
Sign in to your XDA account
Virtual Private Networks (VPNs) are often advertised as an all-in-one privacy solution, but this reputation has largely been built as a result of aggressive marketing by VPN providers. Companies like NordVPN, ExpressVPN, and Surfshark routinely promote their services with bold promises of total privacy and anonymity. In truth, a VPN is not a magic shield for all aspects of your digital life. It's important to know what they actually can and can't do, as otherwise, you may be lured into a false sense of security.
What a VPN can do is encrypt your internet traffic and route it through a server, hiding your real IP address. This can protect your data from local eavesdroppers and even your ISP, and prevents websites or services from seeing your home IP, which can reveal your geographic location. VPNs can also make it appear as if you’re browsing from another country, which is useful for bypassing certain geographic restrictions. That's about it for what a VPN can actually do.
In terms of what VPNs can't do, well, there's a lot. They don't stop other forms of tracking that don’t rely on your IP address, which, to be honest, isn't a particularly useful tracking metric these days. Advertisers, data brokers, and tech companies have many tools to identify and profile users, such as browser cookies, mobile device IDs, and browser fingerprinting, and these are far more effective at tracking users than IP addresses are. A VPN, by default, won’t block cookies or scripts embedded in websites that report your activity to third parties, and there are plenty of free tools and browser extensions that will, so even the VPNs that offer those capabilities aren't doing anything particularly special.
A VPN also won’t prevent your operating system or apps from sending telemetry data back to their developers’ servers, and using a VPN simply means that data travels through the VPN’s server. It still reaches the data collector in the end. Even when it comes to public Wi-Fi, pretty much everything uses HTTPS these days, meaning the traffic is encrypted, and anyone attempting to intercept that traffic won't be able to see the data you're sending. Even if an attacker tries to force their own certificate on devices using that public Wi-Fi (so that they can decrypt the traffic), your device simply won't trust that certificate and won't send the data. And for public Wi-Fi that still requires a password, all traffic is encrypted... even HTTP, though that's admittedly easier to intercept as there's no certificate to verify.
As a result, overblown claims in VPN advertisements have led users to overestimate what VPNs can do. According to one study from June 2024 from the University of Maryland and Carnegie Mellon University, those who consumed YouTube content that advertised VPNs had an "increased belief in hyperbolic threats advertised," and Consumer Reports found in 2021 that "12 out of 16 of the VPNs we looked at either inaccurately represented their products and technology, or made hyperbolic or overly broad claims about the kinds of protection they provide their users."
If a VPN won't protect you online, then what will? These are the things you can actually do to improve your security and better protect yourself on the internet, and they don't even need a VPN.
5 Use a privacy-focused browser
There are so many options out there

One of the most impactful changes you can make is to switch the browser you use and how you search the web. Web browsers and search engines are major sources of data collection. A conventional browser like Google Chrome is tightly integrated with Google’s services and tends to encourage data sharing. While previously I would have considered recommending Firefox here, Mozilla has been making some dubious moves when it comes to user privacy, with one stark change being an update to its FAQ on its website. Previously, it read:
The Firefox Browser is the only major browser backed by a not-for-profit that doesn’t sell your personal data to advertisers while helping you protect your personal information.
Yet, following a debacle where the terms of use were changed (before Mozilla rolled it back and insisted that it had just been boilerplate inserted), it now reads:
The Firefox Browser, the only major browser backed by a not-for-profit, helps you protect your personal information.
In other words, it seems as if Mozilla is no longer committed to not selling your personal data to advertisers. Not a great look for a privacy-focused browser. With that said, there are plenty of Firefox-based browsers that strip Mozilla-related telemetry out, such as Floorp, Zen Browser, and LibreWolf. These browsers prioritize user privacy by blocking trackers and minimizing telemetry. For example, browsers based on Firefox can use Enhanced Tracking Protection can automatically block known trackers and cookies that follow you site to site. Privacy-focused browsers have no or minimal telemetry (meaning they send little to no data back to the browser maker), and they enforce stricter defaults. In privacy-centric Firefox forks like LibreWolf, for example, no telemetry is enabled, and tracking protection is set to "Strict" by default, with cookies and history auto-cleared on close.
If you must use a common browser (such as Chrome or Safari), take time to adjust privacy settings. Turn off features that share data (like Chrome’s sync and prediction services). Block third-party cookies, or at least set your browser to clear cookies and site data regularly. You can enable the "Do Not Track" signal, but paradoxically, it can make you more fingerprintable, and there's no requirement for advertisement providers to abide by it. You can also consider enabling any built-in anti-tracking modes, such as Safari’s Intelligent Tracking Prevention, which tries to limit cross-site tracking.

Related
Brave Browser is the most overrated browser out there, and I don't recommend using it
When it comes to browsers, Brave is touted as one of the best when it comes to privacy, even though it shouldn't be.
4 Employ DNS filtering, encrypted DNS, and a home firewall
Most of these are pretty easy to do
Another powerful technical measure is to improve how your devices perform DNS lookups, which is how your device translates domain names to an IP address on the internet. These DNS requests can reveal what websites you’re visiting, and they often go to your internet provider’s DNS servers (or another third party) in plain text. In some cases, your DNS can "leak" even when using a VPN, meaning that those requests still go to your normal DNS provider (which may be your ISP) rather than through your VPN.
Encrypted DNS prevents your requests from leaking, and services like Cloudflare DNS (1.1.1.1), Quad9 (9.9.9.9), or NextDNS support encryption and have privacy-focused no-logging policies. Your DNS requests are then encrypted, and they can't be seen by others who may be on the same network, or even by your ISP.
You can even go a step further by using DNS filtering to block known trackers, ads, and malicious domains. I use a Pi-hole for this, running on a Proxmox host, but there are plenty of options out there that can enable that for you. Services like NextDNS or AdGuard DNS maintain blocklists of thousands of tracker and ad domains. When enabled, your device will simply fail to connect to any domain on those blacklists. This stops many ads and tracking scripts before they even load, and you can even import many of these blacklists into Pi-hole if you wish.
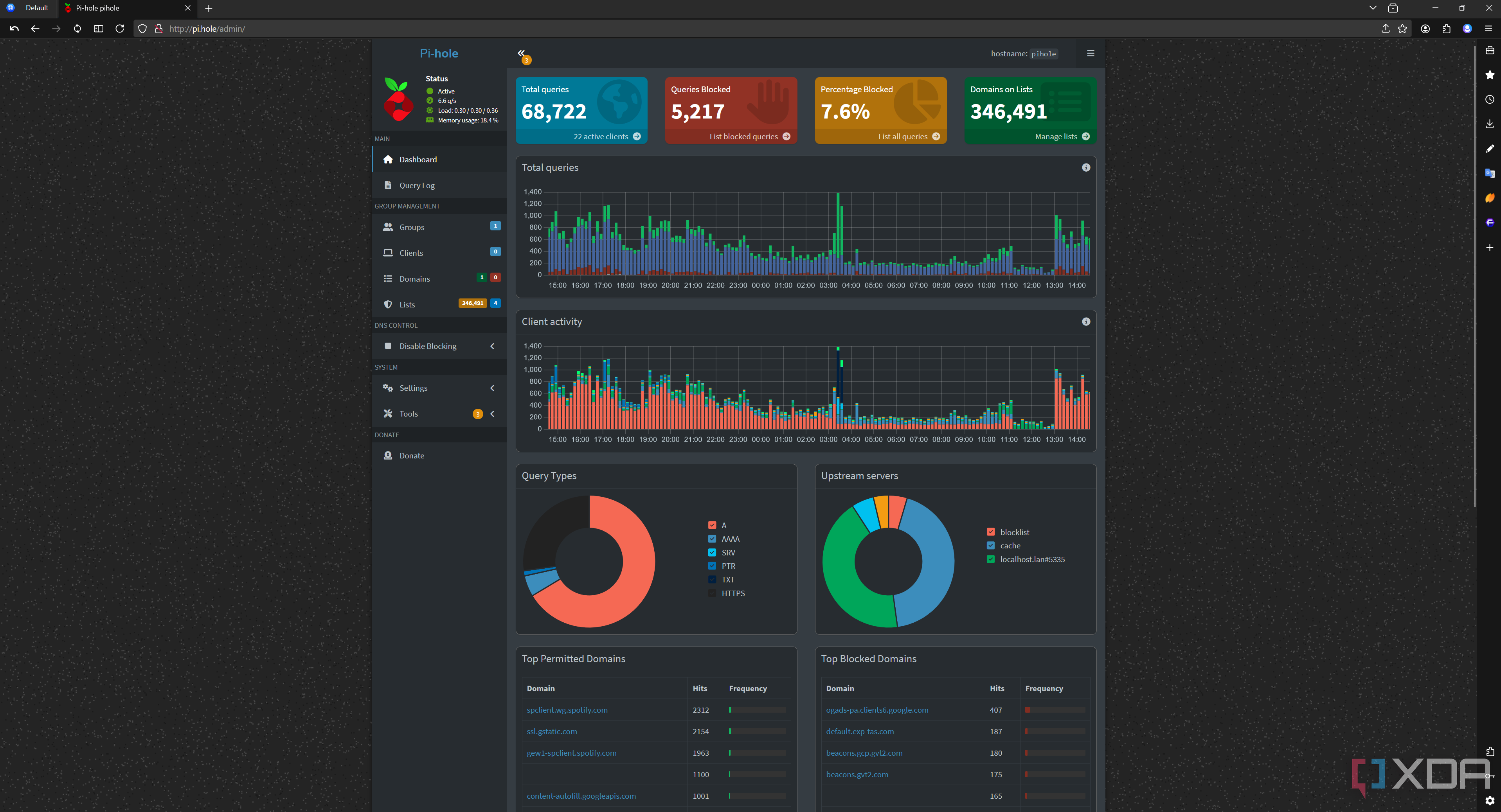
The beauty of a Pi-hole is that you can set your network's DNS to be the IP address of your Pi-hole, and even devices without a configurable DNS will still be prevented from connecting to trackers. You can even use it to create custom domain names. For example, you can see at the top of the above screenshot that I navigated to my Pi-hole simply via "http://pi.hole". It's pretty cool and a great way to organize self-hosted services, too.
Doubling down on this approach, you can even deploy a custom firewall using OPNsense or pfSense and tools such as Zenarmor and CrowdSec. These analyze your network traffic for threats and trackers, and can shut it down before it leaves your network. They're a bit more dynamic, too, identifying new threats that a Pi-hole may not necessarily pick up on. It's significantly more advanced and not for those who are new to networking, but it's something to look into if you want to really nail down your privacy in the future.
If you do use a VPN service, make sure it has DNS leak protection (most reputable VPN apps do). Alternatively, manually set your DNS to a secure provider outside of your ISP, so that even if not on VPN, you aren’t using the ISP’s default. Normally, regardless of a VPN, whoever runs your DNS (often your ISP) gets a full log of the domains you access. With encrypted, private DNS, that visibility is gone or shifted to a trusted party; with DNS filtering, many tracking and ad domains are blocked outright.
3 Harden device and privacy settings
Your OS has settings; use them
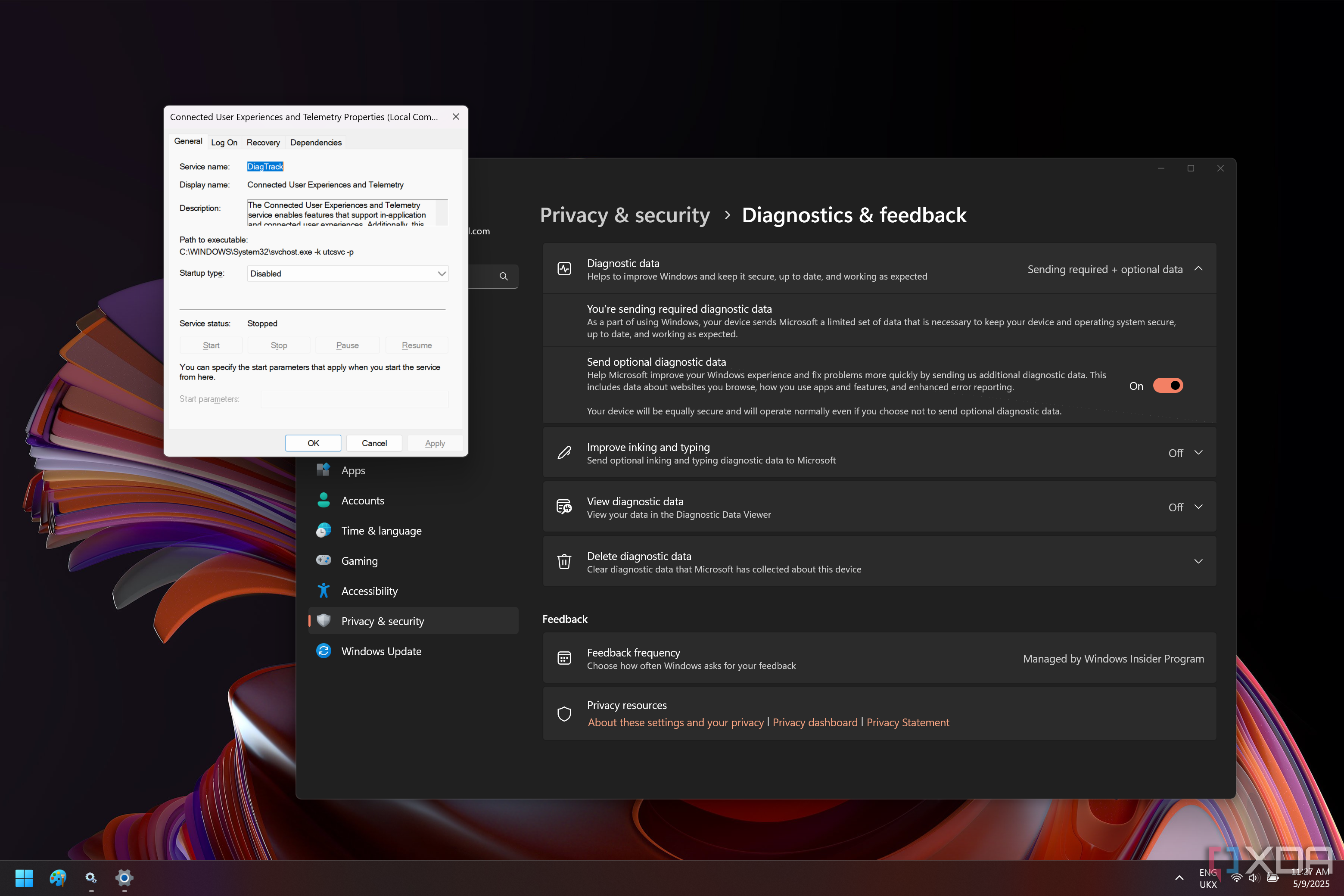
At the device level, there are numerous settings and precautions that can vastly improve your privacy to prevent the likes of Google, Apple, or Microsoft from collecting data from your smartphone, PC, or laptop. Out of the box, they may be configured to share a lot of data with the OS manufacturer or app developers. Taking control of this is important, as again, a VPN won't protect you; it will just change the route that your data takes before being collected in the end, anyway.
For example, Windows 11 has settings under Privacy where you can disable things like ad tracking ID, turning off diagnostic data, and debloating tools can allow you to turn off all telemetry entirely. Microsoft collects usage and diagnostics data by default, but you can opt out of a lot of it. Similarly, on macOS, you can disable sending analytics to Apple and limit what is shared in Spotlight or Siri suggestions. Every major OS has an array of privacy-centric toggles, and it's wise to go through them and see what you can disable.
On Android, devices with Android 12 and up allow you to permanently delete the advertising ID and give you the option to reset it frequently. On iPhones with iOS 14.5 and up, Apple’s App Tracking Transparency will prompt apps to ask permission to track; always choose "Ask App not to Track" so the app is barred from accessing your IDFA (Identifier for Advertisers). There are also privacy-focused operating systems for both PCs and Android smartphones, such as GrapheneOS or LineageOS installed without Google Play Services.
The bottom line is this: every smartphone and PC has toggles for privacy, so use them. A VPN won’t stop those flows of data, as it just encrypts them in transit to the data collector. However, you can shut it off at the source.
It's a multi-layered approach
Even with a privacy-friendly browser, it’s important to add additional layers of defense against web tracking. Advertisers and analytics companies employ a ton of techniques to follow users around the internet, including third-party scripts, tracking pixels, cookies, and browser fingerprinting. There are many specialized browser extensions that you can install and use for this purpose, and they're all free as well. These include:
- uBlock Origin: While many feel that this tool has been held at bay by Google with Manifest v3, the truth is that it's still incredibly powerful. Plus, if you use a Firefox-based browser, you can still get the full-fledged uBlock experience.
- Ghostery: Blocks third-party tracking scripts used for collecting data on user behavior, usually intended for advertising, marketing, and security.
Another tool you can use is EFF’s Privacy Badger, which is a lesser-known but still fantastic privacy-protecting tool. It learns as you browse, and if it sees the same third-party source trying to track you across multiple sites, it automatically blocks it. Privacy Badger also counters more insidious forms of tracking, like fingerprinting. Fingerprinting scripts gather bits of information such as your browser version, fonts, screen size, hardware details, and even "Do Not Track" settings, in order to create a unique "fingerprint" that can recognize you without cookies.
Some modern browsers and extensions try to reduce the effectiveness of fingerprinting by making your browser look less unique, with features like "Resist Fingerprinting." It makes your browser report more generic values, though, keep in mind that fingerprinting is complex and completely defeating it is hard without potentially dealing with usability problems across sites. Your browser is the front line of privacy defense, and a combination of built-in tools and powerful extensions will go significantly further than a VPN ever will in protecting your privacy.
1 Minimize your digital footprint and know how targeted advertising works
It's arguably scarier than your phone listening to you
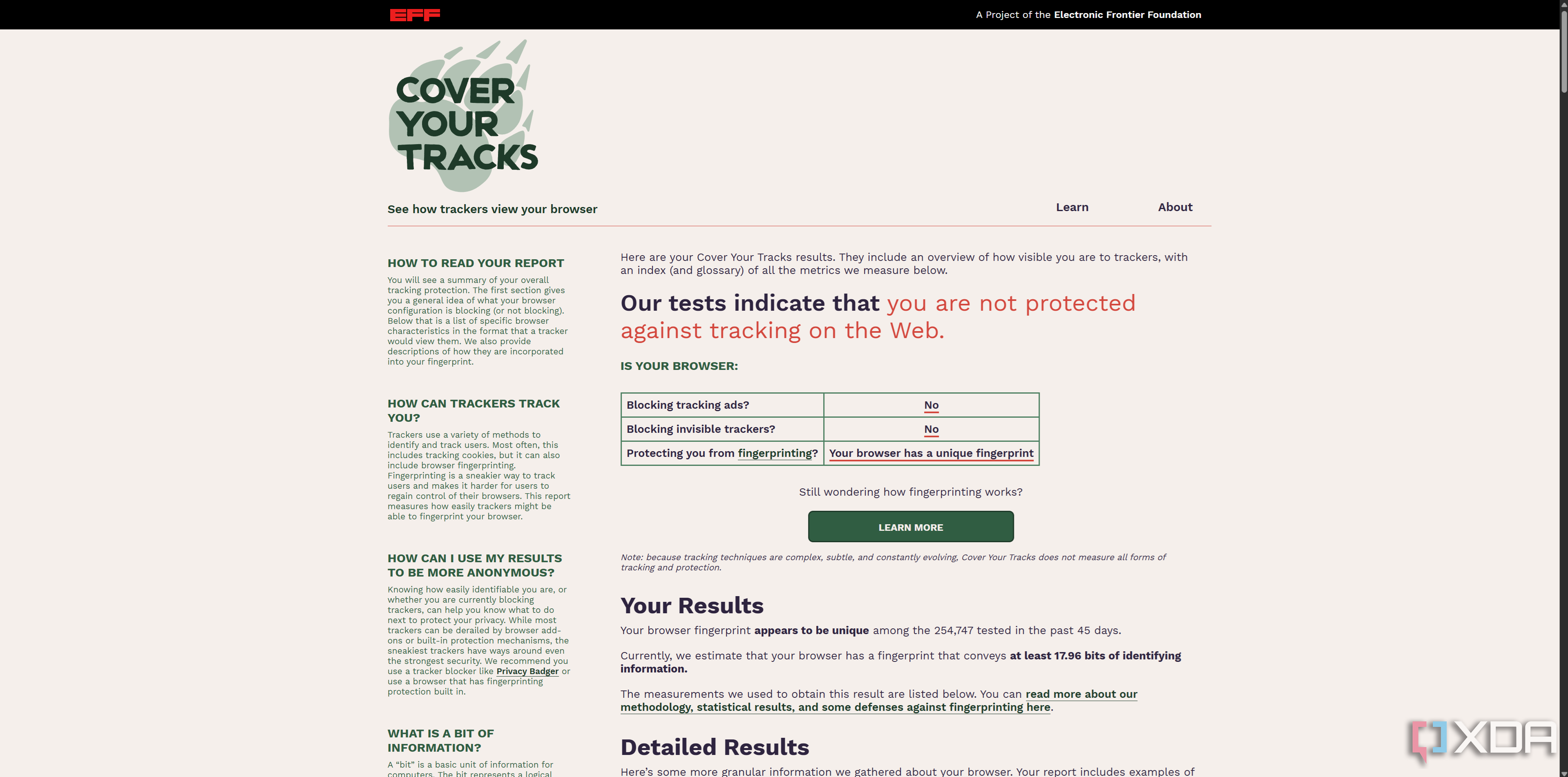
EFF's "Cover your Tracks" tool, using a stock Google Chrome installation
Last but certainly not least, consider your own behavior and habits online. Every piece of information you share, every account you create, and every device you use contributes to your digital footprint. While we've focused on technical protections that you can employ, in hacking contexts, social engineering vulnerabilities are just as much vulnerabilities in a system as a technical vulnerability is. What minimizing your digital footprint looks like is different for everyone, but in short, there are a few key concepts that everyone should employ where they can.
The usual warnings apply for social media, even if you lock down your profile. The companies running these platforms collect detailed data on your activities, which can include your preferences, friends, and activities. Think about all of those times when you were talking to someone about something specific, went on Facebook, and saw an advertisement for the product you talked about. Was Facebook listening? No, it wasn't (nor would that ever really be feasible), but it feels like that. The truth is actually scarier; Facebook knows the two of you were together based on the GPS data it collected, and the person you were talking to probably went and searched for that product where there was a Facebook tracking pixel.
Many advertising companies have built advanced algorithms that can group you with other users based on statistics, and those statistics are likely to be highly accurate. For example, one Irish report found that 90% of Irish people have one "cheat meal" a week, and 82% of 18-34 year olds ordered food as their "cheat meal". If you fall into this demographic, and you're talking to your housemate or family about ordering food on a Friday, the subsequent advertisement you see online showing a food delivery service isn't because your phone listened to you; it's that you were statistically likely to order food. It's a frequency illusion, known as the Baader-Meinhof phenomenon. You don't pay attention to all of the times that irrelevant advertisements are shown to you, but you do notice the ones that seem to get you perfectly, and that's arguably part of the strategy of advertising these days.
Moving on to online interactions in general, not every online interaction needs to be tied to your real identity. For forums, commenting, or services where being "you" isn't critical, consider using an alias. This isn’t about deception, as it's a completely valid way to separate your activities so that not everything is linked to one master profile of you. Similarly, when asked to fill out forms for things like newsletters, you don't always have to provide accurate extra details like your real birthdate or phone number. Only supply what's necessary. On that note, it's also good practice to periodically review and delete accounts you no longer use, especially because we accumulate online accounts on random websites over time. If you don’t need it anymore, reducing what exists out there reduces what can potentially leak or be harvested.
In adopting these behaviors and knowing how targeted advertising works, you can better protect yourself online. Knowing the tricks of the trade means that you can figure out how to avoid being tricked in the first place, and also makes you aware of where your data may be leaking to advertisers. Remember: every time you volunteer data about yourself, you're trusting that platform or service to handle it properly.
Protecting yourself online is important
No single tool or service is a silver bullet, not even that one VPN with flashy ads and a bunch of endorsements from your favorite YouTuber. That's not to disparage VPNs either; a VPN can be a useful component of your overall privacy strategy, but it only addresses a narrow set of threats. For the vast majority of privacy encroachments, you can protect yourself without ever using a VPN. True privacy comes from addressing network-level, device-level, and behavior-level exposures rather than trying to deal with them all through one service. At the network level, use encryption, at the device and application level, lock down the settings, and at the user behavior level, practice data discipline.
Each layer covers gaps that the others leave open, and you'll create overlapping safeguards that reinforce each other. You need to be proactive and intentional when it comes to security and data privacy, and this approach is exactly how security-conscious professionals protect their own data. As well all know, the internet poses serious privacy challenges, but you can tip the balance in your favor. A VPN alone won’t safeguard your privacy, but an informed and comprehensive strategy (that can include a VPN if you wish) most certainly will.
.png)











 English (US) ·
English (US) ·