Maker, meme-r, and unabashed geek, Joe has been writing about technology since starting his career in 2018 at KnowTechie. He's covered everything from Apple to apps and crowdfunding and loves getting to the bottom of complicated topics. In that time, he's also written for SlashGear and numerous corporate clients before finding his home at XDA in the spring of 2023.
He was the kid who took apart every toy to see how it worked, even if it didn't exactly go back together afterward. That's given him a solid background for explaining how complex systems work together, and he promises he's gotten better at the putting things back together stage since then.
As your home network needs grow, you might consider network segmentation to make it more manageable and keep things safer. If you are, you're on the right track toward having a more resililiant network, where ease of use is balanced with security and other needs. The most common way to achieve this is through using VLANs, but that isn't the only way to get the network segmentation you want, and it might not be the best way for your particular network setup.
Software-based solutions
Whether it's firewall rules or software-defined mesh networking, you can achieve your goal
To get the defense-in-depth strategy of network segmentation in place without using VLANs, you've got plenty of software options that will depend on how complex your networking needs are. You could handle it all from one managed switch or router that supports Access Control Lists (ACLs) if you wanted to. These are usually set up using the MAC or IP addresses of individual clients, and you can block or allow their passage through the switch, or if you're setting up the ACLs on a NAS, you can set granular controls over which folders and services those IP addresses can access.
A slightly more complex setup could use firewalls between each network segment, with ACLs and firewall rules to allow traffic between network segments, or to allow or deny traffic based on the protocols used. Protocol-based controls can be a powerful tool to set up access between specific devices and network segments without using VLANs. Still, many commonly used services use the same few protocols, which limits their overall usefulness.
When setting this up, it's important to set up allow rules before restrictive blocking rules, as most firewalls work from a first-match principle. One such inter-subnet block rule would consist of an alias containing all RFC 1918 private network ranges (10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16), disallowing them to communicate except for essential services like DNS resolution to the firewall's IP address. Or you could set up zone-based firewall rules, eg: internal, DMZ, external, and set up rules to control traffic flow between the zones.
Be careful when changing firewall rules, as any mistake could lock you out, or override the carefully crafted deny rules. It's always best to set up a rule set to bypass any potential lockouts before you start.
Software-defined mesh networking
Networking tools have become ever more sophisticated in recent years, and the rise of software-defined networking has made it possible for you to set up network segments easily. Virtual mesh networks like ZeroTier and Tailscale can be used for ACLs and network segmentation. ZeroTier has an advantage as it works on Layer 2, so you can use broadcast traffic, multicast, and ARP resolution. Most of these types of tools start from a Zero Trust principle, so newly added devices are already segmented, and then you can allow the things you want them to be able to access.
-
 Credit: Source: ZeroTier
Credit: Source: ZeroTier -

-
 Credit: Source: Fossorial
Credit: Source: Fossorial
Hardware-based options for network segmentation
Advanced hardware brings microsegmentation, or you can use multiple network devices to achieve the same thing
Many consumer routers have microsegmentation built in, hiding under the Parental Controls section. This lets you create user profiles, group the devices they're allowed to use together, and control how those devices can access other services or the internet. You could set up an old router as a network segment, and use the power of the firewall on that router to keep traffic you don't want off of it. Or with multiple routers, you could set up a segmented mesh network of sorts, assign devices to the individual APs, and set up some rules for how they can communicate.
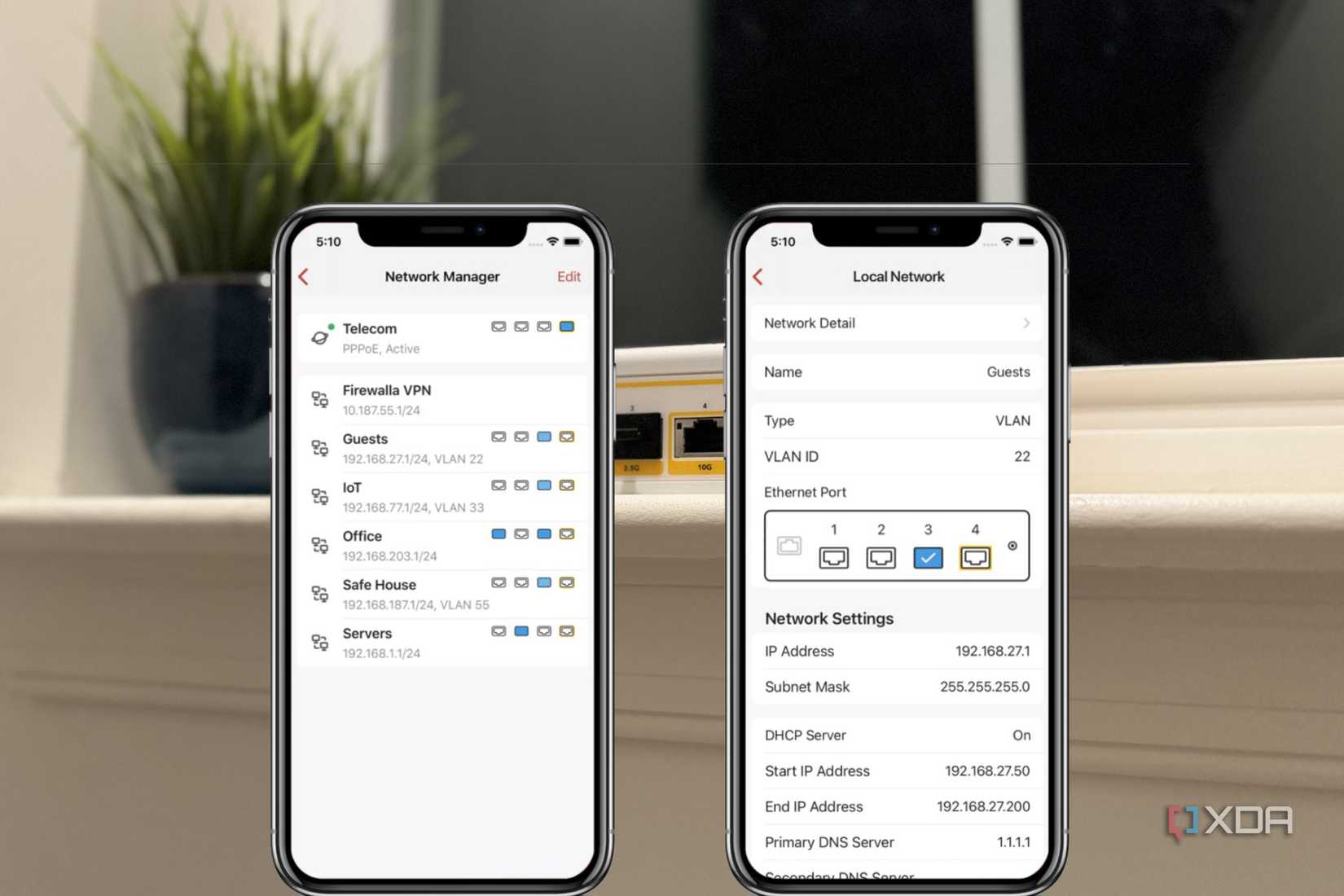
Newer and more advanced networking appliances like my beloved Firewalla and its access points can set up segmentation based on individual router ports, VqLANs (Layer 2 segmentation based on access control lists) for device groups, users for even more granular microsegmentation, and more. Networking in this way starts with a principle of Zero Trust, and that's the best way to do things on your home network. It's more flexible and powerful than VLANs on their own, and makes managing complicated inter-device communications a breeze.
Network segmentation doesn't have to be done via VLANs
As networking gets more virtualized and software-defined, the old ways of network segmentation are no longer the only way to do things. In reality, a combination of every method mentioned here, including VLANs, would be how things would be set up, to give the most layers of security while making things easy to manage from the admin's point of view. Security is only as good as the amount of effort people are willing to put into setting it up, and the easier network segmentation can be made, the better.
.png)












 English (US) ·
English (US) ·