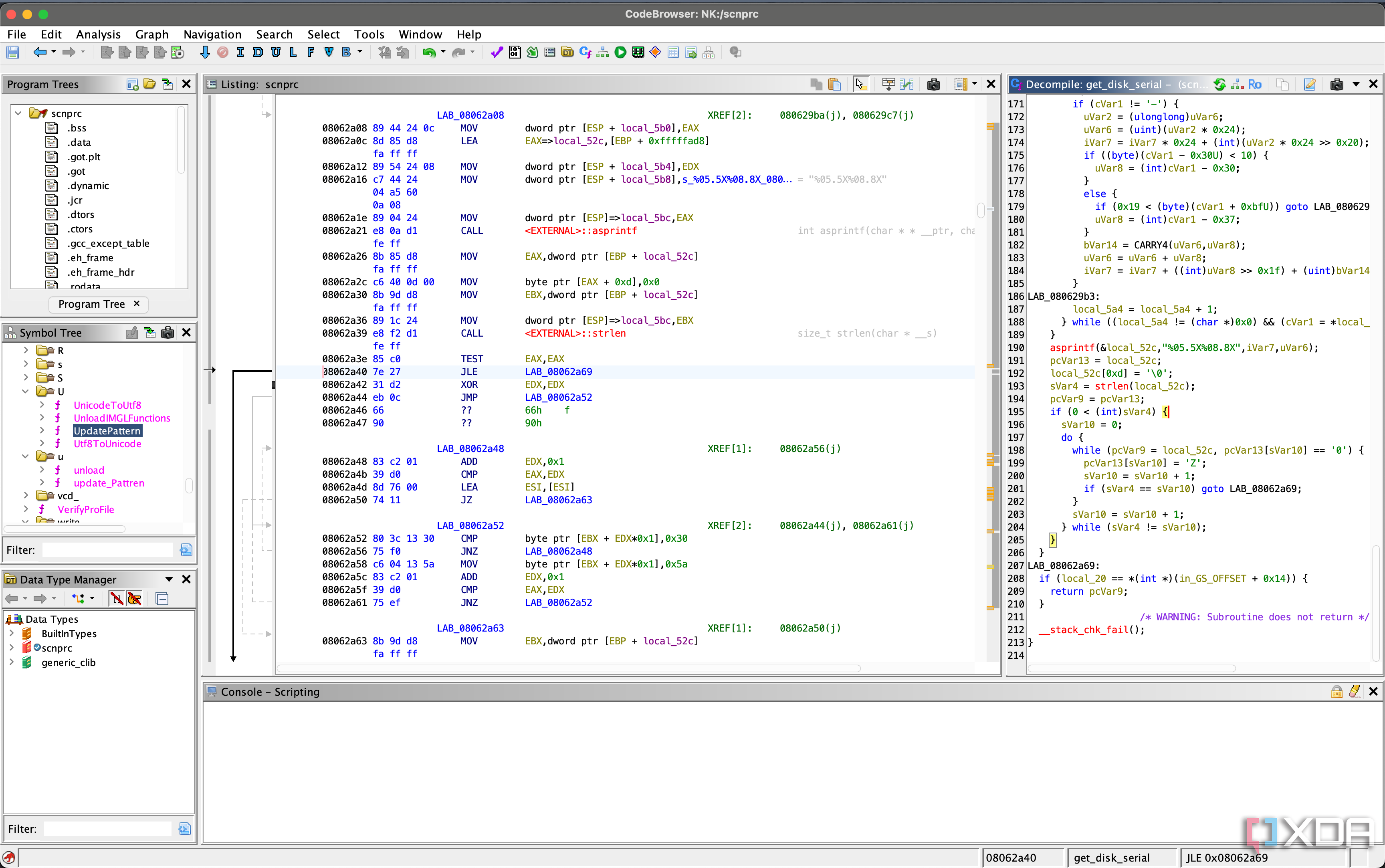
The file that appears to manage the watermarking for all of the other files involves get_disk_serial, and this file is pretty simple. It does the following:
- Grabs the st_dev major and minor of the root filesystem
- Makes a temporary block device on that disk
-
Tries to pull the drive serial with ioctl through one of three ways:
- Poll HDIO_GET_IDENTITY
- Poll SG_ATA_IDENTIFY with an IDENTIFY_DEVICE packet
- Tries again but with an IDENTIFY packet
- If this fails, pulls from gszConstSerial
- Strip response to 20 bytes converts to uppercase, removes "WD-W" if it exists (Western Digital ID)
- Any leading 0 characters are replaced with Z
This disk-serial appears to play a part in file watermarking. When images, documents, or videos are discovered, a watermark that identifies the computer that interacted with them is embedded in the file. With an image, this data is appended to the end of the file, whereas a Word document will see it inserted in null space towards the beginning of the file. For images, unique devices will all have their data appended to the end of them.
The above watermarking behavior that inserts directly into an existing file has already been described in the past with Red Star OS, but I discovered another, very interesting approach to watermarking that I hadn't seen documented anywhere else. The previously reported watermarking works, but can be easily identified by looking at the file in a hex editor. The function that I found, called WriteImageInformation, has a different approach. It hides a watermark string inside an RGB bitmap, adding a prefix of "WM" to the start of a character array. It then tweaks the high-frequency DCT coefficients of successive 8*8 byte blocks of the image, repeats that as many times as needed to cover the entire size of the image, and then writes the modified pixels back.
This approach needs the image to be of a minimum size, and like the other functions identified here, it's unclear if it's actually used in this version of the software. It exists, though, meaning that if it wasn't used before, it probably is now or has been iterated upon.
There's no reason to use Red Star OS
As tempting as it may sound

As tempting as it may sound, you should not install Red Star OS unless you know what you're doing. It's essentially spyware disguised as an operating system, but of course, that was to be expected. Not only that, but it's not even really usable in today's world. Firefox 3.5 is ancient, and websites that use HTTPS won't even allow you to visit them in the first place. There's no point in deploying it, and you're only opening yourself up to danger for no real reason by doing so.
Of course, one could argue that the operating system only phones home within the North Korean intranet, and you'd probably be right, but it's also just not worth it. It can be fun to spin up in a virtual machine, but I've seen people install it as a dual-booted operating system, not realizing that, at the very least, you're appending identifying data to all of the files made accessible to Red Star for no good reason.
There have been plenty of fascinating talks and investigations into Red Star OS 3, and I merely scratched the surface in my analysis here. I highly recommend having a look around if you want to learn more.
.png)











 English (US) ·
English (US) ·