When my smart home started out, it had only a few devices connected to the network, mostly from the same company, and it was fairly simple to manage. Over time, the number of devices grew substantially, to the point where I've got them all connected to a smart home hub running Home Assistant because I got tired of app-juggling.
But that didn't fix every single one of the slowdowns and other minor connectivity issues I'd been experiencing, things I'd written off as moving to a new home with differing dimensions, so I'd have to adjust after everything was plugged in. I'd read that IoT devices can be noisy on the network, so I decided to segment them onto a VLAN as I installed some new networking gear. And, you know what? Most of the issues disappeared once they had a separate 2.4GHz AP and VLAN to communicate on. I've still got a few things to iron out, but my home network is much better behaved, and now I want to add more VLANs for the other functional groups of devices in my home.
Related
I revived old smart home devices with Home Assistant - here's how it went
Here's how I used Home Assistant to blow a second life into my old smart home devices and manage them from a single view
Network segmentation made my smart home more secure
Isolating IoT devices on their own VLAN keeps them away from my precious data
While the security of IoT devices has improved lately, especially with changes like being prompted to change the default credentials when installing them, they're still not the best at staying secure. Why should they, when the hardware is relatively weak and often doesn't have much storage or computational power? The more I read about smart home devices, the less I want them on my home network, but they've got me hooked with convenience.
That doesn't mean I have to accept that my network will be less secure by default. Instead, I've moved them all onto a VLAN that only has other IoT devices on it, to keep them away from my private files and devices that benefit from lower-latency, bandwidth-heavy internet access.
Some of the main benefits to the overall security of my home network include:
- It isolates the vulnerable devices from my main network
- If a breach happens, it limits lateral movement
- Limits which devices can communicate with the network
- Keeps my private files away from the IoT network
And with Home Assistant to tie everything together, I don't even need my smart home devices to reach the internet, as they all talk to the HAOS server, which then talks to my smartphone and voice assistants. It's now much better in every way, apart from a little more effort on my part to get everything working correctly.
Plus, it's much easier to manage
Now I can set individual VLAN network policies and limit bandwidth use
Now that my IoT devices are on one VLAN, I can apply things like access control lists to ensure nothing else is added to that VLAN unless I approve it. Plus, I can assign firewall rules that only apply between that VLAN and the rest of my network and the internet so that I know what traffic is going where. The security packages on my router can get a better baseline for 'normal' network use so they can pick up on irregular or unauthorized traffic faster.
It's easier to manage overall. I can see all my IoT devices in one list, so I know which ones are taking up more bandwidth, which ones might be misbehaving, and so on.
And had an unintended benefit
Keeping all my IoT devices on a dedicated VLAN, with a dedicated 2.4GHz radio didn't just make my home network safer. It also made it faster, by shifting all those broadcast-packet-happy devices away from the devices I actively use and notice the slowdown, like my laptops, PC, and smartphone. That's because total bandwidth is consistently shared among the number of Wi-Fi-connected devices on a router, and the noisier the device, the more bandwidth it'll take up.
Plus, each band can only support so many concurrent devices, and the slow devices on the radio connection make it slower for everyone else. Putting the slow devices onto their radio means the fast devices that support 5GHz and 6GHz can work faster, as they're not slowed down by the IoT babble.
Related
I moved my Home Assistant from TrueNAS to a mini PC running Proxmox, and I'm so glad I did
I moved my Home Assistant from TrueNAS to Proxmox, and it's saving me energy, time, and it's just all around better.
Although it's a bit more work
Between port tagging and firewall rules I've got a few more tasks to do
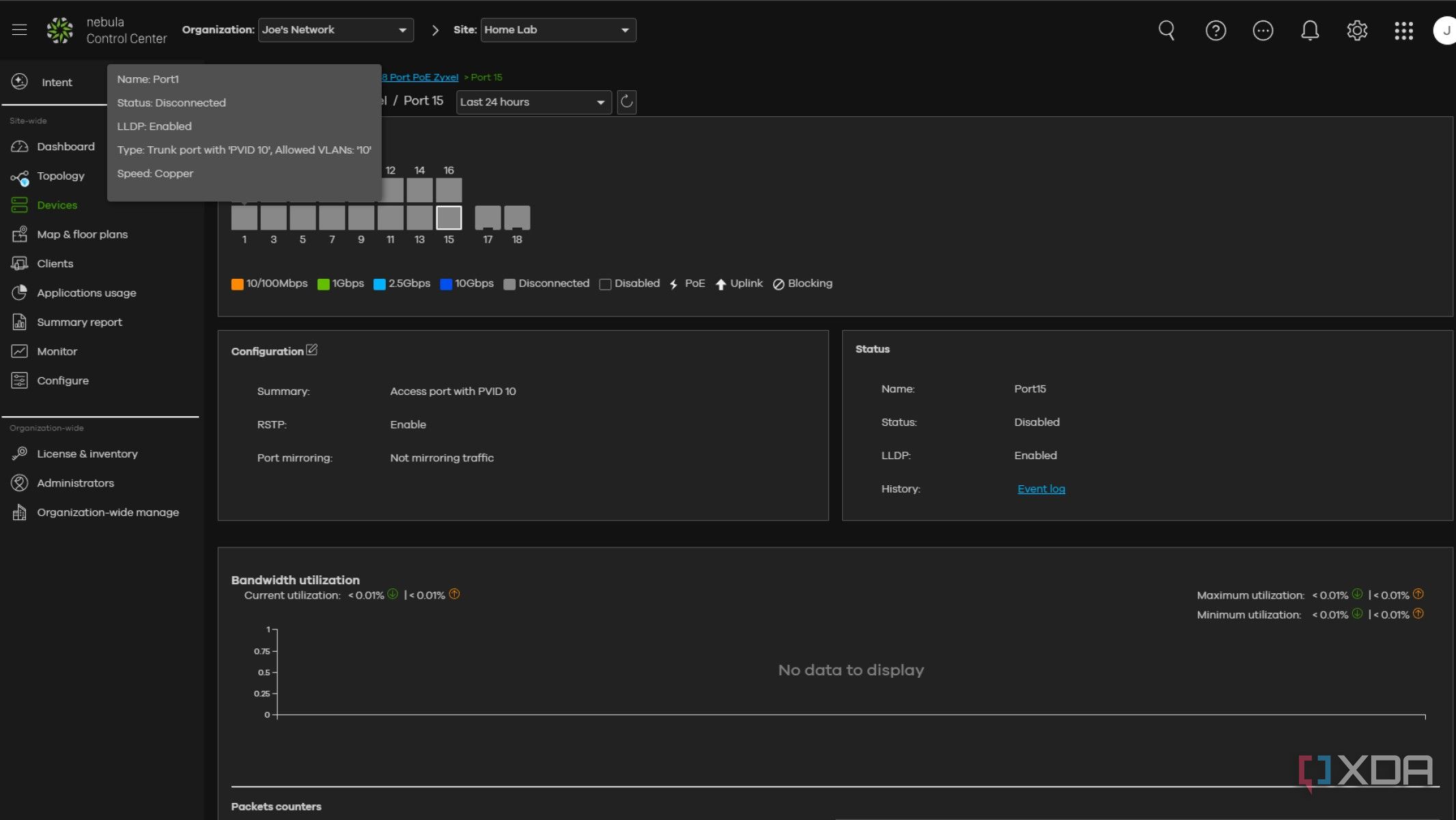
Setting up the VLANs, making sure each device is attached to the correct one, and adding firewall rules to limit connections between them is only part of the process. I also had to make sure each VLAN trunk port was set to specify which VLANs could travel through it because leaving them on ALL would have reduced the isolation between them. Inter-VLAN routing also got turned off, except for the firewalled connection, so that smartphone apps can handle IoT devices.
The firewall rules were set up so that the IoT devices couldn't talk to anything outside their VLAN unless queried first, and even then only the ports needed for those devices were set to allow traffic through from my home network. That way, it reduces the ability of anything spreading if something is compromised, keeping everything safer. It's always best to start from a position of restrictive rules and loosen them for specific uses.
Things like the phone apps to manage smart home devices also get their own firewall rules, with the MAC address of those devices allowed to communicate through the firewall. This does mean I have to turn off the MAC randomization feature on those phones, but I'm connected to my home network, so that's already limiting tracking by third parties.

Related
6 things you need to know before setting up VLANs on your home network
VLANs are super handy for organizing your network, but you need to do some prep work first
Putting my smart home on its own VLAN was the smart move
If you've got the hardware to do so, putting your IoT devices on their own network is highly beneficial. This could be accomplished by using the guest network on your router, in case it doesn't support multiple VLANs, which segregates those guest devices so they can't reach your private information. Plus, I have that VLAN on a 2.4GHz band that nothing else is connected to, keeping the 5GHz and 6GHz radios in my access points free for the devices that need more bandwidth, like my computers and phones.
.png)












 English (US) ·
English (US) ·